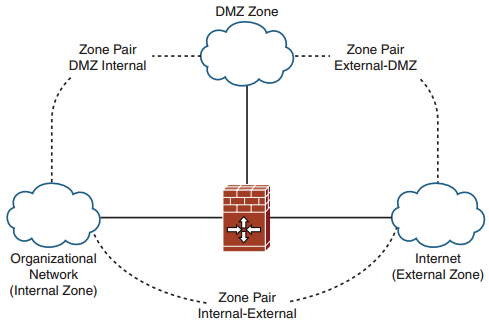
CCNP Secure FAQ: Implementing and Configuring Zone-Based Policy Firewalls
Q1. The Context-Based Access Control (CBAC) applies policies using which of the following?
a. inspect statements
b. cbac-policy statements
c. ACLs on interfaces
d. ACLs on zones
Q2. ZBPFW applies using which of the following?
a. MQC
b. AIC
c. ACLs
d. C3PL
Q3. Traffic between zones is only permitted when?
a. A zone pair is configured.
b. The zone is configured.
c. The zone is assigned to an interface.
d. The ZBPFW feature is enabled.
Q4. Traffic that is sourced and destined within the same zone can be configured when using at least which IOS version?
a. 12.4.24T
b. 15.1.0M
c. 15.0.1M
d. 12.3.10
Q5. A parameter map is applied inside which of the following?
a. Class map
b. Service map
c. Interface
d. Policy map
Q6. Which of the following are valid methods for matching traffic with a class map?
a. match-all
b. match-same
c. match-any
d. match-none
Q7. Which of the following are valid inspect policy map actions?
a. police
b. ignore
c. inspect
d. deny
Q8. To configure the ZBPFW for management and control plane traffic, which of the following zones is used?
a. Manage
b. Self
c. Router
d. Entity
Q9. Which of the following are supported AIC protocols?
a. AOL Instant Messenger
b. TFTP
c. MGCP
d. H.323
Q10. Which of the following parameter map types is used along with HTTP inspection?
a. GLOB
b. Shell
c. regex
d. inspect
1. A firewall is used to enforce an access policy between _____.
2. In IOS versions before 15.0.1M, intrazone traffic was _____ by default.
3. Traffic policy is applied _____ between zones using zone pairs.
4. Zone pairs can be set up to protect the control and management planes by using the _____.
5. The PAM feature is used to map _____ onto _____.
6. With Layer 3/4 traffic, the class map type is always the _____.
7. When using the inspect type policy map, the creation of a parameter map is _____.
8. If no zone pair is defined, traffic will _____ between zones.
9. The URL filter feature provides the ability to _____, _____, or ___ the traffic whose URL matches the configured characteristics.
More Resources