Exploring SAN Security
A Storage Area Network (SAN) is a fast and reliable network that provides access to internal and external storage resources. Typically, the intra-SAN traffic does not cross any of the cables of the production network and is usually deployed in its own IP subnet and VLAN for security and performance reasons. Storage devices are shared as peer resources amongst all network servers and are not owned by any one server. A well-designed SAN exemplifies the principle of separation of services.
SAN Advantages
There are three main benefits of SANs:
- Reduced capital and operating expenses.
- Flexibility and scalability as the business grows and application requirements change.
- Greater reach for replication and backups when compared with storage devices collocated with network servers.
SAN Technologies
There are three main SAN interconnection technologies, all based on the Small Computer Systems Interface (SCSI) communications model:
- Fiber Channel. This is SCSI over a network infrastructure and has these features:
- Used for host-to-SAN connections.
- Is the primary transport technology for SANs.
- iSCSI (SCSI over TCP/IP). This is SCSI using TCP/IP for transport and has these features:
- Used for host-to-SAN connections.
- Typically used for implementing SAN connectivity in a LAN environment.
- FCIP (Fiber Channel over IP). Used to communicate fiber channel commands over IP and to interconnect SANs:
- SAN-to-SAN connections.
- Typically used in a Metropolitan Area Network (MAN) or WAN.
Understand which SAN technology is used for host-to-SAN and SAN-to-SAN connectivity.
SAN Address Vulnerabilities
There are two types of logical addresses implemented within a SAN:
- Logical Unit Number (LUN): A 64-bit field that SCSI uses to identify a logically addressable unit of a target within a SCSI device. This address can be masked through a process called LUN masking to hide physical or logical volumes from misbehaving servers but is considered unsecure because these addresses can be spoofed.
In a SAN, iSCSI volumes will definitely be “targets.” Ugly pun, but you’ll remember the terminology now, right?
- World Wide Names (WWN). A 64-bit field used by Fiber Channel to uniquely identify each element on that fiber channel network. Zoning of the fiber switch fabric (similar to VLANs) can use WWNs to assign security permissions, but this is considered unsecure because WWNs are user-configurable. This zoning capability is only possible in a fiberswitched infrastructure and not a simple fiber channel.
Virtual SANs (VSANs)
Given the relative ease of spoofing both LUNs and WWNs, existing SAN technology cannot be trusted to separate the different SANs’ data planes. With virtual SANs (VSANs):
- SAN traffic is isolated by hardware.
- A single switch can be configured with ports in multiple VSANs.
- Only ports in the same VSAN can communicate with each other.
- In a similar fashion to VLANs, a VSAN can span several switches because
all the inter-switch traffic is tagged with the VSAN membership info.
Cisco invented VSANs, although VSANs have since been adopted as an ANSI standard.
SAN Security Strategies
There are six areas to target in securing a SAN, as follows:
- SAN Management Access. Secure management services access.
- Fabric Access. Secure access of devices to fiber fabric service.
- Target Access. Secure access to LUNs and targets. Can be secured with zoning (see the next section).
- IP Storage Access. iSCSI and FCIP use IP for transport. Secure the underlying IP network. Can be secured with these features in Cisco IOS routers:
- IPSec VPNs when transiting public carriers.
- Hardware-accelerated encryption.
- Firewall filters.
- SAN Protocol. Secure FCIP, the switch-to-switch communication protocol.
- Data Integrity and Confidentiality (Secrecy). Secure data that crosses the network, as well as stored on volumes.
iSCSI has many similarities to security features that we have examined in previous chapters:
- Fiber Channel zones are similar to ACLs.
- Fiber Channel VSANs are similar to VLANs.
- Fiber Channel port security is similar to 802.1X port-based authentication.
Zoning
The main strategy for securing access to SAN targets is zoning. We saw zoning a bit earlier in the context of using user-configurable WWNs to place SAN devices in different zones. This is the same idea, but a different context. In fact, zoning to assure target access security is probably most analogous to zones in the Zone-Based Policy Firewall (ZPF) that we introduced in Chapter 5, “Using Cisco IOS Firewalls to Implement a Network Security Policy.”
There are two basic steps, as follows:
- Associate physical ports on the SAN Fiber switch with VSANs (again, much like a VLAN).
- Logically divide the VSANs into zones. Zones can be either soft or hard:
- Soft Zoning. The visibility of device IDs is restricted, although a server can still connect to a known target using its address.
- Hard Zoning. More secure than soft zoning. Access to SAN resources is physically controlled across the switch fabric. This is most commonly used.
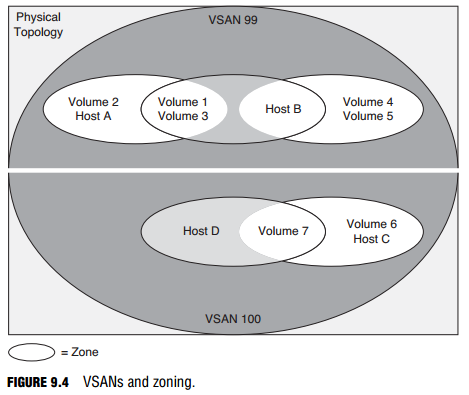
Zoning is illustrated in Figure 9.4. Two VSANs are created inside a single physical topology, with each VSAN containing more than one zone. Disks and hosts can exist across multiple zones in a single VSAN but can never span VSANs.