Host Checking with Machine Certificate verification (using OpenSSL for certification).
Configure Host Checker to verify Machine Certificate.
Note: The commands in the procedure below are executed on a Windows machine using the
openssl.cnf file
. If you are running OpenSSL on a Unix machine, remove –
config C:\OpenSSL-Win32\bin\openssl.cnf
from the command.
Create a Certificate Authority using OpenSSL (3 steps)
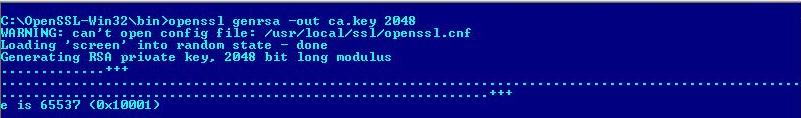
1. Create CA Private Key.
openssl genrsa -out ca.key 2048
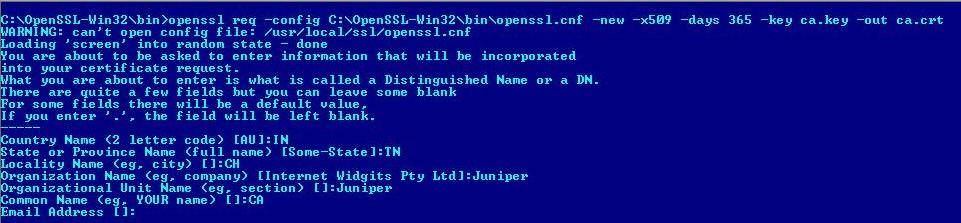
2. Create CA Certificate from the Private Key.
openssl req -config C:\OpenSSL-Win32\bin\openssl.cnf -new -x509 -days 365 -key ca.key -out ca.crt
Enter all the details for the Distinguished Name of the certificate, such as country, organization name, common name, and so on, when prompted.
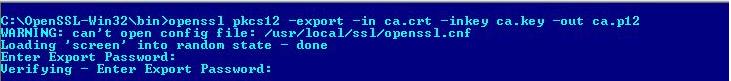
3. Combine ca.crt and ca.key into One File.
openssl pkcs12 -export -in ca.crt -inkey ca.key -out ca.p12
Enter an export password for the p12 file when prompted (the password can be left blank).
Create a Client Certificate using OpenSSL (4 steps)
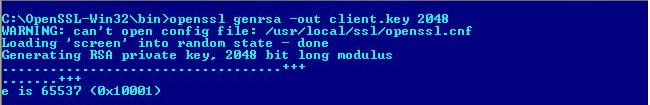
1. Create a Client Private Key.
openssl genrsa -out client.key 2048
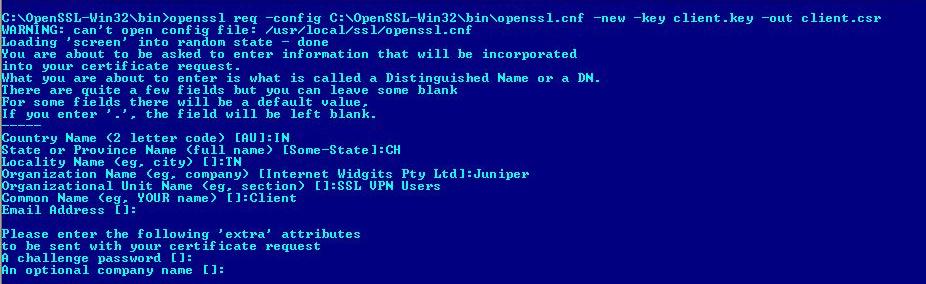
2. Create a Client Certificate Signing Request using Client Key.
openssl req -new -key client.key -out client.csr
Enter all the details for the Distinguished Name of the certificate, such as country, organization name, common name, and so on, when prompted.
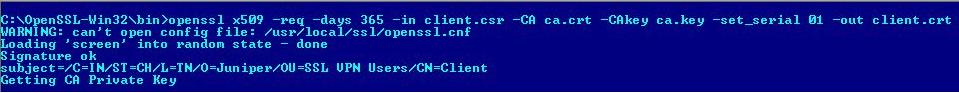
3. Sign the Request with CA to Create the Client Certificate.
openssl x509 -req -days 365 -in client.csr -CA ca.crt -CAkey ca.key -set_serial 01 -out client.crt
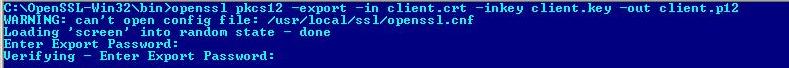
4. Combine Client Certificate and Key File into One File.
openssl pkcs12 -export -in client.crt -inkey client.key -out client.p12
Note:
- Sign each certificate with CA.
- All the certificate and key files are stored under …
/openssl/bin
, unless a path is specified while creating the particular file or is specified in the
openssl.cfg
configuration file.
Configure Machine Authentication (5 steps)
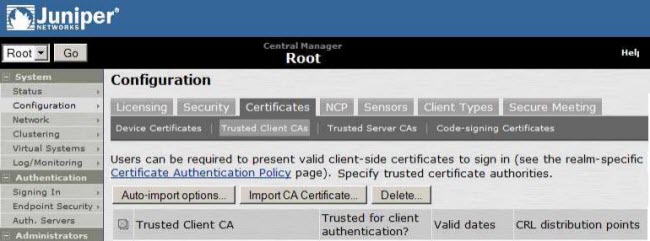
1. Upload the CA (ca.crt) Certificate under Trusted Client CAs.
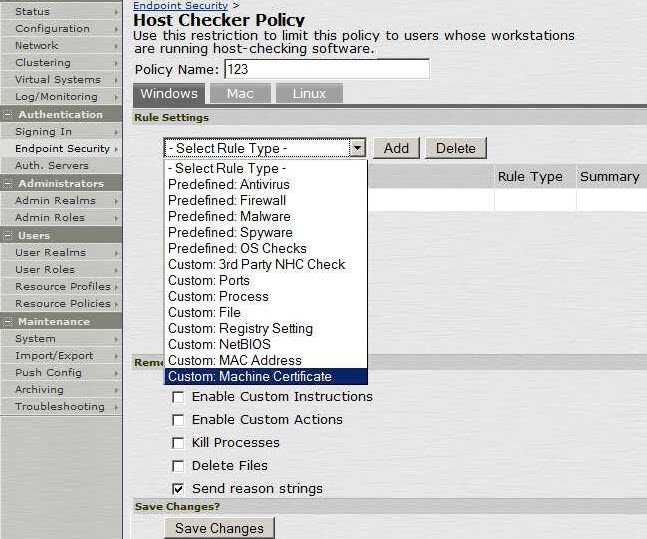
2. Create a New Host Checker Policy and add a New Rule Setting of Type Custom:Machine Certificate.
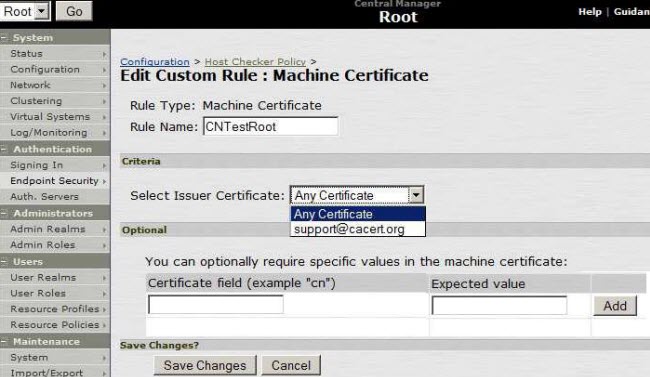
3. Select the Machine Certificate you want to Verify as Part of Host Checking.
4. Create Separate Custom: Machine Certificate Rules for Different Client Computers with Different Certificates Installed on Them.
Configuring Client Certificate on Client Machine
Install the client certificate on the corresponding client machine under Trusted Root Certification Authorities > Personal certificate stores.
1. Go to Start > Run > type mmc and click OK.
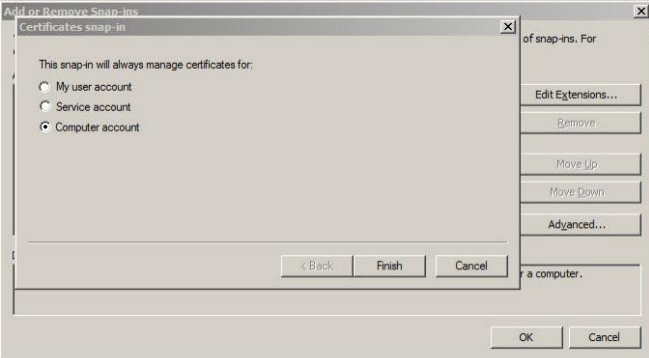
2. On the console go to File > Add/Remove Snap-ins. Select Certificates from the list.
3.Click Add and press Ok.
4.Select Computer account and click Next.
5.On the next window, select Local Computer then click Finish.
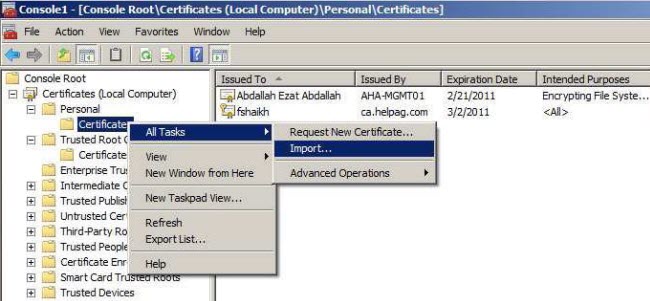
6. Import the client certificate (*.p12) under Certificates (Local Computer) > Personal > Certificates as shown above.