How Juniper Host Checker detects if iOS is jail broken or not.
- iOS jail breaking is the process of removing the limitations imposed by Apple on devices, which are running the iOS operating system through the use of custom kernels.
- Jail breaking allows users to gain root access to the operating system; allowing iOS users to download additional applications, extensions, and themes, which are unavailable through the official Apple App Store.
- A jail broken iOS device can still use the App Store, iTunes, and other normal functions (such as making telephone calls). Unlike rooting an Android device, jail breaking is necessary; if the user intends to run software which is not authorized by Apple.
- Organizations, as per their company security policy, may want to block access to the internal resource via the SA, for the iOS devices which are jail broken.
For example:
- iOS is Jail broken by a well known application – Cydia.
- You can detect a jail broken iOS, by identifying whether Cydia is installed and check if the /private/var/lib/apt/ folder is present in the file system.
- If any of this is found, iOS can be considered to be jail broken.
To configure the Jail Breaking Detection rule, perform the following procedure:
1.Go to Authentication > Endpoint Security > Host Checker.
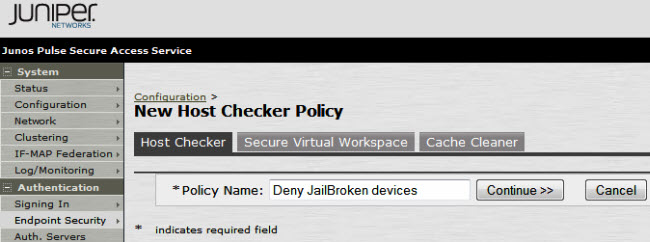
2.Under Policies, click New, type a name for the policy in the Policy Name field, and click Continue:
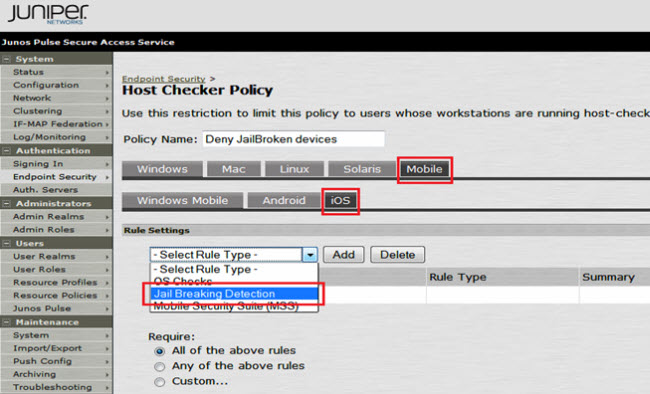
3.On the next window, go to Mobile > iOS. From the Select Rule Type drop-down menu, select the Jail Breaking Detection option:
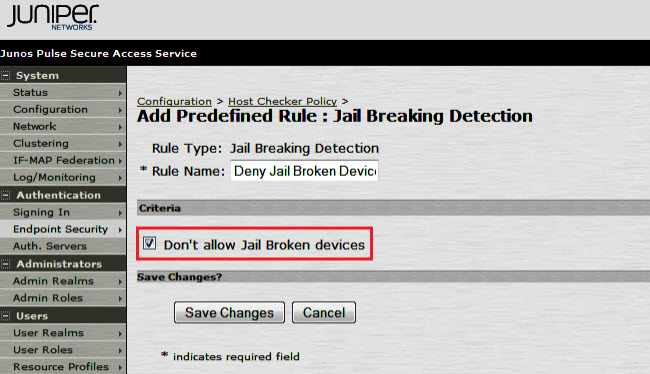
4.Under Criteria select the Don’t allow Jail Broken devices checkbox and click Save Changes:
5.This Policy is then included as a part of Realm/Role level Host Checks.
Note: This requires both IVE OS 7.2 and Pulse 3.2 for iOS. If this is enabled prior to the client being upgraded to 3.2, the user login will fail (and the option is not present pre-7.2). Additionally, if this check is enabled, users will not be able to login via Mobile Safari.