CCNP Security FAQ: Posture Assessment
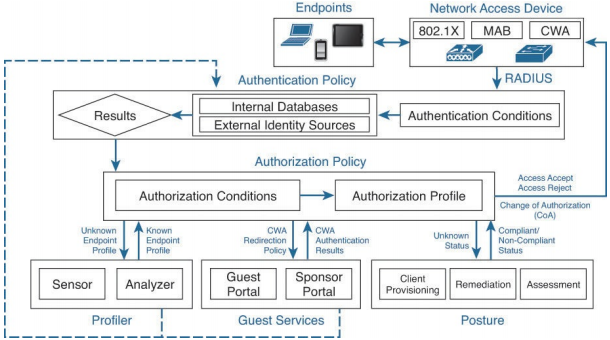
Figure: ISE authentication and authorization flow.
Q1. The Posture Service is comprised of which of the following functional components? (Select three.)
a. Profiling
b. Client provisioning
c. Authorization policy
d. Mobile device managers
e. Access lists
f. Guest Services
g. Posture Policy
Q2. What are the three possible posture outcomes following the initial connection to the network?
a. Location, Location, and Location
b. Routes, Translations, and Permissions
c. Authentication, Authorization, and Accounting
d. Compliant, Noncompliant, and Unknown
Q3. Which is a benefit of a NAC web agent versus a persistent agent?
a. The web agent provides enhanced remediation techniques.
b. The web agent does not require Administrator privileges to install.
c. The web agent provides additional firewall functionality for the endpoint.
d. The web agent can provide a greater number of Posture conditions.
Q4. True or False? The Process Check posture condition is supported on all NAC agent types.
a. True
b. False
Q5. The File condition for Posture does which of the following?
a. Checks the existence of a file
b. Checks the date of a file
c. Checks the version of a file on the client
d. All of the above
Q6. True or False? Cisco offers periodic Posture Elements updates.
a. True
b. False
Q7. The CoA process is used for which of the following?
a. To force an endpoint to reauthorize following a change in status
b. Following a change of posture compliancy from the NAC agent
c. Only after a NAD has terminated an endpoint’s connection
d. a and b
e. b and c
f. a, b, and c
Q8. When configuring the Client Provisioning Policy, you can elect each of the following except which?
a. NAC Agent Configuration
b. Network Supplicant Provisioning
c. Access list
d. Profile
Q9. Remediation is a process by which of the following occurs?
a. An endpoint that is not compliant with security policy can become compliant.
b. ISE communicates to the ASA firewall to block known attackers.
c. ISE confirms the identity of the end user based on the associated endpoint.
Q10. Which remediation type is available on a Macintosh OS X endpoint?
a. Automatic Launch Program Remediation
b. Manual Antispyware remediation
c. File Remediation
d. Manual Antivirus Remediation