Constructing a Network Addressing Scheme
Subnetworks, also known as subnets, are very common in all but the smallest of network environments, segmenting the network into smaller divisions that have their own addresses. To create subnet addresses, some of the bits used for the host portion of an IP address are “borrowed” to create the subnet address. The following sections describe how subnets function and how they are computed.
Subnetworks
Network administrators often need to divide networks, especially large networks, into subnetworks, or subnets, to provide addressing flexibility. This topic describes the purposes and functions of subnets and their addressing schemes. A company that occupies a three-story building might have a network divided by floors, with each floor divided into offices. Think of the building as the network, the floors as the three subnets, and the offices as the individual host addresses.
A subnet segments the hosts within the network. With no subnets, the network has a flat topology. A flat topology has a short routing table and relies on Layer 2 MAC addresses to deliver packets. MAC addresses have no hierarchical structure. As the network grows, the use of the network bandwidth becomes less and less efficient.
The disadvantages of a flat network are as follows:
- All devices share the same bandwidth.
- All devices share the same Layer 2 broadcast domain.
- It is difficult to apply security policies because there are no boundaries between devices.
On an Ethernet network connected by hubs, every host on the same physical network sees all the packets on the network. On a switch-connected network, the host sees all broadcasts. In heavy traffic situations, on a shared segment connected by hubs, there can be many collisions caused by two or more devices transmitting simultaneously. The devices detect the collision, stop transmitting, and then begin transmitting at a random interval later. To users, this process is perceived as the network slowing down. Routers can be used in these situations to separate networks by breaking the network into multiple subnets. Figure 4-10 shows an example of a small network broken into three separate subnets.
Figure 4-10 Network Subnets

The advantages of subnetting a network are as follows:
- Smaller networks are easier to manage and map to geographical or functional requirements.
- Overall network traffic is reduced, which can improve performance.
- You can more easily apply network security measures at the interconnections between subnets than throughout the entire network.
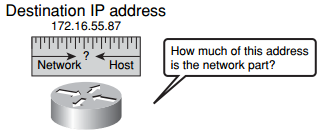
In multiple-network environments, each subnetwork can be connected to the Internet through a single router, as shown in Figure 4-10. In this example, the network is subdivided into multiple subnetworks. The actual details of the internal network environment and how the network is divided into multiple subnetworks are inconsequential to other IP networks. IP addresses provide an identifier for both the network and the host of an IP subnet. As Figure 4-11 illustrates, the router must have some way of determining how much of the address is the network portion.
Figure 4-11 Determining Network Addresses
Each device on an IP network is configured with both an IP address and a subnet mask. The subnet mask identifies the network-significant portion of an IP address. The networksignificant portion of an IP address is, simply, the part that identifies what network the host device is on (that is, the network address). This is important for the routing operation to be efficient
Two-Level and Three-Level Addresses
When the IPv4 method of identifying addresses and address classes was developed, a twolevel address (network and host) seemed sufficient. Each address class (A, B, and C) had a default mask associated with it, and because the mask was predefined, it was not necessary to explicitly configure the mask.
As the number of network-connected devices grew, it became clear that this was an inefficient use of network addresses. To overcome this problem, a third level of addressing, consisting of subnets, was developed.
A subnet address includes the original classful network portion plus a subnet field. This is also known as the extended network prefix. The subnet field and the host field are created from the original classful host portion. To create a subnet address, you can borrow bits from the original host field and designate them as the subnet field.
However, subnets cannot work without a way to identify the part of the address that is network significant and the part that is host significant. For this reason, explicit subnet masks need to be configured.
Subnet Creation
The subnet address is created by taking address bits from the host portion of Class A, Class B, and Class C addresses. Usually a network administrator assigns the subnet address locally. Like IP addresses, each subnet address must be unique.
When creating subnets, many potential individual host addresses (endpoints) are lost. For this reason, you must pay close attention to the percentage of addresses that are lost when you create subnets. The algorithm used to compute the number of subnets uses powers of 2.
When taking (borrowing) bits from the host field, it is important to note that the number of additional subnets that are being created will double each time one more bit is borrowed. Borrowing 1 bit creates two possible subnets (21 = 2). Borrowing 2 bits creates four possible subnets (22 = 4). Borrowing 3 bits creates eight possible subnets (23 = 8), and so on.
Each time another bit is borrowed from the host field, the number of possible subnets created increases by a power of 2 and the number of individual possible host addresses on each subnet decreases by a power of 2. Some examples are as follows:
- Using 1 bit for the subnet field results in 2 possible subnets (21 = 2).
- Using 2 bits for the subnet field results in 4 possible subnets (22 = 4).
- Using 3 bits for the subnet field results in 8 possible subnets (23 = 8).
- Using 4 bits for the subnet field results in 16 possible subnets (24 = 16).
- Using 5 bits for the subnet field results in 32 possible subnets (25 = 32).
- Using 6 bits for the subnet field results in 64 possible subnets (26 = 64).
In general, the following formula can be used to calculate the number of usable subnets, given the number of subnet bits used:
Number of subnets = 2s (where s is the number of subnet bits borrowed)
Computing Usable Subnetworks and Hosts
One of the decisions you must make when creating subnets is to determine the optimal number of subnets and hosts. To accomplish this, you need to understand the classes of IP networks and know how to use the bits within these classes to create networks and allocate address space for hosts. This is done by borrowing bits from the host field in a network address space.
Computing Hosts for a Class C Subnetwork
Each time 1 bit is borrowed from a host field, there is one less bit remaining in the host field that can be used for host numbers, and the number of host addresses that can be assigned decreases by a power of 2.
As an example, consider a Class C network address in which all 8 bits in the last octet are used for the host ID. Therefore, there are 256 possible numbers. The actual number of possible addresses available to assign to hosts is 254 (256 – 2 reserved addresses).
Now, imagine that this Class C network is divided into subnets. If 2 bits are borrowed from the default 8-bit host field, the size of the host field decreases to 6 bits. All possible combinations of 0s and 1s that could occur in the remaining 6 bits produce a total number of possible hosts that could be assigned in each subnet. This number, which formerly was 256, is now 64. (You “borrowed” 2 bits to make subnets from 8 host bits total in a Class C network, so with 6 bits remaining for hosts, 26 = 64.) The number of usable host numbers decreases to 62 (64 – 2).
In the same Class C network, if 3 bits are borrowed, the size of the host field decreases to 5 bits, and the total number of assignable hosts for each subnet decreases to 32 (25). The number of usable host numbers decreases to 30 (32 – 2). The number of possible host addresses that can be assigned to a subnet is related to the number of subnets that have been created. In a Class C network, for example, with 3 bits borrowed to make subnets, the usable subnets created are 8, each having 30 (25 = 32 – 2 = 30) usable host addresses. Figure 4-12 shows the number of subnets and hosts that can be computed in a Class C address space by borrowing host bits.
Figure 4-12 Borrowing Bits in a Class C Network Address Space
 As
As
Figure 4-11 illustrates, the router must have some way of determining how much of the
address is the network portion.
Computing Hosts for a Class B Subnetwork
Now consider a Class B network address, in which 16 bits are used for the network ID and 16 bits are used for the host ID. Therefore, there are 65,536 (216) possible addresses available to assign to hosts (65,534 usable addresses, after subtracting the 2 addresses, the broadcast and the subnet addresses, that cannot be used).
Now, imagine that this Class B network is divided into subnets. If 2 bits are borrowed from the default 16-bit host field, the size of the host field decreases to 14 bits. All possible combinations of 0s and 1s that could occur in the remaining 14 bits produce a total number of possible hosts that could be assigned in each subnet. Thus, the number of hosts assigned to each subnet is now 16,382.
In the same Class B network, if 3 bits are borrowed, making the mask 3 bits longer, the size of the host field decreases from 16 bits to 13 bits, because you borrowed 3 bits to make subnets, and now the total number of host addresses for each subnet decreases to 8192 (213). The number of usable host numbers decreases to 8190 (8192 – 2). In this Class B network, for example, the usable subnets created are 6 (23 = 8 – 2), each having 8190 (8192 – 2) usable host addresses. Figure 4-13 shows the number of subnets and hosts that can be computed in a Class B address space by borrowing host bits.
Figure 4-13 Borrowing Bits in a Class B Network Address Space

Computing Hosts for a Class A Subnetwork
Finally, consider a Class A network address, in which by default 8 bits are used for the network ID and 24 bits are used for the host ID. Therefore, there are 16,777,216 (224) possible addresses available to assign to hosts (16,777,214 usable addresses, after subtracting the 2 addresses, the broadcast and the subnet addresses, that cannot be used).
Now, imagine that this Class A network is divided into subnets. If 6 bits are borrowed from the default 24-bit host field, the size of the host field decreases to 18 bits. All possible combinations of 0s and 1s that could occur in the remaining 18 bits produce a total number of possible hosts that could be assigned in each subnet. This number is now 262,142, while it was formerly 16,777,216. The number of usable hosts decreases to 262,140 (262,142 – 2). Figure 4-14 shows the number of subnets and hosts that can be computed in a Class A address space by borrowing host bits.
Figure 4-14 Borrowing Bits in a Class A Network Address Space

How End Systems Use Subnet Masks
The end system uses the subnet mask to compare the network portion of the local network address with the destination network address of the packet to be sent. Before an end system can send a packet to its destination, it must first determine whether the destination address is on the local network. This is done by comparing the bits in the destination address with the network bits of the sending station. Figure 4-15 shows how host A and host B are local because their subnetwork addresses are both 10.1.1.0.
Figure 4-15 Local Hosts

Because these hosts are on the same subnet, the source end system will use the Address Resolution Protocol (ARP) process to bind the destination IP address to the destination MAC address. If it was not on the same subnet, the packet (frame) must be forwarded to the MAC address of the default gateway, the router on the subnet, for transmission to the destination network.
How Routers Use Subnet Masks
The subnet mask identifies the network-significant part of an IP address. Routers, like all IP hosts, need this information to determine how to get a packet to the desired destination. When a device determines that a packet does not belong on the local subnet (which would called off-net), it will send the packet to the router (its default gateway) on its subnet. The router must then determine where to send the packet.
All routers have routing tables. Depending on the location of the router in the network hierarchy, the table can be small and simple or large and complex. Figure 4-16 shows a packet traveling from host A to host B on different networks. As the packet travels between the adjoining networks, the routers must reference their routing tables to determine where to send the packet next.
Figure 4-16 Routing Tables

The router populates the routing table with the network-significant part of all known networks, to compare the destination network addresses of packets that need to be forwarded. If the network is not directly attached to the router, the router stores the address of the next-hop router to which the packet should be forwarded. For routers to function without the need to store all destination networks in their tables, they use a default route to which packets not matching any entry in the route table are forwarded. The following step list describes this behavior.
Step 1 Host A determines that the destination network is off-net and requires the use of its default gateway router (Router A). So host A must ARP for, and deliver the frame to, Router A.
NOTE Router A has a route to the destination network 10.3.1.0 and forwards the packet to Router B through the indicated interface.
Step 2 Because the 10.3.1.0/24 network is directly connected to Router B interface Fa0/2, Router B will use ARP to determine the MAC address of host B.
When configuring routers, each interface is connected to a different network or subnet segment. An available host address from each different network or subnet must be assigned to the interface of the router that connects to that network or subnet. In Figure 4-17, RouterA has two Ethernet interfaces one connected to the host network and one to the network connecting RouterA to RouterB.
Figure 4-17 IP Addressing on a Router Interface

The interface that is connected to the 172.16.2.0 subnetwork is assigned the IP address of 172.16.2.1, and the other interface that is connected to the 172.16.3.0 subnetwork is assigned the IP address of 172.16.3.1. All the attached hosts need to have their addresses within the range of the subnet. Any host configured with an address outside of this would not be reachable.
Mechanics of Subnet Mask Operation
Although subnet masks use the same format as IP addresses, they are not IP addresses themselves. Each subnet mask is 32 bits long, divided into four octets, and is usually represented in the dotted decimal notation like IP addresses. In their binary representation, subnet masks have all 1s in the network and subnetwork portions (on the left) and all 0s in the host portion (on the right).
There are only eight valid subnet mask values per octet. The subnet field always immediately follows the network number. That is, the borrowed bits must be the first n bits, starting with the most significant bit (MSB) of the default host field, where n is the desired size of the new subnet field. The subnet mask is the tool used by the router to determine which bits are routing (network and subnet) bits and which bits are host bits.
If all 8 bits in any octet are binary 1s, the octet has a decimal equivalent of 255. This is why there is a 255 in a decimal representation of a default subnet. In Class A, the default subnet mask is 255.0.0.0 in decimal, 11111111.00000000.00000000.00000000 in binary, and /8 in shorthand; all three mean the same thing. If the three highest-order bits (bits to the left) from the next highest-order host octet are borrowed (add three more 1s to the default mask), they add up to 224 (128 + 64 + 32). This translates to 255.224.0.0, or 11111111.11100000.00000000.00000000. Figure 4-18 shows the common values used in subnet masking.
Figure 4-18 Subnet Mask Octet Values

With IP addressing, the subnet mask identifies the network addressing information that is necessary to send packets toward their final destinations. The subnet mask identifies which bits within the IP address are the network and subnet bits.
Figure 4-19 shows the default subnet masks for Class A, Class B, and Class C addresses. The subnet mask itself is indicated with 1s in the binary notation for the mask, with all other bits indicated as 0s.
Figure 4-19 Class A, B, and C Default Subnet Masks

Applying Subnet Mask Operation
Most network administrators work with existing networks, complete with subnets and subnet masks in place. Network administrators need to be able to determine, from an existing IP address, which part of the address is the network and which part is the subnet. Applying the subnet mask operation provides this information.
The procedure described in the following steps explains how to select the number of subnets you need for a particular network and then apply a mask to implement subnets:
Step 1 Determine the IP address for your network as assigned by the registry authority. Assume that you are assigned a Class B address of 172.16.0.0.
Step 2 Based on your organization and administrative requirements and structure, determine the number of subnets required for the network. Be sure to plan for future growth. Assume that you are managing a worldwide network in 25 countries. Each country has an average of four locations. Therefore, you will need 100 subnets.
Step 3 Based on the address class and the number of subnets you selected, determine the number of bits you need to borrow from the host ID. To create 100 subnets, you need to borrow 7 bits (27 = 128).
Step 4 Determine the binary and decimal values of the subnet mask you select. For a Class B address with 16 bits in the network ID, when you borrow 7 bits, the mask is /23. Binary value of the mask:
11111111.11111111.11111110.00000000. Decimal value of the mask:
255.255.254.0.
Step 5 Apply the subnet mask for the network IP address to determine the subnet and host addresses. You will also determine the network and broadcast addresses for each subnet.
Step 6 Assign subnet addresses to specific subnets on your network.
Determining the Network Addressing Scheme
When working in a classful networking environment that uses fixed-length subnet masks, you can determine the entire network addressing based on a single IP address and its corresponding subnet mask. Figure 4-20 shows an example of the first three steps, given the following network address and mask:
- Network address: 192.168.221.37
- Subnet mask: 255.255.255.248
Figure 4-20 Determining the Addressing Scheme, Steps 1–3

After using the subnet mask to determine the significant bits used in the host address portion, you will use Steps 4 through 8 to determine the subnetwork network address, broadcast address, first host address, last host address, and next subnet address. This is illustrated in Figure 4-21.
Figure 4-21 Determining the Addressing Scheme, Steps 4–8

After converting the addresses from binary to decimal, the addresses for the subnets are as follows:
- Subnet address: 192.168.221.32
- First host address: 192.168.221.33
- Last host address: 192.168.221.38
- Broadcast address: 192.168.221.39
- Next subnet address: 192.168.221.40
Notice that the range of the address block, including the subnet address and directed broadcast address in this example, is from 192.168.221.32 through 192.168.221.39, which includes eight addresses. The address block is the same size as the number of host bits (2h = 23 = 8).
Class C Example
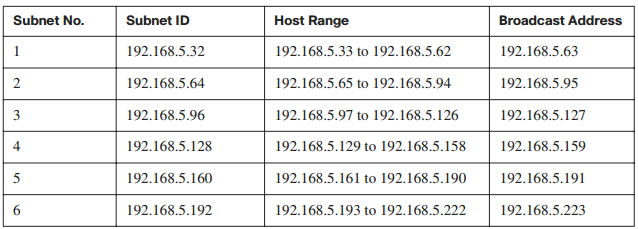
In Figure 4-22, we will determine the addressing for a Class C network with a nondefault mask. Given the address of 192.168.5.139 and knowing that the subnet mask is 255.255.255.224, the subnet number is 11111111.11111111.11111111.11100000, or /27.
Figure 4-22 Class C Addresses with Nondefault Mask

The following outlines the steps and shows the details of each operation in the eight-step process:
Step 1 Write the octet that is being split in binary (10001011).
Step 2 Write the mask bits of the same octet (11100000).
Step 3 Draw a vertical line to delineate the network-significant bits in the assigned IP address. Put a line under the mask so that you can view the significant bits in the IP address (10000000).
Step 4 Copy the significant bits four times.
Step 5 In the first line, define the network address by placing 0s in the remaining host bits (10000000).
Step 6 In the last line, define the directed broadcast address by placing all 1s in the host bits (10011111).
Step 7 In the middle lines, define the first and last host ID for this subnet: 10000001 and 10011110.
Step 8 Increment the subnet bits by 1 to determine the next subnet address.
Repeat Steps 4 through 8 for all subnets (10100000).
Table 4-3 shows the range of subnets and broadcast addresses that would be available with the given subnet mask. Note that the subnet in Figure 4-22 is subnet 4 in the following table.
Table 4-3 Subnet Addresses Table
Class B Example
In Figure 4-23, we will determine the addressing for a Class B network with a nondefault mask. Given the address of 172.16.139.46 and knowing that the subnet mask is 255.255.240.0, or /20, you can determine the subnet and host addresses for this network.
Figure 4-23 Class B Address with Nondefault Subnet Mask

The following outlines the steps and shows the details of each operation in the eight-step process:
Step 1 Write the octet that is being split in binary (10001011).
Step 2 Write the mask bits of the same octet (11110000).
Step 3 Draw a vertical line to delineate the network-significant bits in the assigned IP address. Put a line under the mask so that you can view the significant bits in the IP address (10000000).
Step 4 Copy the significant bits four times.
Step 5 In the first line, define the network address by placing 0s in the remaining host bits (10000000.00000000).
Step 6 In the last line, define the directed broadcast address by placing all 1s in the host bits (10011111.11111111).
Step 7 In the middle lines, define the first and last host ID for this subnet— 10000000.00000001 and 10011111.11111110.
Step 8 Increment the subnet bits by 1 to determine the next subnet address.
Repeat Steps 4 through 8 for all subnets (10100000.00000000).
Table 4-4 shows the range of subnets and broadcast addresses that would be available with the given subnet mask.
Table 4-4 Subnet Addresses Table

Class A Example
In Figure 4-24, we will determine the addressing for a Class A network with a nondefault mask. Given the address of 10.172.16.211 and knowing that the subnet mask is /18, you can determine the subnet and host addresses for this network.
Figure 4-24 Class A Address with Nondefault Subnet Mask

The following outlines the steps and shows the details of each operation in the eight-step process:
Step 1 Write the octet that is being split in binary (00010000).
Step 2 Write the mask bits of the same octet (11000000).
Step 3 Draw a vertical line to delineate the network-significant bits in the assigned IP address. Put a line under the mask so that you can view the significant bits in the IP address (00000000).
Step 4 Copy the significant bits four times.
Step 5 In the first line, define the network address by placing 0s in the remaining host bits (00000000.00000000).
Step 6 In the last line, define the directed broadcast address by placing all 1s in the host bits (00111111.11111111).
Step 7 In the middle lines, define the first and last host ID for this subnet—00000000.00000001 and 00111111.11111110.
Step 8 Increment the subnet bits by 1 to determine the next subnet address.
Repeat Steps 4 through 8 for all subnets (01000000.00000000).
Table 4-5 shows the range of subnets and broadcast addresses that would be available with the given subnet mask.
Table 4-5 Subnet Addresses Table