VLAN Hopping Attacks
Be sure to review basic virtual LAN (VLAN) and IEEE 802.1Q trunk configuration and operation from the prerequisite CCNA material.
VLAN hopping attacks occur when an attacker tricks a switch into allowing traffic to hop to a different VLAN than the VLAN assigned to the port to which they are connected. Normally, routers are required to route traffic between VLANs at layer 3.
Recall “router-on-a-stick” and inter-VLAN routing from your CCNA studies. For traffic to move between VLANs, it needs to be routed either by a router integral to the switch, or by an external router attached to the switch by a trunk port. When diagramming the latter scenario, the router appears connected to the switch by a stick, hence the term “routeron-a-stick.” VLAN hopping attacks break this rule, and trick the switch to allow traffic that arrives on a switch port to hop to a different VLAN without involving a router.
Allowing traffic to hop to a different VLAN is very dangerous; if an attacker can fool the switch into revealing traffic from another VLAN, sensitive information carried in cleartext, such as passwords, may be obtained. For example, an attacker might be able to hop into the management VLAN, a mission-critical traffic plane whose use we first examined in Figure 4-1, our reference network diagram in Chapter 4, “Implementing Secure Management and Hardening the Router.” This is ironic because, according to Cisco, the three main advantages of VLANS are as follows:
- Segmentation
- Flexibility
- Security
The first and third points are related. By segmenting a network into different virtual broadcast domains, security is achieved; under normal operations, a user connected to a switch port is able to see only the following traffic and only in their VLAN:
- Unicast traffic: These are frames destined to the user’s PC.
- Flooded traffic: These are frames that are forwarded out all but the originating interface and consist of the following:
- Unknown unicast frames
- Majority of multicast frames
- Broadcast frames
We examine two common VLAN hopping attacks, as follows:
- VLAN hopping by rogue trunk
- VLAN hopping by double tagging
VLAN Hopping by Rogue Trunk
VLAN hopping by rogue trunk is one of the simplest attacks to explain and also one of the simplest to mitigate. A rogue trunk (like a rogue access point) is where an attacker sets up an unauthorized trunk on the switch port to which they are connected. Trunks (either Cisco ISL or IEEE 802.1Q) carry traffic from all VLANs by default. Add to this the fact that Cisco switch ports will auto-negotiate trunking, and you have a problem. Here is how such an attack might be performed:
- An attacker needs just to trick the switch into negotiating a trunk by using the signaling protocol for automatic trunk negotiation, Dynamic Trunking
Protocol (DTP). The attacker connects a rogue switch to an unused switch port and spoofs DTP messages to automatically negotiate and thus turn on trunking between the rogue switch and the victim switch. - The attacker can now send traffic into the network tagged with the VLAN ID of a VLAN that has been learned from the trunk.
VLAN Hopping by Rogue Trunk Attack Mitigation
Attack mitigation is simple:
- Turn off trunking on ports unless they specifically need it:
Catalyst1(config-if)#switchport mode access - Disable DTP on the remaining ports that require trunking and manually enable trunking on them:
Catalyst1(config-if)#switchport mode trunk Catalyst1(config-if)#switchport nonegotiate
VLAN Hopping by Double-Tagging
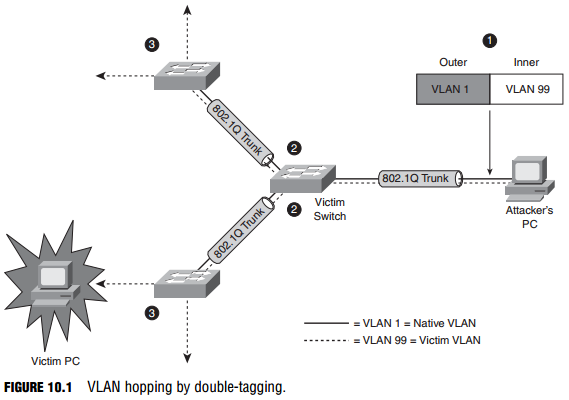
This is sometimes also called a double encapsulation attack. This type of attack leverages how the switch hardware works. Figure 10.1 illustrates the attack.
When most switches receive a frame with 802.1Q encapsulation (indicated by its Ethertype), they unencapsulate them only once, assuming (correctly) that normally 802.1Q frames have only one frame tag in them.
The following is a detailed explanation of the numbered steps in Figure 10-1:
- Knowing that the switch will only unencapsulate 802.1Q frames once, the attacker will send broadcast or unicast traffic into the switch, hiding a tagged 802.1Q frame inside another tagged 802.1Q frame. For example, VLAN 99 might be hidden inside VLAN 1. There is some guesswork involved in this attack; once the outer 802.1Q frame has been stripped of its tag, the inner frame will only travel in a trunk (to another switch) whose native VLAN is the same as the VLAN tag of the outer 802.1Q frame.
- Because this native VLAN traffic is not tagged (per the 802.1Q protocol), the inner frame is transmitted in trunks to neighbor switches of the victim switch.
- All the victim switch’s neighbors see is an 802.1Q frame tagged with VLAN 99, and they do what switches do: They examine the VLAN tag, and if the frame is a broadcast, it is flooded to all ports and trunks in that VLAN. If the frame is a unicast, and the entry is in the switch’s Content Addressable Memory (CAM) table, it is forwarded just to the port where the victim host is connected. (Figure 10-1 illustrates what happens when an unknown unicast is flooded.)
Both types of VLAN hopping attacks are only possible when the switch’s ports are misconfigured.
VLAN Hopping by Double-Tagging Attack Mitigation
A double-tagging VLAN hopping attack is unidirectional and works only if the attacker and the trunk port(s) are in the same native VLAN. The best way to prevent this type of attack is to make sure that the native VLAN of the trunked ports is different than any of the users’ ports (VLAN 10, for example):
Catalyst1(config-if) switchport trunk native vlan 10