CCNP Security FAQ: Identity Management
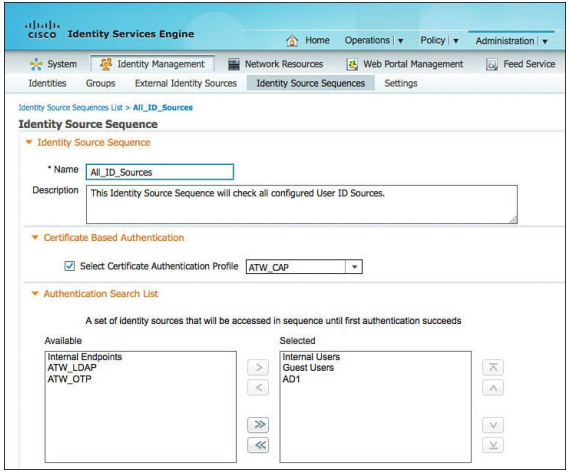
Figure ISE identity source sequence configuration
Q1. What are two types of identities used in Cisco Identity Service Engine?
a. SSID
b. MAC address
c. Username
d. IP address
Q2. What are the two general types of identity stores used by Cisco ISE?
a. Temporary
b. External
c. Internal
d. Permanent
Q3. Cisco ISE internal identity stores are used to authentication which two of the following?
a. Endpoints
b. AD security groups
c. RADIUS
d. Users
Q4. Which identity store attributes can be used in an ISE authorization policy? (Choose two.)
a. User
b. Time
c. Accounting
d. Machine
Q5. What is an individual identity store called?
a. Authentication source
b. Identity database
c. Identity source
d. Authentication database
Q6. How is an identity source sequence processed?
a. Bottom to top
b. Left to right
c. Top to bottom
d. No particular order
Q7. Which of the following identity stores are supported by ISE for authentication? (Choose three.)
a. LDAP
b. TACACS
c. Microsoft Active Directory
d. RADIUS servers
Q8. Which of the following can be used with an internal identity store?
a. SSID
b. Guest login
c. Administration
d. MAB
Q9. What are the two types of internal identity stores used in ISE?
a. User database
b. Endpoint database
c. System database
d. Admin database
Q10. What are the two primary reasons for using external identity stores?
a. Performance
b. Monitoring
c. Scalability
d. Management