Taxonomy of Network Attacks
In this section, we conduct a quick survey of the methodologies of attacks against our network infrastructure and the resulting threats against confidentiality, integrity, and availability. It won’t be all bad news, however, because we’ll summarize some of the best practices used to mitigate the effect of these attacks. We will:
- Define adversaries, their motives, and types of attacks.
- Summarize the concept of defense in depth.
- Examine the threat of IP spoofing.
- List and briefly summarize attack methods used to compromise confidentiality, integrity, and availability.
- Summarize some best practices for defense.
EXAM ALERT
Know the difference between vulnerability, risk, and exploit.
Categories of vulnerabilities are as follows:
- Poor design
- Weaknesses in protocols
- Software
- Misconfiguration
- Hostile code
- Human factor
Adversaries
So, who wants our stuff or wants to make our stuff unusable by us? Sounds simplistic, but answering this question and thus knowing your enemy (and their motivations) will go a long way toward acquiring the right mindset for designing network security controls. Remember, we are not at risk with all of these adversaries, so we should focus on only those where there is likelihood that they may exploit our vulnerabilities. Some examples are as follows:
- Nations or states
- Government agencies
- Hackers (we’ll examine these further)
- Terrorists
- Competitors
- Disgruntled employees
- Organized crime
Hackers
Hackers are the most obvious external threat to network security. There are several different species of hackers according to Cisco:
- Hacker. A computer enthusiast. They can also be grouped by their motivations:
- White hat. Ethical hacker.
- Black hat. Unethical hacker.
- Gray hat. We’re not sure! (This is a hacker who has a real job and sometimes plays both sides of the law, often motivated by intellectual challenge and notoriety but usually not monetary gain.)
- Blue Hat. Bug testers (from “blue collar”).
- Cracker. Hacker with criminal intent, motivated by economic gain.
- Phreakers (or Phone Phreaks). Hackers of telephone systems.
- Script Kiddies. Wannabe hackers with little or no skill.
- Hacktivist. Hacker with a political agenda.
Hacker Specializations
Whether a hacker wears a white, black, gray, or blue hat, they can be further defined by the type of hacking they perform:
- Computer Security Hackers. Usually secretive and specialize in computers and computer networks.
- Academic Hackers. Not usually secretive. Specialize in designing elegant software and gravitate toward Unix and the open source movement.
- Hobby Hackers. Usually hack code related to video games and gaming hardware and other home computing.
Motivations
As we’ve seen, in a broad sense, hackers can be categorized by their motivations but so too can the other adversaries. What makes them do it? Here are some motivations:
- Intelligence gathering
- Theft of intellectual property
- DoS
- Embarrassment of the target
- Intellectual challenge
NOTE
From this point forward, the term “hacker” will be used as a general term for any of the adversaries previously listed and who attacks an organization’s network and other systems.
How Do Hackers Think?
Hackers are said to think “outside the box.” Imagine that the hacker is a very clever lab animal that, when presented with a maze to run through as part of an experiment, chooses to run outside the maze to the prize. In so doing, the animal bypasses all the clever little turns in the maze that are supposed to make it difficult to get to the other side. The inference is clear. If our network is a maze, and the hacker is that clever animal, we will be in big trouble if we don’t start to think like him! This is not to say that all hackers take shortcuts, either. Nor do all hackers use the same methods, but here is an example of a typical structured attack.
Seven Steps for Compromising Targets and Applications
According to Cisco, the seven steps for compromising targets and applications are as follows:
- Perform footprint analysis (reconnaissance).
- Enumerate applications and operating systems.
- Manipulate users to gain access.
- Escalate privileges.
- Gather additional passwords and secrets.
- Install back doors.
- Leverage the compromised system.
EXAM ALERT
Memorize these steps. They are sure to be on the exam. To make it easier to remem ber, note that, generally, network attacks follow two broad steps: Explore, then exploit!
Concepts of Defense in Depth
Security is only as strong as its weakest link. Although this is a commonly held belief, it is not as commonly followed in practice. Defending a network with only one type of security control (administrative, technical, or physical) is bad enough, but many networks are only protected by one control. For example, protecting a home broadband connection with a single technical control such as an integrated firewall/router/wireless access point may be sufficient. It would certainly not be sufficient for a large e-commerce site that sells books online and keeps credit card information and other personal information about their customers. Clearly, the solution needs to be scaled to need and single points of failure should be avoided wherever possible.
To summarize, the Defense in Depth philosophy entails the following:
- Diversity and Redundancy. Use multiple security mechanisms to back up each other.
- Independence. Security mechanisms are self-sufficient and do not rely on one another.
- Augment Weakest Links. Single points of failure can be avoided.
Defense in Depth recommendations are as follows:
- Build a multi-layered defense.
- Place controls in multiple places.
- Use hardened, quality components.
- Use IDS or IPS (consider also Host IPS (HIPS)).
- Employ effective credential and key management.
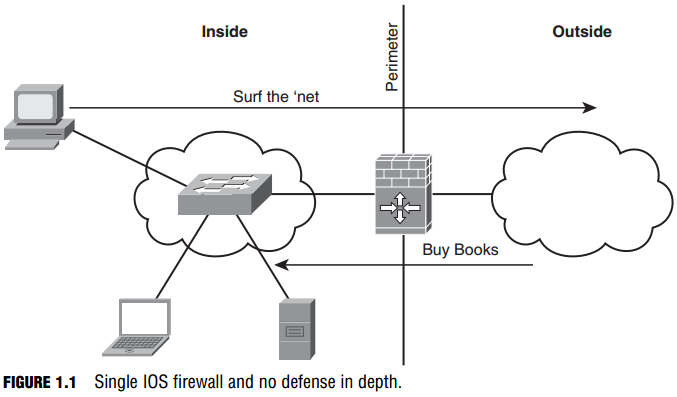
Figure 1.1 shows an example with no depth of defense. A single Cisco IOS firewall establishes a perimeter between an outside, hostile network and an e-commerce site’s inside network, where the employees’ computers and the book-selling server all reside. The firewall is configured to open up access from the outside to allow Internet users to connect to the server. This is an example of a single technical security control. The single technical control might be sufficient for a home network, but note that the file server coexists on the inside network with the employees’ computers. If hackers compromised the server, they could leverage the compromised server to attack other inside hosts including the switch, PC, and laptop. Without the use of an IDS or IPS, we might not even know that the attack had taken place. If this was a company’s e-commerce site, it doesn’t make sense to deploy a server in the same part of the network as knowledge workers’ computers. This is clearly a security incident waiting for a place to happen.
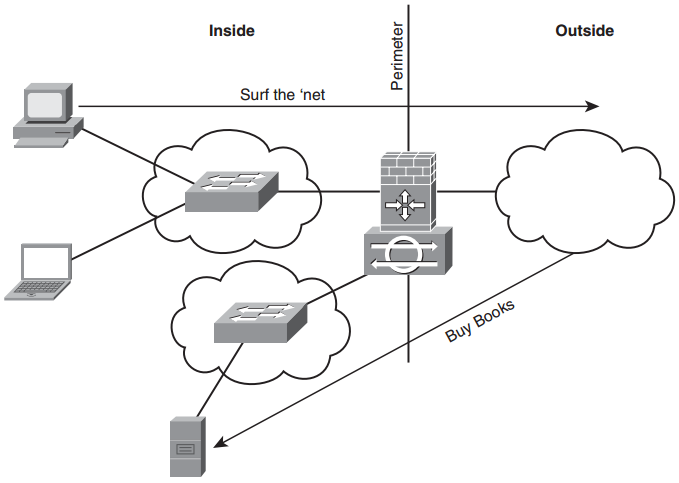
Some simple modifications to the security architecture illustrate the principle of depth of defense, as illustrated in Figure 1.2. The IOS router is configured as an IPS (see Chapter 8, “Network Security Using Cisco IOS IPS”) and can now detect and prevent intrusion attempts into and out of the inside network. The e-commerce server is deployed into a separate demilitarized zone (DMZ). Access Control Lists (ACLs) are configured on the IOS router to ensure that the e-commerce server cannot initiate a connection to an inside host, neutralizing the threat of its compromise leading to a compromise of our inside network. ACLs are covered in Chapter 5, “Using Cisco IOS Firewalls to Implement a Network Security Policy.” The IOS router is hardened against attack using principles discussed in Chapter 3, “Security at the Network Perimeter.” This also separates data planes, making it harder for an attacker to gain access to an inside host.
IP Spoofing Attacks
IP spoofing is the networking equivalent of identity theft. If you fake some other device’s IP address, you can pretend to be that other device in order to:
- Gain root access.
- Inject erroneous data into an existing conversation.
- Fool other devices in order to divert packets to the hacker.
- Overload resources on servers (DoS).
- Accomplish a task as part of a larger attack.
FIGURE 1.2 Single IOS firewall with defense in depth.
One of the things that makes IP spoofing so effective is that the process of routing is destination based, meaning that routers make their best path determination based on the destination IP address in an IP packet, often ignoring completely the source address. For example, if an attacker on the outside guesses correctly source addresses of devices internal to your network, they can inject packets into your network that appear to be coming from trusted hosts on the inside.
NOTE
The Open Systems Interconnect (OSI) model defines a packet as a network layer (layer 3) protocol data unit (PDU). An IP datagram is an example of a packet. Try to avoid using the term “packet” for PDUs at other layers of the OSI model. This will become very important in later chapters, where we will discuss TCP segments (layer 4) and Ethernet frames (layer 2) in the context of network security. This is terminology that you will have learned in your CCNA studies. If you don’t know them, now is the time to go back over your ICND1 and ICND2 notes to review them.
Recall that logical communication between TCP/IP hosts occurs at the transport layer of the OSI model. This is where dialog occurs between end systems. The Transmission Control Protocol (TCP) keeps track of the sequence number of segments both sent and received. Among other things, this allows an end system to put segments received in the right order, as well as retransmit segments from its transmit queue where the other device indicates that it has not received them.
Types of IP Spoofing
If an attacker were able to actually see these sequence numbers, maybe through the use of a packet capture tool, the IP spoofing attack would be called nonblind spoofing. They would need physical access to your network to accomplish this. If an attacker were simply guessing at sequence numbers—essentially using tools to calculate them—then the attack would be called blind spoofing. Physical access to your network is not required. Furthermore, with blind spoofing, the guesswork involved means that there is no verification of a successful attack.
NOTE
Another thing that aids the attacker is that although it is completely up to the end systems what initial sequence numbers they use to build a TCP session, some vendors’ TCP/IP implementations always use the same one. If an attacker were to know what type of sys tem they were dealing with through footprinting (recall “Seven Steps for Compromising Targets and Applications” in a previous section), the guessing would be much easier.
In any case, the information learned through IP spoofing in the course of network reconnaissance may lead to several types of attacks, including:
- Man-in-the-middle attacks (MiM). The attacker assumes the identity of a trusted host on the network and steals information. An example of this is session hijacking.
- DoS Attacks. The information gained leads to a flooding of resources on a targeted system. An example would be excessive hard drive thrash of an unpatched web server.
- Distributed DoS Attacks (DDoS). The information learned during the reconnaissance leads to a flooding of resources on a targeted system from multiple hosts and simultaneously. An example would be an attack on a core network device that consumes all the bandwidth into and out of a network.
NOTE
MiM attacks attack the network’s confidentiality. They also attack the network’s integrity because invalid data can be replayed into the network by a spoofed system. DoS and DDoS attacks attack the network’s availability.
Attacks Against Confidentiality
If effective administrative, technical, and physical security controls are in place, the risk of the following attacks would be minimal.
EXAM ALERT
According to Cisco, attacks against confidentiality are successful if you have been lax with access control (network, OS, application) or protection of data moving over hostile, untrusted networks.
Examples of attacks that may lead to confidentiality (and other) breaches include the following:
- Protocol Analysis (Packet Sniffing). As indicated previously, this is very effective if the attacker has physical access to your network. Packets can be captured and often analyzed offline for cleartext, confidential information.
- Port Scanning. This is very common during the reconnaissance phase of an attack, using tools like nmap or Nessus to scan a network to find out what TCP ports are open.
- Ping Sweeps. Often used in the initial phases of reconnaissance. First find out what hosts are answering to the ping (ICMP echo packet); then drill down on them with a port scan (see previous).
- Dumpster Diving. Organizations often accidentally throw out sensitive information that would be of use to an attacker.
- Social Engineering. Subverting an individual through social skills within a targeted organization to provide information that is either confidential by itself or that can lead to the breach of a network’s security controls.
- Overt Channels. Hiding something out in the open sounds like an oxymoron. An attacker can craft an attack that tunnels one protocol inside another protocol. If the security appliance or IDS/IPS is not configured to check protocol compliance at the application layer, it will be successful. An example might be a Peer-to-Peer (P2P) file transfer of malicious code using Kazaa inside an HTTP session. Another example might be the process of steganography. This is typically executed through the secretion of hidden messages into image files, themselves embedded in overt
objects such as HTML for transport. - Covert Channels. Hiding information (perhaps by encryption) within a network session. An example might be injecting some malicious code
within a legitimate client-server session. This is sometimes called a back channel attack. - Emanations Capturing. Capturing electrical and radio frequency emissions (from wireless networking gear, for example) using passive means and decoding their meaning. Can be countered with TEMPEST standard equipment.
NOTE
TEMPEST is a U.S. government standard. Equipment or rooms that are certified as TEMPEST standard are leakage-free but it is an expensive standard. Other nations have similar standards. Interestingly, TEMPEST is actually not an acronym, though many have tried to make it into one. One of the most common examples of this “bacronym” is “Transient Electromagnetic Pulse Emanation Surveillance Technology.” It sounds cool, but it’s incorrect. Why not “Tiny ElectroMagnetic Particles Emitting Secret Things?” TEMPEST is an unclassified U.S. govern ment code word coined by the National Security Agency (NSA) in the late 60’s and early 70’s for an operation for compromising emanations. The general term for preventing unwanted electromagnetic emissions is now more properly called Emissions Security (EMSEC).
Phishing, Pharming, and Identity Theft
Two very real exploits that are commonly in the news are phishing and pharming. Both these exploits are threats against a user or site’s identity.
- Phishing. This is a social engineering attack. By posing as a legitimate, trusted third party, an attacker attempts to acquire confidential or sensitive information from the victim. The most common vehicles for phishing are email messages that entice victims to visit a legitimate-looking
website where their credit card information, PINs, and so on, are stolen. - Pharming. This is the process of farming (get it?) or harvesting traffic from one website by redirecting it to another. A common method is commandeering vulnerable Domain Name System (DNS) servers and altering their records so that users are redirected to a site not operated by the real owner of the domain name.
Antivirus, antispyware, and anti-spam software are somewhat effective against phishing attacks. Nevertheless, this type of technical control is not a replacement for the administrative control of educating users.
There is no specific technical control to thwart pharming, however. The best defense is to make sure that vulnerable servers are properly patched (problematic across the whole Internet!) and to regularly test DNS resolution against root servers in the Internet to ensure that an organization’s fully-qualified domain name (FQDN) resolves properly to the correct IP address.
Attacks Against Integrity
EXAM ALERT
Like attacks against confidentiality, attacks against integrity are successful if you have been lax with access control (network, OS, application) or protection of data that moves over hostile, untrusted networks.
We’ve done a good job at defining integrity previously, so let’s look at a list of common attacks against a system or a network’s integrity. These attacks might also be used to breach availability and confidentiality:
- Salami Attacks. Salami, like sausage, is made up of a variety of ingredients. It’s not a single meat. This is true with a salami attack. It is a larger attack that is comprised of a series of smaller attacks. An example would be an attacker launching an attack that makes small compromises of the integrity of several different systems’ databases simultaneously. This type of granular, spread-out attack is difficult to detect.
- Data Diddling. Interfering with data before it is stored on a computer, prior to or during data input. This may be the result of a virus or even malicious code designed into the program.
- Trust Exploits. An attacker leverages on a trust relationship between devices on a network. Port redirection is an example of this type of attack. A walk-through of a port redirection is found in Figure 1.3.
- Password Attacks. This is any attack that is geared toward making a system divulge its password database. Viruses, trojans, keyloggers, protocol analyzers (sniffers), and brute force attacks are common vectors.
Application protocols such as Telnet and FTP that use cleartext passwords are the most vulnerable to the use of protocol analyzers. Even protocols like NTLM (Windows NT LAN Manager) and Active Directory, which exchange hashes of passwords vs. cleartext passwords, are vulnerable to offline, brute force tools such as John the Ripper.
NOTE
Hashing is explained in Chapter 6, “Introducing Cryptographic Services.” Although theoreti cally a hash cannot be cracked, there are cracking programs such as RainbowCrack, which can match a hash against a database of known hashes captured with protocol analyzers.
- Session Hijacking. This is the most common Man-in-the-Middle (MiM) attack. It’s not so much an attack in itself, as it is a result of a successful attack.
EXAM ALERT
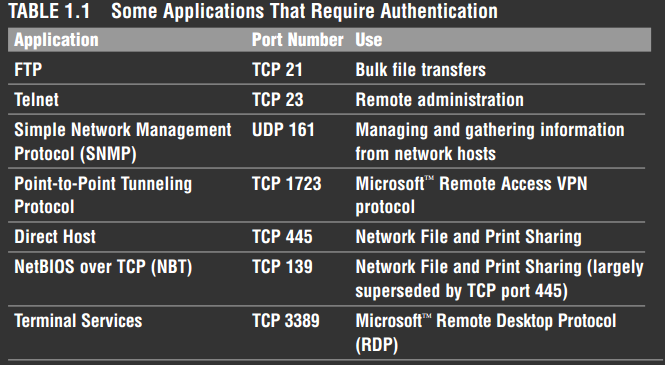
Memorize the names and port numbers of several popular protocols that use authentication, as shown in Table 1.1.
Attack Against Integrity Example: Port Redirection Attack
This example should help bring together some concepts about attacks against in
tegrity. Revisit the simple network from a previous example now in Figure 1.3. Figure 1.3 shows an IOS router with three interfaces: one facing the Internet, another one facing the inside, and a third that establishes a DMZ where the ecommerce server is deployed. Figure 1.3 shows a port redirection attack in which “Z” trusts “Y” and “Y” trusts “X.” The attacker is trying to trick “Z” into trusting “X” too. Arrow “A” illustrates that the router is configured to allow connections from the outside to the web server in the DMZ on TCP port 80 (or else, how could we sell books?). The router will not allow connections to be initiated from the outside to the inside. However, the router is configured to allow the DMZ server to initiate connections to the inside (arrow “B”) perhaps to synchronize its clock on a time server or to authenticate users on a AAA server. Here’s how an attack might unfold:
- A hacker “X” conducts a port scan of the network and discovers that there is a web server “Y.” The hacker footprints the network using a tool such as nmap and learns that the web server software used may have some vulnerabilities that could be exploited. This peaks his interest!
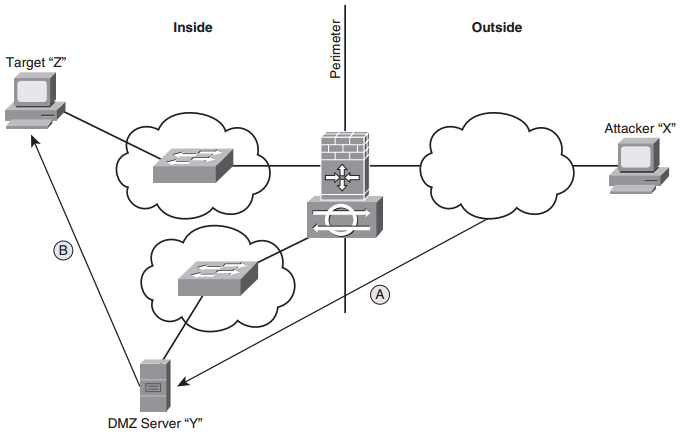
FIGURE 1.3 Port redirection attack.
- The attacker uses a hacking tool such as netcat to compromise the web server and installs a port forwarding tool, such that when inbound WWW traffic from the attacker’s workstation is sent to the compromised web server, it will redirect it to a different port entirely (TCP port 3389 = Terminal Services, for example).
- Now the attacker can essentially tunnel the desired protocol inside HTTP to the DMZ server and then use the DMZ server to attempt to establish a connection to an inside host “Z.”
- Because the attacker has control over the DMZ server, he can complete a remote reconnaissance of the internal network from the DMZ server using a ping sweep to find out what IP addresses are active.
- The attacker conducts a port sweep to see what services are available on the active IP addresses.
- The attacker then attempts to exploit vulnerabilities on inside hosts, perhaps also installing keylogger software, and so on.
The attacker has now successfully leveraged the trust relationships. “Z” trusts “Y.” “Y” trusts “X.” Now “Z” trusts “X,” too. Ouch! This is what makes port redirection an example of a trust exploit. The risk of this exploit happening can be mitigated by:
- Installing a firewall or IPS, which can examine inbound HTTP traffic to ensure that it is protocol compliant, block traffic that isn’t, and also alert a custodian.
- Installing Host Intrusion Protection System (HIPS) software on inside hosts.
- Using ACLs on the IOS firewall to tighten the rules as to which IP addresses and applications the DMZ server is allowed to initiate connections to on the inside.
NOTE
ACLs, firewalls, IPS, and HIPS will be discussed in later chapters, although hopefully you are getting a feel for their respective roles in the context of this discussion at this point in the Exam Cram.
Attacks Against Availability
Now we move on to the last letter of our C-I-A triad and more reasons for network insecurity! We look at what constitutes an availability attack and how to mitigate their effects.
EXAM ALERT
Availability attacks are DoS attacks. If these attacks are successful, it is because the system fails to either handle:
- Unanticipated, exceptional conditions (such as malicious code, buffer overflows, and so on).
- Enormous floods of data, crashing a system or bringing it to a halt. …leading to a compromise of availability.
Also know that many availability attacks can be used to attack confidentiality and integrity too.
NOTE
Heads up! Strictly speaking, any type of attack that seriously impedes the availability of a network or system is a DoS attack. By that definition, availability attacks are DoS attacks. Nevertheless (and confusingly) DoS is often also identified as a category of availability attack, typically a network-borne attack. Don’t be confused by this inconsistency. Just know that the term DoS can be used correctly in those two contexts. Aiding an attacker is the relative simplicity of the attack methods. Even a script kiddy would have no problem executing some of these attacks. Some common types of availability attack include the following:
- Botnets
- ICMP floods
- DoS
- DDoS
- SYN floods
- Electrical power
- Computer environment
- MAC flooding
The following sections go over each type of availability attack in more detail.
Botnets
A botnet is a collection of infected computers or “robots” that can be controlled by crackers. The location of infected computers is shared by circles of crackers who can then seize control of these machines, typically on Internet Relay Chat (IRC), and use them in the commission of larger attacks such as a DDoS. For crackers, locating these computers’ IP addresses can be done fairly easily if they register their domain names dynamically with a Dynamic DNS provider. Whole communities of infected computers might resolve to the same domain suffix, such as “ivebeenhacked.net.”
ICMP Floods
ICMP floods work like they sound. A constant stream of ICMP messages is sent against a system. No response is necessary; the ICMP message just has to be received by the host being attacked. Conducting a constant ping from one host is unlikely to completely consume bandwidth and/or CPU cycles on an attacked host. However, when used as part of a DDoS attack (maybe combined with spoofed source IP addresses!), it can be quite effective.
DoS
In general terms, DoS attacks occur when an attack is leveraged against a system that slows its response to legitimate requests. The affected server will eventually drop requests from legitimate clients when there are too many unanswered requests for resources in its receive queue.
DDoS
A DDoS attack is a DoS attack from many sources simultaneously, perhaps from hosts enlisted from a botnet. This remains a common attack due to both its efficacy and its relative simplicity to execute.
SYN Floods
This is a type of DoS attack. This attack leverages on the requirement within the Transmission Control Protocol (TCP) that a server answer a synchronization attempt from a client (SYN) when a connection is being established to his well-known port number. Think of the SYN, which is carried inside a TCP segment, as pushing a doorbell. A web server has a doorbell with the number “80” on it. The server, if it is polite (or at least protocol compliant!) is required to answer the SYN with a SYN, ACK. Of course, in between the time that the attacker has pressed the server’s doorbell and the time the server has gotten out of his comfortable chair to answer the door, perhaps thousands of other doorbell presses to port 80 have happened … some of them even from legitimate clients of the server. The attacker won’t even wait around to see if the server has come to the door because unlike a legitimate client, his goal is not to actually create a connection with the server but to frustrate him. Meanwhile the server has to allocate memory and other resources for each connection attempt. Eventually, the server is going to get so tired of coming to the door only to find that there is no one there, that he will no longer answer the door for anybody, attacker and legitimate user alike.
Electrical Power
Any attack against an organization’s electrical power is an availability attack. There are three categories, as follows:
- Excess power (spikes and surges)
- Complete power outage (brief faults and blackouts)
- Reduced power levels (sag and brownouts)
Computer Environment
One of the most neglected parts of network security. This falls under the broad category of physical controls (remember “PAT”?). Ensure that the physical environment is regulated for the following:
- Temperature
- Ventilation
- Humidity
MAC Flooding
This kind of attack will be examined in more detail in Chapter 10, “Protecting Switch Infrastructure.” This is an OSI layer 2 (data link layer) attack. Essentially, an attacker can use some commonly available tools (such as the macof utility) to inject a switch with vast quantities of Ethernet frames with fictitious source addresses. The normal behavior of the switch is cache these addresses in its MAC address table. The MAC address table can contain a finite number of entries. For example, a Cisco Catalyst 2924-XL-EN can contain 4096 entries in its MAC address table. Eventually, the switch will become so full of bogus MAC addresses that when it receives a frame, it will flood it out all its ports, effectively acting like a hub. If an attacker is connected to one of the switch’s ports, they will potentially see all the traffic served by that switch, compromising confidentiality as well as availability
NOTE
Do you know how on some vacuum cleaners, you can reverse their operation so they will blow air rather than suck particles? Some protocol analyzers can be configured to not only suck traffic off a wire, but to blow engineered traffic back (for example, Ethernet frames) into a network. Instant attack tool!
Best Practices to Thwart Network Attacks
If common sense were so common, we wouldn’t have to call it common. Cisco makes specific recommendations as to some best practices for ensuring that you reduce the risk footprint of your network through three categories of controls:
administrative, technical, and physical security controls.
Administrative Controls
Administrative controls include the following:
- Written Security Policy. Put your security policy in writing! Make sure all the stakeholders: owners, custodians, and users understand and respect their responsibilities. (This will be discussed in Chapter 2, “Building a Secure Network Using Security Controls.”)
- Education. Ensure all stakeholders are aware of the dangers of social engineering.
- Patches. Keep up-to-date with firmware, hardware, and software patches, particularly those that address security vulnerabilities.
Technical Controls
Technical controls include the following:
- Unnecessary Services and TCP/UDP Ports. Configure the network such that only necessary services are exposed. Don’t forget to configure servers so they only have the necessary services active.
- Encryption. Encrypt all sensitive data, especially if it passes over hostile networks.
- Passwords. Rotate passwords often and make them complex (strong).
- Hardware and Software. Use hardware and software that can mitigate risk to an appropriate level.
Physical Controls
Physical controls include the following:
- Physical Access. Limit physical access to systems to a select few and only those who need it.
- Environmental. Equipment should be in a controlled environment with regulated temperature, power, and ventilation.