This article provides information on how to simultaneously connect one user from different locations to the same SRX device by using multiple Junos Pulse connections.
Currently, Junos Pulse does not have the support for allowing multiple connections from the same user.
When a user tries to logon by using his/her credentials via Junos Pulse, SRX allows the connection. But when that user tries to establish a second connection, when the first connection is still present, it drops both connections or drops the first connection and connects the second one. But a concurrent connection does not work, as this feature is not yet supported.
Currently SRX does not support two connections from the same user via only one IKE gateway. You have to create two different gateways and then tie the lab user to each IKE gateway.
SRX configuration:
1. Create the access profile for the lab user:
[edit]
root@FSB-BYRON-SRX210# show access | display set
set access profile dyn-vpn-access-profile client lab firewall-user password "$9$ZfDH.QF/0BEP5BEcyW8ZUjHP5"
set access firewall-authentication web-authentication default-profile dyn-vpn-access-profile
2. Create two separate IKE gateways and tie the lab user to each gateway:
[edit]
root@FSB-BYRON-SRX210# show security ike | display set
set security ike policy ike-dyn-vpn-policy mode aggressive
set security ike policy ike-dyn-vpn-policy proposal-set standard
set security ike policy ike-dyn-vpn-policy pre-shared-key ascii-text "$9$XfJNVYJGifT3goT369OBxNd"
set security ike gateway dyn-vpn-local-gateway-1 ike-policy ike-dyn-vpn-policy
set security ike gateway dyn-vpn-local-gateway-1 dynamic hostname dynvpn < Notice the hostname here
set security ike gateway dyn-vpn-local-gateway-1 dynamic connections-limit 10
set security ike gateway dyn-vpn-local-gateway-1 dynamic ike-user-type group-ike-id
set security ike gateway dyn-vpn-local-gateway-1 external-interface fe-0/0/4.0
set security ike gateway dyn-vpn-local-gateway-1 xauth access-profile dyn-vpn-access-profile
set security ike gateway dyn-vpn-local-gateway-2 ike-policy ike-dyn-vpn-policy
set security ike gateway dyn-vpn-local-gateway-2 dynamic hostname test1 < Notice the new hostname here
set security ike gateway dyn-vpn-local-gateway-2 dynamic connections-limit 10
set security ike gateway dyn-vpn-local-gateway-2 dynamic ike-user-type group-ike-id
set security ike gateway dyn-vpn-local-gateway-2 external-interface fe-0/0/4.0
set security ike gateway dyn-vpn-local-gateway-2 xauth access-profile dyn-vpn-access-profile
3. Create two separate IPsec VPNs and tie each of them to the separate IKE gateways that were created in Step 1:
[edit]
root@FSB-BYRON-SRX210# show security ipsec | display set
set security ipsec policy ipsec-dyn-vpn-policy proposal-set standard
set security ipsec vpn dyn-vpn ike gateway dyn-vpn-local-gateway-1
set security ipsec vpn dyn-vpn ike ipsec-policy ipsec-dyn-vpn-policy
set security ipsec vpn dyn-vpn-2 ike gateway dyn-vpn-local-gateway-2
set security ipsec vpn dyn-vpn-2 ike ipsec-policy ipsec-dyn-vpn-policy
4. Define the clients under the dynamic VPN stanza:
root@FSB-BYRON-SRX210# show | display set | match dynamic
set security dynamic-vpn access-profile dyn-vpn-access-profile
set security dynamic-vpn clients client1 remote-protected-resources 10.0.0.0/8
set security dynamic-vpn clients client1 remote-exceptions 0.0.0.0/0
set security dynamic-vpn clients client1 ipsec-vpn dyn-vpn
set security dynamic-vpn clients client1 user lab
set security dynamic-vpn clients client2 remote-protected-resources 10.0.0.0/8
set security dynamic-vpn clients client2 remote-exceptions 0.0.0.0/0
set security dynamic-vpn clients client2 ipsec-vpn dyn-vpn-2
set security dynamic-vpn clients client2 user lab
Junos Pulse configuration:
- Logon to the PC and start the Junos Pulse client.
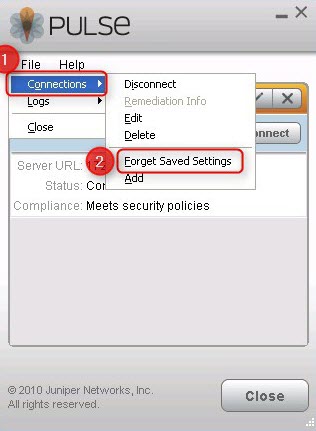
- Go to File > Connections > Forget Saved Settings.
- Create the connection by clicking the + symbol.
- Type the SRX URL (that is IP address).
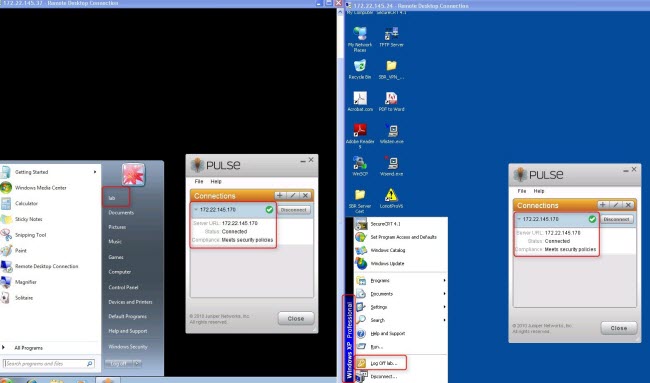
- Click Connect. You will be prompted for the username and password twice. When the credentials are provided twice, it will connect.
- Repeat the process from a different PC by using the same user credentials.
Verification:
[edit]
root@FSB-BYRON-SRX210# show security policies | display set
set security policies default-policy permit-all
[edit]
root@FSB-BYRON-SRX210# run show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
7495974 UP 71b277f5871bb686 98ede9dceafd0b09 Aggressive 172.22.145.24
7495973 UP 48376a740ce5963e 949e8f6c0e766514 Aggressive 172.22.145.37
[edit]
root@FSB-BYRON-SRX210# run show security ipsec security-associations
Total active tunnels: 2
ID Algorithm SPI Life:sec/kb Mon vsys Port Gateway
<133955591 ESP:aes-128/sha1 58141aba 3488/ 500000 - root 500 172.22.145.24
>133955591 ESP:aes-128/sha1 59e130c2 3488/ 500000 - root 500 172.22.145.24
<133955592 ESP:aes-128/sha1 d154504d 3482/ 500000 - root 500 172.22.145.37
>133955592 ESP:aes-128/sha1 b53cfd86 3482/ 500000 - root 500 172.22.145.37
root@FSB-BYRON-SRX210> show security dynamic-vpn users
User: lab , Number of connections: 2
Remote IP: 172.22.145.37
IPSEC VPN: dyn-vpn
IKE gateway: dyn-vpn-local-gw
IKE ID : labdynvpn
IKE Lifetime: 28800
IPSEC Lifetime: 3600
Status: CONNECTED
Remote IP: 172.22.145.24
IPSEC VPN: dyn-vpn-2
IKE gateway: dyn-vpn-local-gw-2
IKE ID : labtest1
IKE Lifetime: 28800
IPSEC Lifetime: 3600
Status: CONNECTED
The protected resources that are defined in the access profile are 10.0.0.0/8.
The pinging of the SRX interface address (10.10.10.10) is successful:
C:\Users\lab>ping 10.10.10.10 -t
Pinging 10.10.10.10 with 32 bytes of data:
Reply from 10.10.10.10: bytes=32 time=4ms TTL=64
Reply from 10.10.10.10: bytes=32 time=4ms TTL=64
Reply from 10.10.10.10: bytes=32 time=4ms TTL=64
Reply from 10.10.10.10: bytes=32 time=4ms TTL=64
Ping statistics for 10.10.10.10:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 4ms, Maximum = 4ms, Average = 4ms
Control-C
^C
The pinging of the SRX interface address (20.10.10.10) fails, as expected, as it is not part of the allowed resources via SRX:
C:\Users\lab>ping 20.10.10.10 -t Pinging 20.10.10.10 with 32 bytes of data: Reply from 152.179.43.29: Destination host unreachable. Request timed out. Reply from 152.179.43.29: Destination host unreachable. Request timed out. Reply from 152.179.43.29: Destination host unreachable. Request timed out. Reply from 152.179.43.29: Destination host unreachable. Request timed out. Reply from 152.179.43.29: Destination host unreachable. Request timed out. Reply from 152.179.43.29: Destination host unreachable. Request timed out. Reply from 152.179.43.29: Destination host unreachable. Request timed out. Reply from 152.179.43.29: Destination host unreachable. Request timed out.
Refer to the following images: