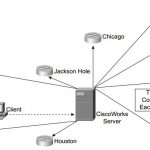
CCSP SECUR FAQ : Scaling Management of an Enterprise VPN Environment Q1. Which of the following is not supported by CiscoWorks 2000? A. Management and monitoring of PIX firewalls B. Management and monitoring of the CSIDS C. Management and monitoring of Cisco HIDS D. Management and monitoring of syslog servers E. Web-based interface for the configuration, … [Read more...]
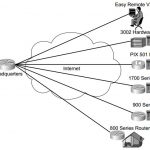
CCSP SECUR FAQ : Configuring Remote Access Using Easy VPN
CCSP SECUR FAQ : Configuring Remote Access Using Easy VPN Q1. What version of Cisco IOS Software supports Easy VPN Server? A. 12.1(13) B. 12.2(8)T C. 12.5 D. 12.0(8)J E. None of the above Answer: B Q2. What device does not support Easy VPN client? A. Cisco 800 Series router B. Cisco 3002 hardware VPN client C. Cisco PIX 535 Firewall D. Cisco PIX 501 Firewall E. … [Read more...]
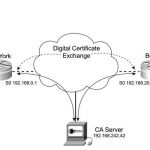
CCSP SECUR FAQ : Scaling a VPN Using IPSec with a Certificate Authority
CCSP SECUR FAQ : Scaling a VPN Using IPSec with a Certificate Authority Q1. What is the primary advantage of creating IPSec VPNs using CA support? A. They are easy to configure. B. They are easy to manage. C. They cannot be interrupted. D. Microsoft makes a CA product. E. None of the above. Answer: B Q2. Which is not a supported X.509 CA product? A. VeriSign OnSite … [Read more...]
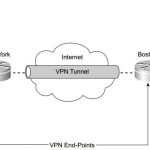
CCSP SECUR FAQ : Building a VPN Using IPSec
CCSP SECUR FAQ : Building a VPN Using IPSec Q1. What is the purpose of the intranet VPN? A. For dialup users to access the intranet B. For business partners to trade data C. To securely interconnect business locations D. To allow access to the intranet server E. None of the above Answer: C Q2. What should you be most aware of when using the debug crypto isakmp … [Read more...]
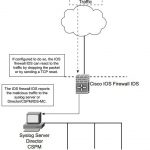
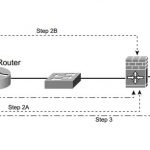
CCSP SECUR FAQ : Intrusion Detection and the Cisco IOS Firewall
CCSP SECUR FAQ : Intrusion Detection and the Cisco IOS Firewall Q1. What advantages does the Cisco IOS firewall IDS provide security administrators? (Choose two.) A. Detect malicious activity B. Combine features of routing and switching C. Work well with syslog servers D. Can respond to potential threats E. None of the above Answer: A, D Q2. The Cisco IOS firewall IDS … [Read more...]
CCSP SECUR FAQ : Authentication Proxy and the Cisco IOS Firewall
CCSP SECUR FAQ : Authentication Proxy and the Cisco IOS Firewall Q1. Authentication proxy enables administrators to restrict access to resources . A. by IP address of the source. B. by the IP address of the destination. C. on a per-user basis. D. by limiting groups to a specific resource. E. on a cache-limit basis. Answer: C Q2. Authentication proxy is not a transparent … [Read more...]
CCSP SECUR FAQ : Context-Based Access Control (CBAC)
CCSP SECUR FAQ : Context-Based Access Control (CBAC) Q1. Which of the following is not about a content-based access control? A. CBAC provides secure per-application access control across network perimeters. B. CBAC intelligently filters TCP and UDP packets based on application layer protocol session information. C. The CBAC feature is only available on Cisco … [Read more...]
CCSP SECUR FAQ : The Cisco IOS Firewall
CCSP SECUR FAQ : The Cisco IOS Firewall Q1. The Cisco IOS firewall feature set is usually configured on a what? A. Firewall B. PIX C. Router D. Switch Answer: C Q2. Which of the following places would be the appropriate position to place your IOS firewall? A. Between subnetworks. B. Between the internal network and an external network such as the Internet. C. There is … [Read more...]
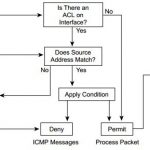
CCSP SECUR FAQ : Access Lists
CCSP SECUR FAQ : Access Lists Q1. What is an access control list (ACL)? A. An ACL is a method of only permitting IPX traffic. B. ACLs are rules that deny or permit packets coming in to or out of a router’s interface. C. ACLs are used only on switches. D. ACLs are rules to prevent mail traffic from leaving a router interface only. Answer: B Q2. Which of the … [Read more...]
CCSP SECUR FAQ : Securing the Network with a Cisco Router
CCSP SECUR FAQ : Securing the Network with a Cisco Router Q1. Which of the following versions of SNMP does Cisco IOS Software support? A. SNMPv1 B. SNMPv2 C. SNMPv3 D. SNMPv4 Answer: A, B, C Q2. Which of the following is (are) true about SNMP version 1? A. Very secure B. Used very widely C. Uses a very weak authentication scheme based on “community string” D. All of … [Read more...]