User is experiencing unexpected behavior with fragmented packets when he configures a firewall filter.
User has the following firewall filter configured.
[edit firewall family inet]
term dns-out-access {
from {
destination-port 1024-65535;
}
then accept;
}
When the server responds to the client conversations he realized the end user is not managing to establish connectivity to the server.
Upon the removal of the firewall filter we realized that the conversation is working fine.
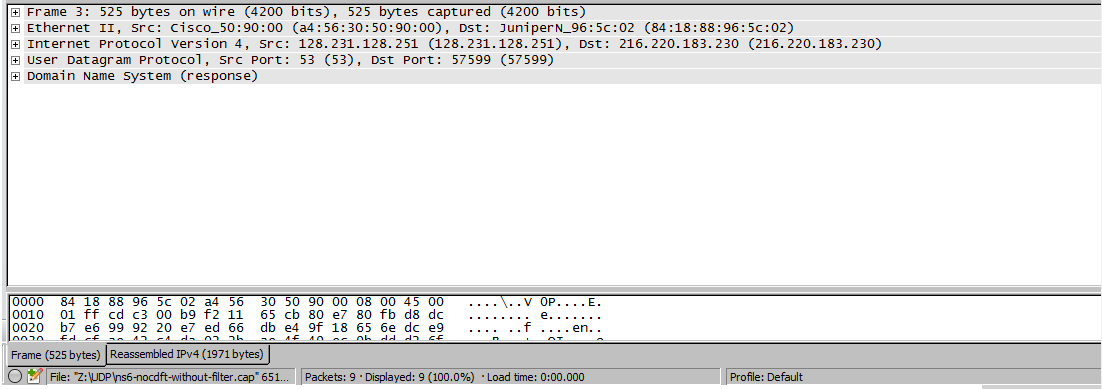
We know for certain that there is fragmentation on the way between the server and the client; and upon taking a packet capture without the firewall filter we noticed that packets have the correct destination port
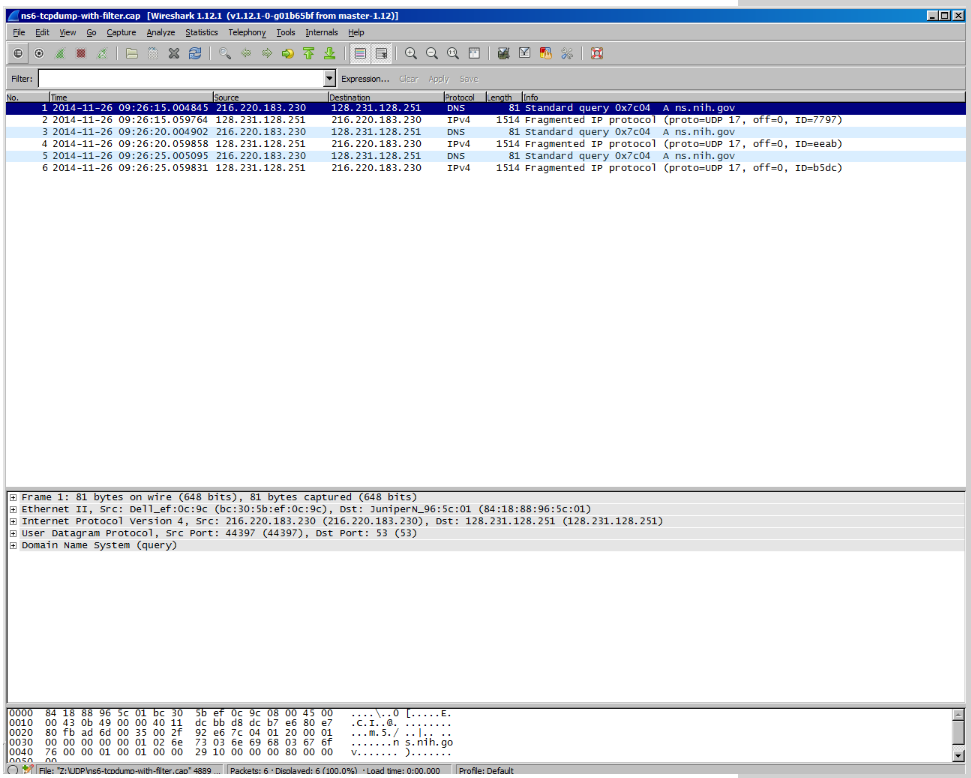
Upon the insertion of the firewall filter and taking the capture again; we noticed that the fragmented part is missing:
The reason for this behavior is that the header that we are seeing on the first capture (the one without the filter) is not real; i.e. It’s inserted by wireshark but does not actually exist in the fragment traversing the router.
The real ip behavior is that only the first fragment has the correct Layer 4 header, all the rest do not.
The header that appears to us in Wireshark is caused by a feature called Ip Reassembly that is turned on by default on newer versions of Wireshark.
This feature will analyze a TCP/IP stream and artificially add a layer 4 header to packets that belong to the same stream.
Let’s check what happens when we disable the reassembly feature:
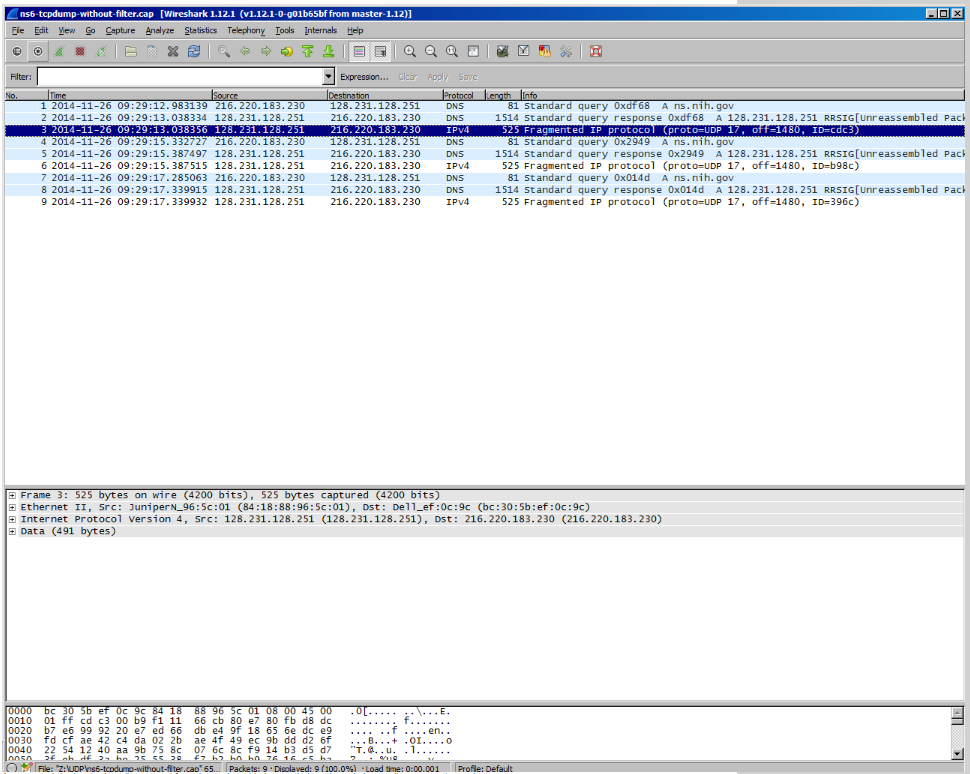
As expected the header has disappeared from the packet; this is exactly how the switch actually process the packets when trying to apply the firewall filter.
Ex-switches process firewall filters on a per-packet basis. That means that each packets is judged independently of each other packet.
When we apply the filter
[edit firewall family inet]
term dns-out-access {
from {
destination-port 1024-65535;
}
then accept;
}
We are trying to match packets going to destination ports 1024-65535; which correctly matches the first fragment, but not rest as they lack the layer 4 header to match on.
There are two different ways we can resolve this problem:
1.Eliminate packet fragmentation. This will ensure that all fragments have the correct layer 4 headers for the firewall filter to match on.
2.The second option is to alter the firewall filter so it matches on fields found in the layer 2 or layer 3 headers, as all fragments still have those headers.
I hope this articles proves to be a friendly reminder on how firewall filters work on switches and how fragments are handled by Wireshark.