Overview of VLANs
Objectives:
- Describe enhanced switching technologies (including: VTP, RSTP, VLAN, PVSTP, 802.1q)
- Describe how VLANs create logically separate networks and the need for routing between them
In your company, you may have several departments connected to the same Layer 2 switch or switched network. Quite often, departments may be running applications and protocols that are unique to users within their own group. Unfortunately, if this traffic consists of multicasts and broadcasts (or unknown unicasts, for that matter), that traffic hits all users connected to
that switched network.
For instance, imagine that the Not-So-Human Resources department is running a developed program that helps them track employee lunch break times. Unfortunately, this traffic relies heavily on broadcasts to communicate with other applications being used by personnel in that department. The broadcast and multicast traffic from the Not-So-Human Resources department continues to be flooded out to everyone else in the network because they are all connected to the same switched network.
Because this is the only department that uses this software, ideally it would be convenient to separate the Not-So-Human Resources group into their own separate switched LAN so their traffic doesn’t affect any other department. To this point, the only way you could segment this network into smaller broadcast domains is by using a router because routers do not forward broadcasts or multicasts by default.
The problem with this solution is that routers can be expensive, considering you need an interface for each department to keep the traffic separate. In addition, because routers have to process all the way into the Layer 3 information of a packet before sending the traffic to a different segment, throughput is considerably slower than that of a switch. Not to mention, if you have users within departments physically dispersed all throughout your network, the broadcast and multicast traffic would never reach them because the router does not forward them onto other interfaces.
The answer to all these problems lies within the magic of virtual LANs (VLANs). VLANs enable you to segment broadcast domains at Layer 2 without a router. Each VLAN created in a switch represents a logical grouping of devices into their own broadcast domain. Thus, each department can have its own VLAN that separates traffic from one department from that of other departments. In fact, devices in one VLAN cannot communicate with other devices in another VLAN without the help of a router, even if those devices are plugged into the same switch. What’s more, VLANs can span multiple switches, so the geographic location of the devices is no longer a limiting factor. As members of a specific department are added or moved, you simply need to assign their switch interface to the department’s VLAN.
What is also remarkable about VLANs is that because each VLAN represents a broadcast domain in which devices can communicate only with other devices in that same VLAN, there must be a separate instance of Spanning Tree Protocol (STP) running for each VLAN. In other words, if you have 20 VLANs running in your switched network, you will have 20 instances of STP running, each with its own root bridge. The term for this ability to have a separate instance of Spanning Tree Protocol for each VLAN is called PVST (per VLAN Spanning Tree). It is for this very reason that the configuration for the STP priority (discussed in Chapter 13, “Foundation Switching Operations”) required that the VLAN be specified in the command syntax.
EXAM ALERT
Unless VLANs are specifically mentioned in an exam question or answer choices, routers segment broadcast domains and switches segment collision domains.
VLAN Membership Methods
After the VLANs are created, they have to be associated with the users or departments connected to the switches. The most common way to associate VLANs is statically on a port-byport basis. When the VLAN is associated with the switch port, it is referred to as an access port. When a single VLAN is assigned on the interface, traffic is sent to and received by only devices
connected to interfaces with the same VLAN.
For instance, consider the typical single-switch VLAN configuration exhibited in Figure 15.1. All these switches are access ports that have a single VLAN assigned to them. On Fast Ethernet interfaces 0/1 and 0/3, they are assigned to VLAN 1. Our Not-So-Human Resources VLAN (VLAN 3) has been assigned to Fast Ethernet interfaces 0/2, 0/4, and 0/5. The devices connected to these interfaces can communicate only with other interfaces that also contain that VLAN.
So in the example, the printer and the computer on the right can communicate with each other and the computer connected to interface Fast Ethernet 0/2. Even though they are connected to the same switch, these devices cannot communicate with the computers connected to interfaces assigned to VLAN 1 because they are in a completely different broadcast domain.
An alternative to static VLANs is to have the VLANs dynamically associated with the frames entering a switch. To achieve this, you must configure a VLAN Membership Policy Server (VMPS). The VMPS is a device, such as a server or even a high-end Catalyst switch, that has an association of every MAC address with a VLAN. When the frame enters a port, the switch acts as a client and queries the VMPS for the VLAN assigned to that MAC. This is appealing because you don’t have to configure VLANs on every interface; however, it does require a good deal of initial setup on the actual server.
The Management VLAN
Conveniently enough, your switch is already configured with a default VLAN that is used for management on access ports. This is used for a management communication channel because the IP address, CDP, and VTP (discussed later in this chapter) all exist in the management VLAN for ethernet, VLAN 1. This VLAN is created by default in all Cisco Catalyst switches and assigned to all interfaces. Because it is applied to all switch ports, it still holds true that all devices connected to a switch are in the same broadcast domain.
Recall from Chapter 13 that to assign a management IP address to a switch, you configure the IP on interface VLAN 1. This means that your management workstation must have access to VLAN 1 to remotely manage the Catalyst switch. If you change the VLAN on the port in which your management station or your router (if managing it remotely) is connected, you lose the ability to manage the switch with Telnet, SSH, HTTP, or SNMP.
Configuring and Verifying VLANs
Objective:
- Configure, verify, and troubleshoot VLANs
All interfaces are already assigned to VLAN 1. To create smaller broadcast domains in your switch, you must create those VLANs for each department you want to segment and assign them to their respective interfaces. Specifically, the configuration steps for VLANs are as follows:
- Create the VLAN, using a number between 2 and 1001.
- Name the VLAN. If you do not assign it a name, it uses VLANxxxx, where xxxx is the VLAN number.
- Assign it to a switch port.
EXAM ALERT
Know the three steps involved in configuring VLANs.
VLAN-specific configurations are permanently stored in Flash memory in a special file called the VLAN database (vlan.dat). To configure VLANs on the Catalyst switch, you must navigate to a VLAN configuration mode from global configuration referred to as config-VLAN Mode. To navigate to this configuration mode, you type the command vlan followed by the VLAN ID you want to create. At this point, the prompt changes to Switch(config-vlan)#, signifying that you are in the config-VLAN mode. At this stage of the VLAN configuration, you have the option to assign a unique name to the VLAN you just created by typing the keyword name followed by the custom name of your VLAN. If you do not specify a name, the switch will automatically assign the name using the VLAN ID. For instance, if you chose the number 4 for the VLAN ID, the VLAN name defaults to VLAN0004.
In the following example, we are creating two VLANS; one we named NSHR and the other we left to its default VLAN name based on the VLAN ID:
Switch#configure terminal Enter configuration commands, one per line. End with CNTL/Z.
Switch(config)#vlan 3 Switch(config-vlan)#name NSHR Switch(config-vlan)#exit Switch(config)#vlan 4 Switch(config-vlan)#exit Switch(config) #
A VLAN is useful only if it is assigned to an interface; thus, our next logical step is to assign VLAN 3 and VLAN 4 to switch ports to segment those devices connected to those interfaces into their own VLAN broadcast domain. To statically assign the VLANs to a switch port, you must navigate to the interface and use the switchport access vlan command as demonstrated here:
Switch(config)#interface FastEthernet 0/2 Switch(config-if)#switchport access vlan 3 Switch(config-if)#exit Switch(config)#interface FastEthernet 0/7 Switch(config-if)#switchport access vlan 4
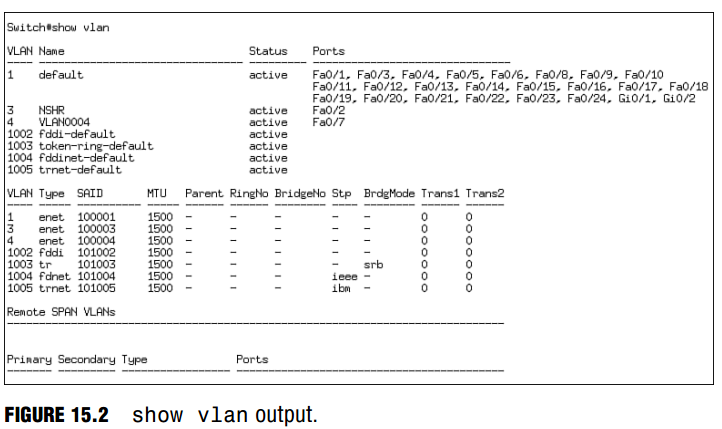
Because these VLAN configurations are stored in the VLAN database, they will not be displayed in the running or startup configs. Instead, to verify your VLAN configuration, use the show vlan command to observe the VLANs that you created and the interfaces to which they are applied, as demonstrated in Figure 15.2.
EXAM ALERT
The previous version of the exams tested your knowledge on configuring VLANs using the VLAN Database Configuration Mode from privileged EXEC. The current exams no longer test your configura tion knowledge using this mode but rather using the config-VLAN Mode as described in this chapter.