This article describes the impact of Java 7 Update 51 on older versions* of Java Applets used by certain client components of Juniper’s SSL VPN solutions (JSAM, Juniper Setup Applet, Junos Pulse Collaboration, Network Connect, Premier Java RDP Applet).
* Prior to:
SA 7.1R17
SA 7.3R9
SA 7.4R7
SA 8.0R1
According to the information available on this Oracle blog, after upgrading the Java version on the client computer to Java 7 update 51, older versions of Java Applets used by Juniper’s SSL VPN solution may be blocked. Based on our internal testing, older versions of Java Applets will be blocked and the end user may see the following or similar error message:
SecurityException: Missing required Permissions manifest attribute in main jar: https://ive77.sslvpnlab.com/dana-cached/sc/JuniperSetupClientApplet.jar
FAQ:
1. What specific use cases are impacted?
Any use cases that involves the use of a Java Applet will be impacted. Such as:
a. Juniper Setup Applet: When using a browser that does not support Active-X, such as Safari or Firefox, the Juniper Setup Applet is used to deliver and launch client applications such as Host Checker, Junos Pulse, Network Connect and Junos Pulse Collaboration.
b. JSAM: JSAM is a Java based applet and is impacted.
c. Premier Java RDP applet: This is another Java applet based access method and is impacted.
2. I do not use a browser to sign-in or start my SSL VPN session; instead I directly launch the Junos Pulse Client installed on my computer. Am I still impacted?
No. If you directly launch the Junos Pulse client then you will not be impacted by this issue as this use case does not involve the use of any Java applet.
3. What about applets delivered through Juniper’s Java Applet Rewrite Engine?
Juniper’s Secure Access (SSL VPN) solution offers a powerful option of rewriting Java applets, making it possible to use Java applets without a client. When using this access method and SA 7.1R17, 7.3R9, 7.4R7, 8.0R1 or later, the rewrite engine will automatically add the ‘permissions’ attribute to the manifest file after rewriting the applet only if the original applet had this attribute set. Refer KB
Java Update 51 has introduced changes that mandate the presence of this “permissions” attribute along with the requirement of code signing all applets. The issue described in this KB is due to the older versions of applets not containing the “Permissions” attribute within the manifest file.
Note: All JAR files (applets) used in Juniper’s SSL VPN software are digitally signed (code signed) in all releases.
This issue has been resolved in Secure Access (SA) version 7.1R17, 7.3R9, 7.4R7, 8.0R1 and later versions. The issue was resolved by adding the “permissions” attributes within the manifest file.
Workaround:
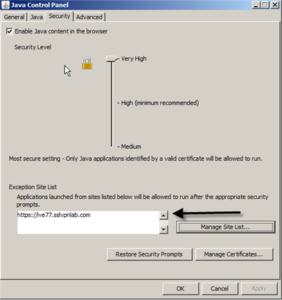
If you are unable to upgrade your SSL VPN platform to one of the above mentioned versions then as a workaround end users can use the “Exception Site List” feature described here. In the example shown in the below screenshot the SSL VPN gateway device is accessed via URL https://ive77.sslvpnlab.com/