CCNP Secure FAQ: Implementing and Configuring IOS Intrusion Prevention System (IPS) Figure: Configuration Scenario Q1. What types of security controls are capable of monitoring traffic to detect problems in the network? a. Intrusion prevention systems (IPS) b. Protocol analyzers c. Intrusion detection systems (IDS) d. Security policy Answer: C Q2. What security … [Read more...]
CCNP Secure FAQ 802.1X and Cisco Identity-Based Networking Services (IBNS)
CCNP Secure FAQ 802.1X and Cisco Identity-Based Networking Services (IBNS) Q1. Which of the following is a framework defined by the IEEE 802.1 working group that provides a standard link layer protocol for port-based access control and authentication? A. 802.1q B. 802.11b C. 802.1x D. 802.1w Answer: C Q2. What are the three roles the IEEE 802.1x framework defines in the … [Read more...]
CCNP Secure FAQ Network Security Threats
CCNP Secure FAQ Network Security Threats Q1. A good rule of thumb for “strong” passwords is that they follow which of the following guidelines? A. Should be uppercase and lowercase, numbers, and special characters B. Should be complex and documented someplace C. Should be common words all strung together D. Should be documented so that you can reference them E. All of … [Read more...]
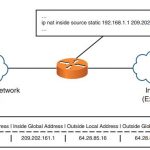
CCNP Secure FAQ Implementing and Configuring Network Address Translation (NAT)
CCNP Secure FAQ Implementing and Configuring Network Address Translation (NAT) Q1. Which of the following are potential limitations of using NAT? A. Embedding address complications B. Private address support complications C. Logging complications D. Overlapping address complications Answer: A and C Q2. Which of the following are valid NAT interface types? A. Inside B. … [Read more...]
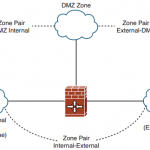
CCNP Secure FAQ: Implementing and Configuring Zone-Based Policy Firewalls
CCNP Secure FAQ: Implementing and Configuring Zone-Based Policy Firewalls Q1. The Context-Based Access Control (CBAC) applies policies using which of the following? a. inspect statements b. cbac-policy statements c. ACLs on interfaces d. ACLs on zones Answer: A and C Q2. ZBPFW applies using which of the following? a. MQC b. AIC c. ACLs d. C3PL Answer: D Q3. … [Read more...]
CCNP Secure FAQ Implementing and Configuring Cisco IOS Management Plane Security
CCNP Secure FAQ Implementing and Configuring Cisco IOS Management Plane Security Q1. Which type of management plane attack type works by creating or taking over a management session? A. Slow-path denial of service B. Management session spoofing C. Man-in-the-middle attacks D. DoS session spoofing Answer: B Q2. Which of the following type of password is used to secure … [Read more...]
CCNP Secure FAQ Implementing and Configuring Cisco IOS Control Plane Security
CCNP Secure FAQ Implementing and Configuring Cisco IOS Control Plane Security Q1. The central processing unit of each device is tasked to not do which of these? A. Process fast-path data plane traffic B. Process control plane traffic C. Process management plane traffic D. Process slow-path data plane traffic Answer: A Q2. The route processor is divided into which of the … [Read more...]
CCNP Secure FAQ Implementing and Configuring Cisco IOS Routed Data Plane Security
CCNP Secure FAQ Implementing and Configuring Cisco IOS Routed Data Plane Security Q1. Which of the following are some of the most common types of routed data plane attacks? A. Routing protocol spoofing B. Slow-path denial of service C. STP spoofing D. Traffic flooding Answer: B and D Q2. Which of the following ACL ranges are used for standard access lists? A. … [Read more...]
CCNP Secure FAQ: Introduction to Cisco IOS Site-to-Site Security Solutions
CCNP Secure FAQ: Introduction to Cisco IOS Site-to-Site Security Solutions Q1. Which network topology is in use when two sites interconnect using a secure VPN using point-to-point connectivity? a. Hub-and-spoke network b. Partially meshed network c. Individual point-to-point VPN connection d. Fully meshed network e. Star topology network Answer: C Q2. Which network … [Read more...]
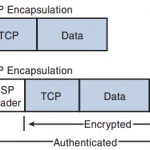
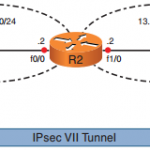
CCNP Secure FAQ: Deploying VTI-Based Site-to-Site IPsec VPNs
CCNP Secure FAQ: Deploying VTI-Based Site-to-Site IPsec VPNs Q1. The line protocol of a virtual tunnel interface depends on the state of which of the following? a. Physical interface b. Routing table c. VPN tunnel d. Peer’s VPN tunnel e. Crypto map Answer: C Q2. The encapsulation on a virtual tunnel interface must be which of the following? a. Frame Relay b. ATM c. … [Read more...]