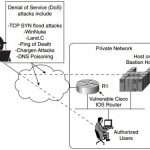
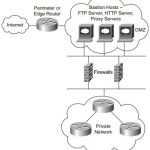
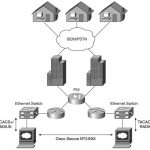
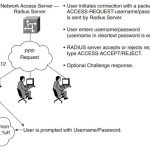
CCIE Security FAQ Network Security Policies, Vulnerabilities, and Protection Q1. A remote user tries logging into a remote network but fails after three additional tries and is disconnected. What useful information should the network administrator gather? (Select the best two answers.) a. Username b. Invalid password c. Invalid username d. Valid username Answer: b and … [Read more...]
CCIE Security FAQ Security Technologies
CCIE Security FAQ Security Technologies Q1. DMZ stands for what? a. Demilitarized zone b. Demitted zone c. Domain main zone d. Domain name Answer: a Q2. When defining an extended access list, what TCP port numbers can you use? a. Only predefined Cisco keywords b. 0 to –65,000 c. 0 to –65,535 d. 1 to 65,534 e. None of the above Answer: c Explanation: TCP port … [Read more...]
CCIE Security FAQ Operating Systems and Cisco Security Applications
CCIE Security FAQ Operating Systems and Cisco Security Applications Q1. What UNIX command implements a trace route to the remote network www.guitar.com? a. trace www.guitar.com if DNS is enabled with the IOS command dns server ip-address. b. traceroute www.guitar.com c. trace guitar.com d. UNIX does not support the traceroute command. Answer: b Q2. What UNIX … [Read more...]
CCIE Security FAQ Security Protocols
CCIE Security FAQ Security Protocols Q1. What are the three components of AAA? (Choose the three best answers.) a. Accounting b. Authorization c. Adapting d. Authentication Answer:a, b, and d Explanation: AAA is used for authentication, authorization, and accounting. Answer c is incorrect because adapting is not part of the security options available with AAA. Q2. What … [Read more...]
CCIE Security FAQ Cisco IOS Specifics and Security
CCIE Security FAQ Cisco IOS Specifics and Security Q1. What IOS command will display the System Flash? a. show flash b. show system flash c. show memory d. show process flash Answer: a Explanation: The show flash IOS command displays the System Flash: R1#show flash System flash directory: File Length Name/status 1 11600424 c2600-ik8o3s-mz.122-2.T.bin [11600488 … [Read more...]
CCIE Security FAQ Application Protocols
CCIE Security FAQ Application Protocols Q1. RFC 1700 defines what well-known ports for DNS? a. TCP port 21 b. TCP port 23 c. UDP port 21 d. UDP port 53 e. TCP/UDP port 53 Answer: e Explanation: DNS is permitted by RFC 1700 to use both TCP/UDP port 53. Typically UDP is vendor configured for UDP port 53. Q2. What supplies DNS security? a. A default username/password … [Read more...]
CCIE Security FAQ General Networking Topics
CCIE Security FAQ General Networking Topics Q1. Which layer of the OSI model is responsible for converting frames into bits and bits into frames? a. Physical b. Network c. Transport d. LLC sublayer e. Data link Answer: e Explanation: The data link layer performs bit conversion to pass to the MAC sublayer. Q2. Routing occurs at what layer of the OSI model? a. … [Read more...]