CCNA 200-125 Exam: Security Questions With Answers
Question 1. Which statement about RADIUS security is true?
A. It supports EAP authentication for connecting to wireless networks.
B. It provides encrypted multiprotocol support.
C. Device-administration packets are encrypted in their entirety.
D. It ensures that user activity is fully anonymous.
RADIUS provides authentication, authorization, and accounting (AAA) services in network environments. When users attempt to access a network device, a RADIUS server verifies that the user is legitimate (authentication). The RADIUS server can then assign certain levels of access to network resources (authorization). Finally, the RADIUS server keeps track of how long that user stayed connected and how much data the user sent or received (accounting).
Question 2. Which condition indicates that service password-encryption is enabled?
A. The local username password is in clear text in the configuration.
B. The enable secret is in clear text in the configuration.
C. The local username password is encrypted in the configuration.
D. The enable secret is encrypted in the configuration.
Service password-encryption affects plain text passwords such as the line passwords or the enable password. This feature uses a simple substitution method to create a “secure” non-text password displayed in the configuration.
Question 3. Which command can you enter to configure a local username with an encrypted password and EXEC mode user privileges?
A. Router(config)#username jdone privilege 1 password 7 08314D5D1A48
B. Router(config)#username jdone privilege 1 password 7 PASSWORD1
C. Router(config)#username jdone privilege 15 password 0 08314D5D1A48
D. Router(config)#username jdone privilege 15 password 0 PASSWORD1
Question 4. Which command sets and automatically encrypts the privileged enable mode password?
A. enable password c1sco
B. secret enable c1sco
C. password enable c1sco
D. enable secret c1sco
Question 5. The enable secret command is used to secure access to which CLI mode?
A. user EXEC mode
B. global configuration mode
C. privileged EXEC mode
D. auxiliary setup mode
Question 6. Refer to the exhibit. What is the result of setting the no login command?
Router#config t
Router(config)#line vty 0 4
Router(config-line)#password c1sc0
Router(config-line)#no login
A. Telnet access is denied.
B. Telnet access requires a new password at the first login.
C. Telnet access requires a new password.
D. no password is required for telnet access.
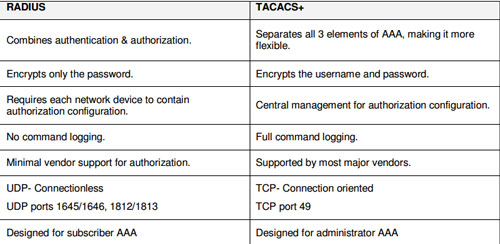
Question 7. What is a difference between TACACS+ and RADIUS in AAA?
A. Only TACACS+ allows for separate authentication.
B. Only RADIUS encrypts the entire access-request packet.
C. Only RADIUS uses TCP.
D. Only TACACS+ couples authentication and authorization.
Question 8. Which protocol authenticates connected devices before allowing them to access the LAN?
A. 802.1d
B. 802.11
C. 802.1w
D. 802.1x
Question 9. Which three options are benefits of using TACACS+ on a device? (Choose three)
A. It ensures that user activity is untraceable.
B. It provides a secure accounting facility on the device.
C. device-administration packets are encrypted in their entirely.
D. It allows the user to remotely access devices from other vendors.
E. It allows the users to be authenticated against a remote server.
F. It supports access-level authorization for commands.
Question 10. A security administrator wants to profile endpoints and gain visibility into attempted authentications. Which 802.1x mode allows these actions?
A. Monitor mode
B. High-Security mode
C. Low-impact mode
D. Closed mode
Question 11. What should be part of a comprehensive network security plan?
A. Allow users to develop their own approach to network security
B. Physically secure network equipment from potential access by unauthorized individuals
C. Encourage users to use personal information in their passwords to minimize the likelihood of passwords being forgotten
D. Delay deployment of software patches and updates until their effect on end-user equipment is well known and widely reported
E. Minimize network overhead by deactivating automatic antivirus client updates
Question 12. Which password types are encrypted?
A. SSH
B. Telnet
C. enable secret
D. enable password
Question 13. How do you maintain security in multiple websites?
A. VPN
B. DMVPN
C. other
D. other
Question 14. Which of the following encrypts the traffic on a leased line?
A. telnet
B. ssh
C. vtp
D. vpn
E. dmvpn
Question 15. Which command is necessary to permit SSH or Telnet access to a Cisco switch that is otherwise configured for these vty line protocols?
A. transport type all
B. transport output all
C. transport preferred all
D. transport input all
Question 16. How to verify SSH connections were secured?
A. ssh -v 1 -l admin IP
B. ssh -v 2 -l admin IP
C. ssh -l admin IP
D. ssh -v 2 admin IP
More Resources