Using the Cisco SDM
The Cisco Router and Security Device Manager (Cisco SDM) is an easy-to-use, Java-based device-management tool, designed for configuring LAN, WAN, and security features on a router. The following sections describe how to use the Cisco SDM.
Upon completing this lesson, you will be able to describe the features of the Cisco SDM.
This ability includes being able to meet these objectives:
- Describe the features of Cisco SDM
- Explain how to use the elements of the Cisco SDM interface
- Explain the function of each of the five Cisco SDM wizards
Cisco SDM Overview
Cisco Secure Device Manager (SDM) is an intuitive, web-based device-management tool for Cisco IOS Software–based routers. Cisco SDM simplifies router and security configuration by using wizards, which help you quickly and easily deploy, configure, and monitor a Cisco router without requiring knowledge of command-line interface (CLI) commands. Cisco SDM is supported on Cisco 830 series, Cisco 1700 series, Cisco 1800 series, Cisco 2600XM, Cisco 2800 series, Cisco 3600 series, Cisco 3700 series, and Cisco 3800 series routers and on selected Cisco 7200 series and Cisco 7301 routers.
Cisco SDM allows you to easily configure routing, switching, security, and quality of service (QoS) services on Cisco routers while helping to enable proactive management through performance monitoring. Whether you are deploying a new router or installing the Cisco SDM on an existing router, you can now remotely configure and monitor these routers without using the Cisco IOS Software CLI. The Cisco SDM GUI aids nonexpert users of Cisco IOS Software in day-to-day operations, provides easy-to-use smart wizards, automates router security management, and assists you through comprehensive online help and tutorials. Figure 4-46 shows the home page of the SDM.
Cisco SDM smart wizards guide you step by step through router and security configuration by systematically configuring LAN and WAN interfaces, firewalls, intrusion prevention systems (IPS), and IP security (IPsec) virtual private networks (VPN). Cisco SDM wizards can intelligently detect incorrect configurations and propose fixes, such as allowing DHCP traffic through a firewall if the WAN interface is DHCP addressed. Online help in the Cisco SDM contains appropriate background information, in addition to step-by-step procedures to help you enter correct data in the Cisco SDM. Networking and security terms, and other definitions that you might need, are included in an online glossary.
For network professionals familiar with Cisco IOS Software and its security features, Cisco SDM offers advanced configuration tools to allow you to quickly configure and fine-tune router security features, allowing you to review the commands generated by Cisco SDM before delivering the configuration changes to the router.
Cisco SDM helps you configure and monitor routers from remote locations using Secure Socket Layer (SSL) and Secure Shell version 2 (SSHv2) connections. This technology helps enable a secure connection over the Internet between the user browser and the router.
When deployed at a branch office, a Cisco SDM–enabled router can be configured and monitored from corporate headquarters, reducing the need for experienced network administrators at the branch office.
Cisco SDM is supported on a number of Cisco routers and the associated Cisco IOS Software versions.
Always consult the latest information regarding Cisco SDM router and Cisco IOS Software release support at http://www.cisco.com/go/sdm.
Cisco SDM comes preinstalled on several Cisco router models manufactured in June 2003 or later that were purchased with the VPN bundle.
If you have a router that does not have Cisco SDM installed, and you would like to use Cisco SDM, you must download it from Cisco.com and install it on your router. Ensure that your
router contains enough flash memory to support both your existing flash file structure and the Cisco SDM files. Installing Cisco SDM on a Cisco router is beyond the scope of this course.
Configuring Your Router to Support Cisco SDM
You can install and run Cisco SDM on a router that is already in use without disrupting network traffic, but you must ensure that a few configuration settings are present in the router configuration file.
Access the CLI using Telnet or the console connection to modify the existing configuration before installing Cisco SDM on your router. Follow these steps:
Step 1 Enable the HTTP and HTTPS servers on your router by entering the following
commands in global configuration mode:
Router# configure terminal Enter configuration commands, one per line. End with CNTL/Z. Router(config)# ip http server Router(config)# ip http secure-server Router(config)# ip http authentication local Router(config)# ip http timeout-policy idle 600 life 86400 requests 10000
NOTE If the router supports HTTPS, the HTTPS server will be enabled. If not, the HTTP server will be enabled. HTTPS is supported in all images that support the crypto IPsec feature set, starting from Cisco IOS Release 12.25(T).
Step 2 Create a user account defined with privilege level 15 (enable privileges).
Enter the following command in global configuration mode, replacing
username and password with the strings that you want to use:
Router(config)# username username privilege 15 secret 0 password
For example, if you chose the username tomato and the password vegetable, you would enter the following:
Router(config)# username tomato privilege 15 secret 0 vegetable You will use this username and password to log in to Cisco SDM.
Step 3 Configure SSH and Telnet for local login and privilege level 15. Use the following commands:
Router(config)# line vty 0 4 Router(config-line)# privilege level 1 5 Router(config-line)# login local Router(config-line)# transport input telnet ssh Router(config-line)# exit
Start Cisco SDM
Cisco SDM is stored in the router flash memory. It is invoked by executing an HTML file in the router archive, which then loads the signed Cisco SDM Java file. To launch Cisco SDM, complete the following steps:
Step 1 From your browser, enter the following URL: https://<router IP address>
The https:// designation specifies that SSL protocol be used for a secure connection.
The http:// designation can be used if SSL is not available.
Step 2 The Cisco SDM home page will appear in the browser window. The username and password dialog box will appear. The type and shape of the dialog box will depend on the type of browser that you are using. Enter the username and password for the privileged (privilege level 15) account on your router.
The Cisco SDM Java applet will begin loading to your PC’s web browser.
Step 3 Cisco SDM is a signed Java applet. This can cause your browser to display a security warning. Accept the certificate.
Cisco SDM displays the Launch page.
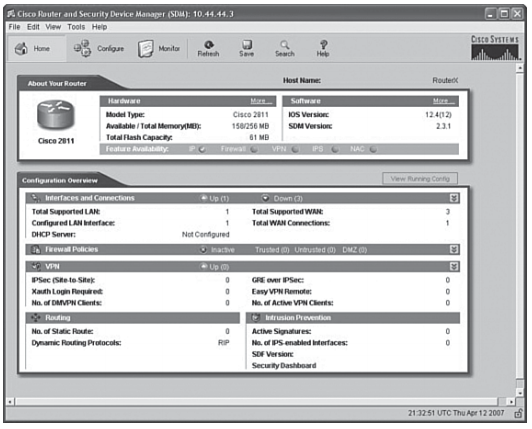
When the Launch window appears, Cisco SDM displays the Cisco SDM home page. The home page gives you a snapshot of the router configuration and the features that the Cisco IOS image supports. Cisco SDM starts in Wizard mode, in which you can perform configuration tasks using a sequence of windows that break the configuration task into manageable steps. Figure 4-47 shows the SDM home page.
The home page supplies basic information about the router hardware, software, and configuration, and contains the following sections:
- Host Name: This is the configured name of the router.
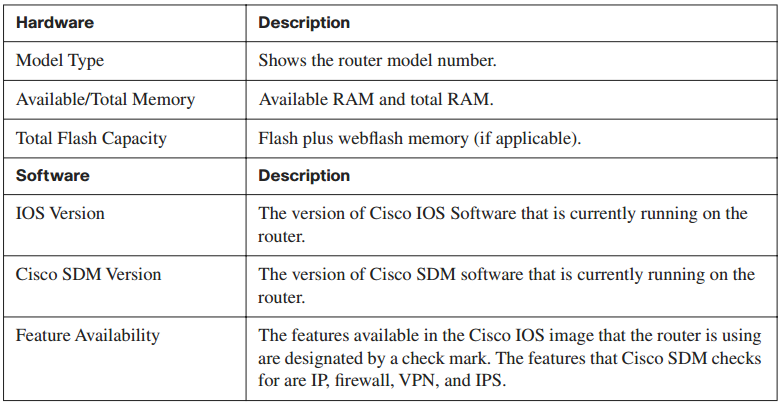
- About Your Router: This area shows basic information about your router hardware and software, and contains the fields shown in Table 4-11.
More Link
The More link displays a pop-up window providing additional hardware and software details, as follows:
- Hardware Details: In addition to the information presented in the About Your Router window, this tab displays information about the following:
- Where the router boots from—flash memory or the configuration file
- Whether the router has accelerators, such as VPN accelerators
- A diagram of the hardware configuration
- Software Details: In addition to the information presented in the About Your Router section, this tab displays information about the feature sets included in the Cisco IOS image.
Configuration Overview
This section of the home page summarizes the configuration settings that have been made.
To view the running configuration, click View Running Config.
The Interfaces and Connections area shows the following information:
- Up: The number of connections that are up.
- Down: The number of connections that are down.
- Double arrow: Click to display or hide details.
- Total Supported LAN: Shows the total number of LAN interfaces that are present in the router.
- Total Supported WAN: The number of Cisco SDM–supported WAN interfaces that are present on the router.
- Configured LAN Interfaces: The number of supported LAN interfaces currently configured on the router.
- Total WAN Connections: The total number of Cisco SDM–supported WAN connections that are present on the router.
- DHCP Server: Configured and not configured.
- DHCP Pool (Detail View): If one pool is configured, this area shows the starting and ending address of the DHCP pool. If multiple pools are configured, it shows a list of configured pool names.
- Number of DHCP Clients (Detail View): Current number of clients leasing addresses.
- Interface: Name of the configured interface, as follows:
- Type: Interface type
- IP Mask: IP address and subnet mask
- Description: Description of the interface
The Firewall Policies area shows the following information:
- Active: A firewall is in place.
- Inactive: No firewall is in place.
- Trusted: The number of trusted (inside) interfaces.
- Untrusted: The number of untrusted (outside) interfaces.
- DMZ: The number of demilitarized zone (DMZ) interfaces.
- Double arrow: Click to display or hide details.
- Interface: The name of the interface to which a firewall has been applied.
- Firewall icon: Whether the interface is designated as an inside or an outside interface.
- NAT: The name or number of the Network Address Translation (NAT) rule applied to this interface.
- Inspection Rule: The names or numbers of the inbound and outbound inspection rules.
- Access Rule: The names or numbers of the inbound and outbound access rules.
The VPN area shows the following information: - Up: The number of active VPN connections.
- Double arrow: Click to display or hide details.
- IPsec (Site-to-Site): The number of configured site-to-site VPN connections.
- GRE over IPsec: The number of configured Generic Routing Encapsulation (GRE) over IPsec connections.
- XAUTH Login Required: The number of Cisco Easy VPN connections awaiting an Extended Authentication (XAUTH) login.
NOTE Some VPN servers or concentrators authenticate clients using XAUTH. This shows the number of VPN tunnels awaiting an XAUTH login. If any Cisco Easy VPN tunnel is waiting for an XAUTH login, a separate message panel is shown with a Login
button. Click Login to enter the credentials for the tunnel.
If XAUTH has been configured for a tunnel, it will not begin to function until the login and password have been supplied. There is no timeout after which it will stop waiting; it will wait indefinitely for this information.
- Easy VPN Remote: The number of configured Cisco Easy VPN Remote connections.
- No. of DMVPN Clients: If the router is configured as a Dynamic Multipoint VPN (DMVPN) hub, the number of DMVPN clients.
- No. of Active VPN Clients: If this router is functioning as an Easy VPN Server, the number of Easy VPN clients with active connections.
- Interface: The name of an interface with a configured VPN connection.
- IPsec Policy: The name of the IPsec policy associated with the VPN connection.
The Routing area shows the following information: - No. of Static Routes: The number of static routes configured on the router.
- Dynamic Routing Protocols: Lists any dynamic routing protocols that are configured on the router.
The Intrusion Prevention area shows the following information: - Active Signatures: The number of active signatures that the router is using. These can be built-in, or they can be loaded from a remote location.
- No. of IPS-Enabled Interfaces: The number of router interfaces on which IPS has been enabled.
Cisco SDM Wizards
The following wizards are included in Cisco SDM:
- LAN wizard: Used to configure the LAN interfaces and DHCP.
- WAN wizard: Used to configure PPP, Frame Relay, and High-Level Data Link Control (HDLC) WAN interfaces. Check http://www.cisco.com/go/sdm for the latest information about wizards and the interfaces they support.
- Firewall wizards
- VPN wizards
- Security Audit wizards: There are these two options:
- The router security audit wizard
- An easy one-step router security lockdown wizard
- QoS: Quality of service wizard.
NOTE At the end of each wizard procedure, all changes are automatically delivered to the router using Cisco SDM–generated CLI commands. You can choose whether or not to preview the commands to be sent. The default is to not preview the commands.