This article provides detailed information related to the fixes for OpenSSL “Heartbleed” issue(CVE-2014-0160) /JSA10623 for SSL VPN products.
The following SSL VPN versions are vulnerable to the OpenSSL vulnerability CVE-2014-0160 as described in JSA10623
Server-side:
1. Secure Access software versions 7.4R1 to 7.4R9.
2. Secure Access Software versions 8.0R1 to 8.0R3.
Client-Side:
1. Junos Pulse (Desktop) version 5.0R1 to 5.0R3.
2. Junos Pulse (Desktop) version 4.0R5 to 4.0R9.1.
3. Network Connect (windows only) version 7.4R5 to 7.4R9.1 and 8.0R1 to 8.0R3.1. This client component is impacted only if used in FIPS mode. Non-FIPS version of Network Connect clients are not impacted.
4. Junos Pulse (Mobile) for Android version 4.2R1 to 5.0R3
5. Junos Pulse (Mobile) for iOS version 4.2R1 to 5.0R2. This client component is impacted only if used in FIPS mode.
6. Windows In-Box Junos Pulse Client on Windows 8.1
For details on client-side exposure refer FAQ # 1 (Exposure due to impacted client-side Components) in the FAQ section below.
Exposure to OpenSSL Heartbleed vulnerability described in JSA10623
Last Update: 8.00 a.m. May 6th 2014 Pacific Daylight Savings.
Refer ‘Section A’ if currently on ANY release version other than 7.4R9.1, 7.4R9.2 or 8.0R3.1
Refer ‘Section B’ if currently on 7.4R9.1 or 8.0R3.1
Refer ‘Section C’ if currently on 7.4R9.2
Section A – Applies if upgrading from ANY release other than 7.4R9.1, 7.4R9.2 or 8.0R3.1
Juniper Networks has released the following versions of software to resolve this issue on the server side and client side for its SSL VPN product family. The fixed build includes OpenSSL libraries with disabled heartbeat extension options (using the openssl option -DOPENSSL_NO_HEARTBEATS)
1. SSL VPN software version 8.0R3.2 and 7.4R9.3 are available for download from our download site
2. Junos Pulse desktop clients versions 5.0R3.1 and 4.0R9.2 are available for download from our download site (previously released Pulse Desktop 4.0R9.1 client is vulnerable and should no longer be used)
3. Junos Pulse (Mobile) for Android version 5.0R3 (44997) is available for download from Google Play Store.
4. Junos Pulse (Mobile) for Android (Samsung Variant) version 5.0R3 (44997) is available for download from Google Play Store.
5. Junos Pulse (Mobile) for Apple iOS version 5.0.3.44999 is available for download from Apple App Store.
Section B – Applies ONLY if upgrading from 7.4R9.1 or 8.0R3.1 versions.
If customers previously upgraded to 7.4R9.1 or 8.0R3.1 then the issue is resolved on server side (SSL VPN gateway device) as these release versions include openssl libraries with disabled heartbeat extension option (using the openssl option -DOPENSSL_NO_HEARTBEATS). However there may be some exposure to client components. For details on the exposure refer FAQ 1 (Exposure due to impacted client-side Components) in the FAQ section below. To resolve outstanding issues with client-side components, use the options listed below:
For Junos Pulse (Desktop) clients: Upgrade Junos Pulse clients to versions 5.0R3.1 or 4.0R9.2 using your chosen method of Junos Pulse deployment (through Web browser when users signs-in to their SSL VPN session or through software distribution infrastructure). If you previously used Pulse Client Version 4.0R9.1 – upgrade to Pulse Client 4.0R9.2.
For FIPS mode of Network Connect (windows Only) client: Upgrade your SSL VPN device to software version 8.0R3.2 or 7.4R9.3. This is because Network Connect client is tied to the server version and you have to upgrade the server to upgrade the clients.
Junos Pulse (Mobile) for Android version 5.0R3 (44997) is available for download from Google Play Store.
Junos Pulse (Mobile) for Android (Samsung Variant) version 5.0R3 (44997) is available for download from Google Play Store.
Junos Pulse (Mobile) for Apple iOS version 5.0.3.44999 is available for download from Apple App Store.
If you are not impacted by the scenarios described under FAQ # 1 (Exposure due to impacted client-side Components) then 7.4R9.1 and 8.0R3.1 will resolve the issue and you do not have to upgrade (neither the Server nor Client versions)
Section C – Applies ONLY if upgrading from 7.4R9.2
If customers previously upgraded to 7.4R9.2 then the issue is resolved on server side (SSL VPN gateway device) as these release versions include openssl libraries with disabled heartbeat extension option (using the openssl option -DOPENSSL_NO_HEARTBEATS). However there may be some exposure to Junos Pulse Desktops clients as described under FAQ # 1 (Exposure due to impacted client-side Components). To resolve outstanding issues with client-side components, use the options listed below:
1.For Junos Pulse (Desktop) clients: Upgrade Junos Pulse clients to versions 5.0R3.1 or 4.0R9.2 using your chosen method of Junos Pulse deployment (through Web browser when user signs-in to their SSL VPN session or through software distribution infrastructure). If you previously used Pulse Client Version 4.0R9.1, upgrade to Pulse Client 4.0R9.2.
2.For FIPS mode of Network Connect (windows Only) client: N/A. This client is already fixed in 7.4R9.2.
3.Junos Pulse (Mobile) for Android version 5.0R3 (44997) is available for download from Google Play Store.
4.Junos Pulse (Mobile) for Android (Samsung Variant) version 5.0R3 (44997) is available for download from Google Play Store.
5.Junos Pulse (Mobile) for Apple iOS version 5.0.3.44999 is available for download from the Apple App Store.
6.If you are not impacted by the scenarios described under FAQ # 1 (Exposure due to impacted client-side Components) then 7.4R9.2 will resolve the issue and you do not have to upgrade (neither the Server nor Client versions)
Note: 7.4R9.3 was recently released to provide a single 7.4R9 build which contains all fixes for both server and client components.
FAQ Section:
FAQ 1: Exposure due to impacted client-side Components.
Juniper SSL VPN clients components listed under ‘Client-side’ in the problem section above contain a version of impacted OpenSSL library which is used by the Juniper client components to communicate to the sever over https. As long as the client connects to a patched version of server there should be no exposure to this vulnerability due to the Juniper Client Component; neither to the client nor to the server. However if the client connects to a rogue server that is capable of exploiting this vulnerability then the client device may be exposed to this memory buffer over-read issue.
FAQ 2: Are all client Components impacted?
No. Only the client components listed under ‘client-side’ section in the problem section are affected.
FAQ 3: Should I replace the private keys on the SSL VPN gateway device?
Since the vulnerability may allow attackers to read from the process memory it is possible to obtain sensitive information such as private keys and user’s personal information as described in JSA10623, Juniper Networks recommends that customers generate new device certificates to replace the existing ones. This will effectively replace the private key that may have been compromised.
Inline with PKI best practices it is recommended that customers revoke the impacted certificate.
FAQ 4: Should I change my user and administrator passwords?
Since the vulnerability may allow attackers to read from the process memory it is possible to obtain sensitive information such as passwords. Juniper Networks recommends that customers change any password that might have been compromised. This includes user passwords and administrator passwords on the SA device and backend resources.
FAQ 5: Should I delete all my active sessions after upgrade?
Yes. A software upgrade preserves user sessions even after an upgrade. Juniper Networks recommends that customers use the ‘Delete Sessions’ option after an upgrade and delete all sessions. This option is available in the Admin GUI System menu by selecting Status > Active Users. All users and administrators will have to login again. This will generate a new session ID and also invalidate the previous session ID in the event that it was compromised.
FAQ 6: If customers previously upgraded to 7.4R9.1, 7.4R9.2 or 8.0R3.1 do they have to upgrade again to 7.4R9.3 or 8.0R3.2?
The subsequent releases are required ONLY if customers determine that they are impacted. For details refer to FAQ 1 and the affected client-side list in the ‘problem’ section above
FAQ 7: If a customer has not yet upgraded to any patched release which release versions should they upgrade to?
If the gateway devices are not yet upgraded then use 7.4R9.3 or 8.0R3.2 as described in detail under Section A above.
FAQ 8: What are the openssl versions used in vulnerable server and clients components?
Server-Side:
Secure Access software versions 7.4R1 and 7.4R2 uses openssl version 1.0.1c and 7.4R3 and above uses openssl version 1.0.1e.
Secure Access software versions 8.0R1 to 8.0R3 uses openssl version 1.0.1e
Client-Side:
Junos Pulse (Desktop) version 5.0R1 to 5.0R3 uses openssl version 1.0.1e
Junos Pulse (Desktop) 4.0R5 to 4.0R9.1 uses openssl version 1.0.1e
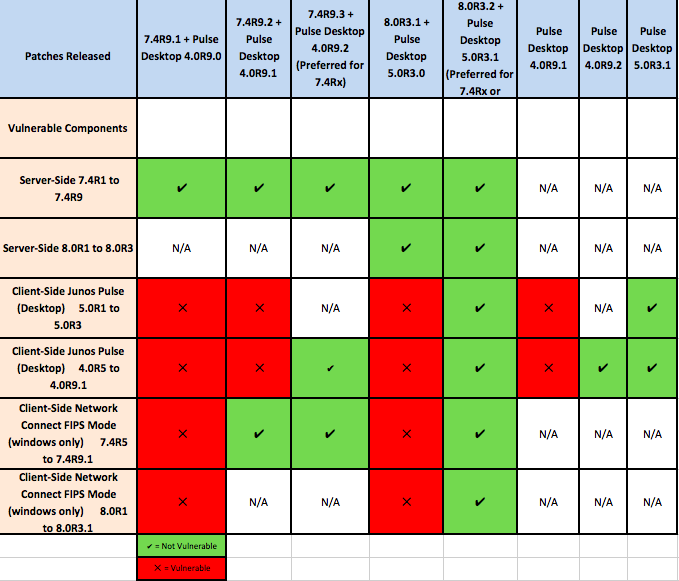
FAQ 9: The image below is a table of vulnerable components and Patches released. It is a snapshot of information provided in Section A, B and C
Table of Vulnerable Components and Patches Released