CCNA FAQ: Virtual Private Networks
Q1. Your organization has just opened a new office in Detroit. You have existing offices in Phoenix, San Diego, and Albuquerque that are tied together using VPN technology. What physical or logical changes should you add to support the VPN connection to the new office?
A. No new interfaces are needed. The VPN configuration needs only to be applied to the router.
B. No new interfaces are needed. You need to communicate with the ISP to provision a new DLCI.
C. A new serial interface needs to be added to the router to support the new connection. The encapsulation should be set to match the service provider’s requirements.
D. A new Fast Ethernet interface needs to be added to the router to support the new connection. You must communicate with the service provider to provision the new circuit.
Q2. Which of the following is not a valid benefit of using VPN technology?
A. Lower costs
B. More flexibility when configuring site-to-site connections
C. The ability to support telecommuters
D. Lower network overhead
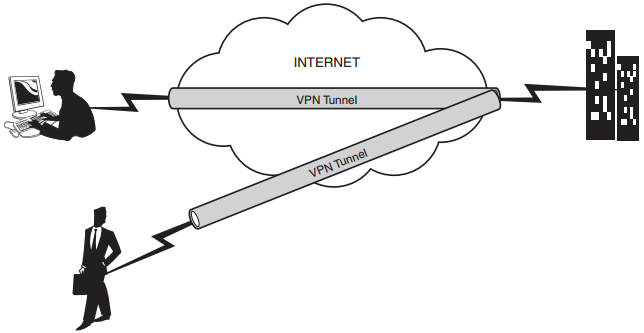
FIGURE: Remote-access VPN technology.
Q3. What is needed to support an SSL VPN connection?
A. The router should be configured to support SSL VPN connections. The client can connect using a standard web browser.
B. The router should be configured to support SSL VPN connections. The client must use the Cisco VPN client when connecting.
C. The router should be configured to support SSL VPN connections. The client must use a third-party thin client to connect.
D. The router does not need to be configured to support SSL VPN connections. The client platform delivers all configuration when it connects.
Q4. What platforms can support site-to-site and remote-access VPNs? (Choose two)
A. Cisco IOS
B. Cisco IPS Appliance
C. Cisco Catalyst 3550
D. Cisco ASA 5500
Q5. Which of the following is not a component of the IPsec framework?
A. ESP
B. SHA-1
C. TCP
D. MD5
E. AES
Q6. Which of the following represent data integrity algorithms? (Choose two)
A. AES
B. MD5
C. DES
D. 3DES
E. SHA-1
Q7. Which of the following are symmetric encryption algorithms? (Choose two)
A. DH
B. SHA-1
C. DES
D. AES
Q8. You have just finished proposing a new VPN solution to your organization’s upper management. They have approved the solution, provided that you use the strongest level of encryption possible. What algorithm will you choose?
A. 3DES
B. AES
C. SHA-1
D. MD5
Q9. You would like to implement IPsec over your LAN network. You are not as interested in encryption features, because they can cause tremendous overhead, but you would like to implement authentication and data integrity features. What IPsec protocol will you use?
A. AH
B. DH
C. ESP
D. SHA-1
Q10. What process passes data through a mathematical algorithm to generate a 128- or 160-bit result?
A. Encryption
B. Diffie-Hellman
C. Hashing
D. ESP
Q11. What are the three benefits of using VPN connectivity over private lines?
Q12. Describe the two types of VPN implementations. What would be an ideal use of each?
Q13. The three primary security techniques used over VPN connections are encryption, authentication, and data integrity. Briefly describe the purpose of each.
Q14. What are the differences between asymmetric and symmetric encryption?
Q15. Briefly describe how SSL can securely send an encryption/decryption key over a public network.
Q16. Which of the following terms refers to a VPN that uses the Internet to connect the sites of a single company, rather than using leased lines or Frame Relay?
a. Intranet VPN
b. Extranet VPN
c. Access VPN
d. Enterprise VPN
Q17. Which of the following are not considered to be desirable security goals for a site-tosite VPN?
a. Message integrity checks
b. Privacy (encryption)
c. Antivirus
d. Authentication
Q18. Which of the following functions could be performed by the IPsec IP Authentication Header? (Choose two answers.)
a. Authentication
b. Encryption
c. Message integrity checks
d. Anti-reply
Q19. Which of the following is considered to be the best encryption protocol for providing privacy in an IPsec VPN as compared to the other answers?
a. AES
b. HMAC-MD5
c. HMAC-SHA-1
d. DES
e. 3DES
Q20. Which three of the following options would be the most commonly used options for newly purchased and installed VPN components today? (Choose three answers.)
a. ASA
b. PIX firewall
c. VPN concentrator
d. Cisco router
e. Cisco VPN client
Q21. When using the Cisco Web VPN solution, with the client using a normal web browser without any special client software, which of the following are true? (Choose two answers.)
a. The user creates a TCP connection to a Web VPN server using SSL.
b. If the user connects to a normal web server inside the enterprise, and that server only supports HTTP and not SSL, those packets pass over the Internet unencrypted.
c. The Web VPN server connects to internal web servers on behalf of the Web VPN client, translating between HTTP and SSL as need be.
d. The Web VPN client cannot connect without at least thin-client SSL software installed on the client.
[mks_button size=”medium” title=”CCNA Frequently Asked Questions” style=”squared” url=”https://www.configrouter.com/cisco-certified-network-associate-faq/” target=”_blank” bg_color=”#000000″ txt_color=”#FFFFFF” icon=”” icon_type=”” nofollow=”0″] [mks_button size=”medium” title=”CCNA Exam Questions with Explanation” style=”squared” url=”https://www.configrouter.com/ccna-online-training/” target=”_blank” bg_color=”#000000″ txt_color=”#FFFFFF” icon=”” icon_type=”” nofollow=”0″]