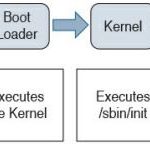
CCNA Cyber Ops FAQ: Forensics Q1. Which of the following are the three broad categories of cybersecurity investigations? A. Public, private, and individual investigations B. Judiciary, private, and individual investigations C. Public, private, and corporate investigations D. Government, corporate, and private investigations Answer: A. The three broad categories of … [Read more...]
CCNA Cyber Ops FAQ: Threat Analysis
CCNA Cyber Ops FAQ: Threat Analysis Q1. You must have adequate control mechanisms in order to enforce and ensure that data is only accessed by the individuals who should be allowed to access it and nobody else. Which of the following techniques can be used to prevent any attacks that could impact confidentiality? A. Secure routing protocols B. Network scanners C. … [Read more...]
CCNA Cyber Ops FAQ: Compliance Frameworks
CCNA Cyber Ops FAQ: Compliance Frameworks Q1. PCI DSS is designed to ensure which of the following? A. Protect electronic health care information B. Protect financial data such as the PAN, account data on a magnetic strip, and data on embedded chips C. Prevent data loss D. Prevent corporate fraud Answer: B. PCI DSS is designed to protect financial transactions, meaning … [Read more...]
CCNA Cyber Ops FAQ: Incident Response Teams
CCNA Cyber Ops FAQ: Incident Response Teams Q1. Which of the following are examples of some of the responsibilities of a corporate CSIRT and the policies it helps create? (Select all that apply.) A. Scanning vendor customer networks B. Incident classification and handling C. Information classification and protection D. Information dissemination E. Record retentions and … [Read more...]
CCNA Cyber Ops FAQ: Introduction to Incident Response and the Incident Handling Process
CCNA Cyber Ops FAQ: Introduction to Incident Response and the Incident Handling Process Q1. What NIST special publication covers the incident response process? A. Special Publication 800-61 B. Judiciary, private, and individual investigations C. Public, private, and corporate investigations D. Government, corporate, and private investigations Answer: A. NIST’s Special … [Read more...]
CCNA Cyber Ops FAQ: NetFlow for Cybersecurity
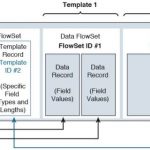
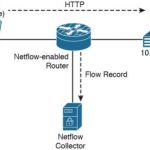
CCNA Cyber Ops FAQ: NetFlow for Cybersecurity Q1. Which of the following are some common uses of NetFlow? (Choose three.) A. To see what is actually happening across the entire network B. To identify DoS attacks C. To quickly identify compromised endpoints and network infrastructure devices D. To perform network scans to detect vulnerabilities Answer: A, B, and C. … [Read more...]
CCNA Cyber Ops FAQ: Fundamentals of Intrusion Analysis
CCNA Cyber Ops FAQ: Fundamentals of Intrusion Analysis Q1. Source and destination IP addresses are usually shown in NetFlow records and security events. What other artifacts are part of NetFlow records? (Select all that apply.) A. Destination ports B. Usernames C. Signature IDs D. Source ports Answer: A and D. Source and destination IP addresses, along with source and … [Read more...]
CCNA Cyber Ops FAQ: Introduction to Virtual Private Networks (VPNs)
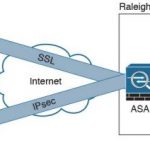
CCNA Cyber Ops FAQ: Introduction to Virtual Private Networks (VPNs) Q1. Which of the following are examples of protocols used for VPN implementations? A. TCP B. Secure Sockets Layer (SSL) C. UDP D. Multiprotocol Label Switching (MPLS) E. Internet Protocol Security (IPsec) Answer: B, D, E. MPLS, IPsec, SSL, PPTP, and GRE are examples of protocols used for VPN … [Read more...]
CCNA Cyber Ops FAQ: Fundamentals of Cryptography and Public Key Infrastructure (PKI)
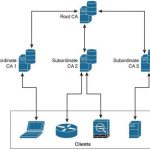
CCNA Cyber Ops FAQ: Fundamentals of Cryptography and Public Key Infrastructure (PKI) Q1. Which of the following are examples of common methods used by ciphers? A. Transposition B. Substitution C. Polyalphabetic D. Polynomial Answer: A, B, C. Common methods that ciphers use include substitution, polyalphabetic, and transposition. Q2. Which of the following are examples … [Read more...]
CCNA Cyber Ops FAQ: Network Security Devices and Cloud Services
CCNA Cyber Ops FAQ: Network Security Devices and Cloud Services Q1. Which of the following are examples of network security devices that have been invented throughout the years to enforce policy and maintain network visibility? A. Routers B. Firewalls C. Traditional and next-generation intrusion prevention systems (IPSs) D. Anomaly detection systems E. Cisco Prime … [Read more...]