How multipoint tunnel interface can be used to avoid configuring multiple virtual router for individual ipsec vpn tunnel interface st0.x
Assume a customer has a network setup like below and he wants to use route based ipsec vpn.
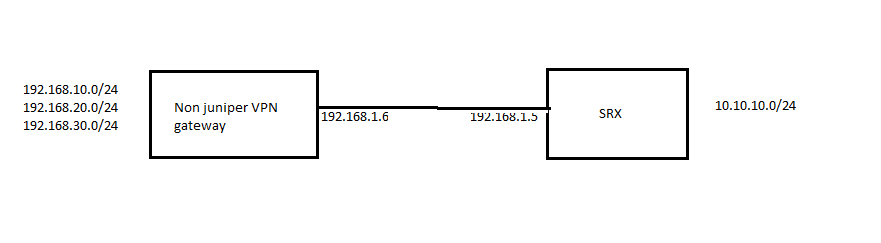
Since there are multiple subnets behind peer device we need to create multiple ipsec vpn on srx, for ex 3 in this case.
This will cause problems in routing traffic for destination 10.10.10.0/24 from srx as it will have three next hop st0.0, st0.1, st0.2 .
One way to avoid this routing problem is to use virtual router for every st0.x interface and use one static route in each vr.
But it will require a lot of configuration changes and route sharing between LAN VR’s and st0.x interface VR’s.
There is a simple solution to this using a single multipoint st0.x interface as described below.
Below are the main points that we need to keep in mind while configuring multipoint route based vpn .
1.configure a numbered multipoint st0.x interface and configure next hop tunnel binding.
set interfaces st0 unit 0 multipoint
set interfaces st0 unit 0 family inet address 1.1.1.254/24
2.use next hop tunnel binding for routing traffic over related ipsec vpn where next-hop-tunnel addresses are dummy ip addresses used to bind traffic to specific vpn.
set interfaces st0 unit 0 family inet next-hop-tunnel 1.1.1.1 ipsec-vpn mumbai_vpn1
set interfaces st0 unit 0 family inet next-hop-tunnel 1.1.1.2 ipsec-vpn mumbai_vpn2
set interfaces st0 unit 0 family inet next-hop-tunnel 1.1.1.3 ipsec-vpn mumbai_vpn3
Note: It’s not necessary that remote end device should have a numbered tunnel interface with ip address as next-hop-tunnel address. These are dummy ip addresses solely used by srx in differentiating traffic for specific vpn . Make sure that you configure dummy ip addresses from the same subnet as st0.x interface ip otherwise route for remote subnet will not be active in routing table.
3.Configure route for remote subnet with next hop address same as next-hop-tunnel address.
set routing-options static route 192.168.10.0/24 next-hop 1.1.1.1
set routing-options static route 192.168.20.0/24 next-hop 1.1.1.2
set routing-options static route 192.168.30.0/24 next-hop 1.1.1.3
Complete VPN configuration as follows.
set interfaces st0 unit 0 multipoint
set interfaces st0 unit 0 family inet next-hop-tunnel 1.1.1.1 ipsec-vpn mumbai_vpn1
set interfaces st0 unit 0 family inet next-hop-tunnel 1.1.1.2 ipsec-vpn mumbai_vpn2
set interfaces st0 unit 0 family inet next-hop-tunnel 1.1.1.3 ipsec-vpn mumbai_vpn3
set interfaces st0 unit 0 family inet address 1.1.1.254/24
set security ike policy ike_policy mode main
set security ike policy ike_policy proposal-set standard
set security ike policy ike_policy pre-shared-key ascii-text “$9$RidcrKX7V4aUM8aUjH5TRhS”
set security ike gateway mumbai ike-policy ike_policy
set security ike gateway mumbai address 192.168.1.6
set security ike gateway mumbai external-interface ge-0/0/0.0
set security ipsec policy ipsec_policy proposal-set standard
set security ipsec vpn mumbai_vpn1 bind-interface st0.0
set security ipsec vpn mumbai_vpn1 ike gateway mumbai
set security ipsec vpn mumbai_vpn1 ike proxy-identity local 10.10.10.0/24
set security ipsec vpn mumbai_vpn1 ike proxy-identity remote 192.168.10.0/24
set security ipsec vpn mumbai_vpn1 ike ipsec-policy ipsec_policy
set security ipsec vpn mumbai_vpn1 establish-tunnels immediately
set security ipsec vpn mumbai_vpn2 bind-interface st0.0
set security ipsec vpn mumbai_vpn2 ike gateway mumbai
set security ipsec vpn mumbai_vpn2 ike proxy-identity local 10.10.10.0/24
set security ipsec vpn mumbai_vpn2 ike proxy-identity remote 192.168.20.0/24
set security ipsec vpn mumbai_vpn2 ike ipsec-policy ipsec_policy
set security ipsec vpn mumbai_vpn2 establish-tunnels immediately
set security ipsec vpn mumbai_vpn3 bind-interface st0.0
set security ipsec vpn mumbai_vpn3 ike gateway mumbai
set security ipsec vpn mumbai_vpn3 ike proxy-identity local 10.10.10.0/24
set security ipsec vpn mumbai_vpn3 ike proxy-identity remote 192.168.30.0/24
set security ipsec vpn mumbai_vpn3 ike ipsec-policy ipsec_policy
set security ipsec vpn mumbai_vpn3 establish-tunnels immediately
set routing-options static route 192.168.10.0/24 next-hop 1.1.1.1
set routing-options static route 192.168.20.0/24 next-hop 1.1.1.2
set routing-options static route 192.168.30.0/24 next-hop 1.1.1.3
set security zones security-zone vpn interfaces st0.0
Verification:
root@HQ# run show security ike sa Index State Initiator cookie Responder cookie Mode Remote Address 5514212 UP df240f9322289063 a098d005f73a9cd7 Main 192.168.1.6 [edit] root@HQ# run show security ipsec sa Total active tunnels: 3 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <131073 ESP:3des/sha1 a7c2e5d3 3406/ unlim - root 500 192.168.1.6 >131073 ESP:3des/sha1 a7a256a1 3406/ unlim - root 500 192.168.1.6 <131074 ESP:3des/sha1 e70531af 3406/ unlim - root 500 192.168.1.6 >131074 ESP:3des/sha1 e3916253 3406/ unlim - root 500 192.168.1.6 <131075 ESP:3des/sha1 eafc8684 3406/ unlim - root 500 192.168.1.6 >131075 ESP:3des/sha1 f5ec7a57 3406/ unlim - root 500 192.168.1.6 [edit] root@HQ# run show security ipsec sa detail ID: 131073 Virtual-system: root, VPN Name: mumbai_vpn1 Local Gateway: 192.168.1.5, Remote Gateway: 192.168.1.6 Local Identity: ipv4_subnet(any:0,[0..7]=10.10.10.0/24) Remote Identity: ipv4_subnet(any:0,[0..7]=192.168.10.0/24) Version: IKEv1 DF-bit: clear Bind-interface: st0.0 Port: 500, Nego#: 6, Fail#: 0, Def-Del#: 0 Flag: 600a29 Tunnel Down Reason: Delete payload received Direction: inbound, SPI: a7c2e5d3, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 3403 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 2765 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service: counter-based enabled, Replay window size: 64 Direction: outbound, SPI: a7a256a1, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 3403 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 2765 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service: counter-based enabled, Replay window size: 64 ID: 131074 Virtual-system: root, VPN Name: mumbai_vpn2 Local Gateway: 192.168.1.5, Remote Gateway: 192.168.1.6 Local Identity: ipv4_subnet(any:0,[0..7]=10.10.10.0/24) Remote Identity: ipv4_subnet(any:0,[0..7]=192.168.20.0/24) Version: IKEv1 DF-bit: clear Bind-interface: st0.0 Port: 500, Nego#: 6, Fail#: 0, Def-Del#: 0 Flag: 600a29 Tunnel Down Reason: Delete payload received Direction: inbound, SPI: e70531af, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 3403 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 2796 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service: counter-based enabled, Replay window size: 64 Direction: outbound, SPI: e3916253, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 3403 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 2796 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service: counter-based enabled, Replay window size: 64 ID: 131075 Virtual-system: root, VPN Name: mumbai_vpn3 Local Gateway: 192.168.1.5, Remote Gateway: 192.168.1.6 Local Identity: ipv4_subnet(any:0,[0..7]=10.10.10.0/24) Remote Identity: ipv4_subnet(any:0,[0..7]=192.168.30.0/24) Version: IKEv1 DF-bit: clear Bind-interface: st0.0 Port: 500, Nego#: 6, Fail#: 0, Def-Del#: 0 Flag: 600a29 Tunnel Down Reason: Delete payload received Direction: inbound, SPI: eafc8684, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 3403 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 2769 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service: counter-based enabled, Replay window size: 64 Direction: outbound, SPI: f5ec7a57, AUX-SPI: 0 , VPN Monitoring: - Hard lifetime: Expires in 3403 seconds Lifesize Remaining: Unlimited Soft lifetime: Expires in 2769 seconds Mode: Tunnel(0 0), Type: dynamic, State: installed Protocol: ESP, Authentication: hmac-sha1-96, Encryption: 3des-cbc Anti-replay service: counter-based enabled, Replay window size: 64 root@HQ# run show security flow session protocol icmp Session ID: 4395, Policy name: default-policy-00/2, Timeout: 2, Valid In: 10.10.10.2/1 --> 192.168.10.1/2500;icmp, If: ge-0/0/1.0, Pkts: 1, Bytes: 84 Out: 192.168.10.1/2500 --> 10.10.10.2/1;icmp, If: st0.0, Pkts: 1, Bytes: 84 Session ID: 4431, Policy name: default-policy-00/2, Timeout: 2, Valid In: 10.10.10.2/2 --> 192.168.20.1/2501;icmp, If: ge-0/0/1.0, Pkts: 1, Bytes: 84 Out: 192.168.20.1/2501 --> 10.10.10.2/2;icmp, If: st0.0, Pkts: 1, Bytes: 84 Session ID: 4483, Policy name: default-policy-00/2, Timeout: 2, Valid In: 10.10.10.2/6 --> 192.168.30.1/2502;icmp, If: ge-0/0/1.0, Pkts: 1, Bytes: 84 Out: 192.168.30.1/2502 --> 10.10.10.2/6;icmp, If: st0.0, Pkts: 1, Bytes: 84