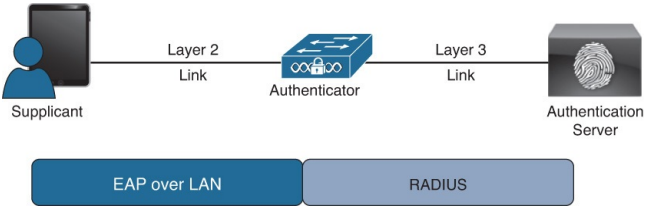
CCNP Security FAQ: EAP Over LAN (Also Known As 802.1X)
Q1. Which of the following is true?
a. The authenticator decides whether the supplicant is allowed on the network.
b. The EAP communication occurs between the supplicant and the authentication server.
c. The supplicant uses RADIUS to communicate the user’s identity to the authentication server.
d. The authenticator uses EAP to send the user’s credentials to the authentication server.
Q2. Which supplicant(s) is capable of EAP chaining?
a. Windows Native Supplicant
b. Cisco AnyConnect NAM
c. Cisco Secure Services Client (CSSC)
d. Odyssey Client
Q3. What is the purpose of an outer identity?
a. The outer identity is used for dual-factor authentications such as a username/password combined with a one-time password (OTP).
b. The outer identity provides a mechanism to modify the actual identity of the end user or device to allow for identity spoofing.
c. The outer identity provides a mechanism to authenticate the identity of the endpoint during the tunnel establishment phase.
d. The outer identity represents the machine, whereas the inner identity represents the user during EAP chaining.
Q4. True or False? IEEE 802.1X may use TACACS+ to communicate the EAP identity to the authentication server.
a. True
b. False
Q5. True or False? The supplicant is required to trust the certificate of the authentication server before it will form the TLS tunnel within which the EAP transaction will occur.
a. True
b. False
Q6. What is the name of the “secure cookie” used with EAP-FAST that can be used in lieu of a certificate, or even in addition to a certificate?
a. Protected password file (PPF)
b. Shadow credential file (SCF)
c. Private authorization credential (PAC)
d. Protected access credential (PAC)
Q7. True or False? MSCHAPv2 may be used to perform machine authentication with an LDAP connection to Active Directory.
a. True
b. False
Q8. True or False? A machine authentication may use EAP-FAST.
a. True
b. False
Q9. What are the three main components of IEEE 802.1X?
a. Agent, broker, authentication server
b. Supplicant, authorizer, authorization server
c. Authentication server, supplicant, authenticator
d. EAP, RADIUS, TLS
Q10. True or False? A tunneled EAP type is able to use native EAP types as its inner method.
a. True
b. False