CCNP Security FAQ: Authentication Policies
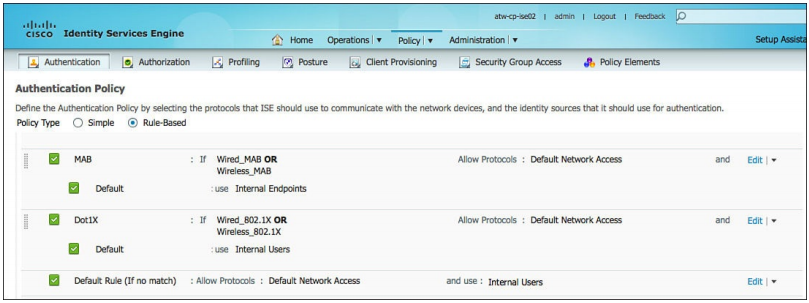
Figure: Default authentication policy.
Q1. Which of the following is required to perform MAB from a Cisco network device?
a. The RADIUS packet must have the service-type set to login and the calledstation-id populated with the MAC address of the endpoint.
b. The RADIUS packet must have the service-type set to Call-Check and the calling-station-id populated with the MAC address of the endpoint.
c. The RADIUS packet must have the service-type set to Call-Check and the calledstation-id populated with the MAC address of the endpoint
d. The RADIUS packet must have the service-type set to login and the callingstation-id populated with the MAC address of the endpoint
Q2. Which EAP type is capable of performing EAP chaining?
a. PEAP
b. EAP-FAST
c. EAP-TLS
d. EAP-MD5
Q3. Which of the following choices are purposes of an authentication policy?
a. To permit or deny access to the network based on the incoming authentication request
b. To apply access control filters, such as dACL or security group tags (SGTs), to the network device to limit traffic
c. To drop requests using an incorrect authentication method, route authentication requests tothe correct identity store, validate the identity, and “pass” successful authentications over to the authorization policy
d. To terminate encrypted tunnels for purposes of remote access into the network
Q4. True or False? You must select Detect PAP as Host Lookup to enable MAB requests for Cisco nNetwork devices.
a. True
b. False
Q5. True or False? Policy conditions from attribute dictionaries can be saved as conditions inline while building authentication policies.
a. True
b. False
Q6. Which method will work effectively to allow a different Identity store to be selected for each EAP type used?
a. This is not possible because the first rule to match 802.1X will be used and no further rules can be used.
b. Create one authentication rule that matches a service type framed for each of the EAP protocols. Each authentication rule should have one subrule that matches the EapAuthentication (such as EAP-TLS, EAP-FAST, and so on).
c. This is only possible for the main EAP types. If there is an inner method of EAP-MSCHAPv2 with PEAP, it must be sent to the same identity store as the EAP-MSCHAPv2 inner method of EAP-FAST.
d. Create one sub-rule for each EAP type under the default 802.1X authentication rule that points to the appropriate identity store per rule.
Q7. Which RADIUS attribute is used to match the SSID?
a. calling-station-ID
b. source-wireless-SSID
c. framed-station-ID
d. called-station-ID
Q8. Which RADIUS attribute contains the MAC address of the endpoint?
a. calling-station-ID
b. source-wireless-SSID
c. framed-station-ID
d. called-station-ID
Q9. What is the purpose of the continue option of an authentication rule?
a. The continue option is used to send an authentication down the list of rules in an authentication policy until there is a match.
b. The continue option sends an authentication to the next sub-rule within the same authentication rule.
c. The continue option is used to send an authentication to the authorization policy, even if the authentication was not successful.
d. The continue option will send an authentication to the selected identity store.
Q10. True or False? The Drop option for an authentication rule will allow ISE to act as if it were not “alive” so the network device will no longer send authentication requests to that ISE server.
a. True
b. False