Understanding Switch Security
After physical access has been secured, there is a growing need to ensure that access to the switch ports is secure through any EXEC session connection, such as securing the console (CON) port and securing the Telnet (VTY) ports. In addition, it is important
to ensure that unused switch ports do not become security holes. The following sections describe how to mitigate hardware, environmental, electrical, and maintenance-related security threats to Cisco IOS devices.
Physical and Environmental Threats
Improper and incomplete network device installation is an often-overlooked security threat that, if left uncorrected, can have dire results. Just like a typical PC or server configured with default settings presents a security threat, the same is true for Cisco devices. But software-based security configuration measures alone cannot prevent premeditated or even accidental network damage because of poor installation.
Beyond insecure configuration settings, there are four classes of insecure installations or physical access threats:
- Hardware threats: The threat of physical damage to the switch or switch hardware
- Environmental threats: Threats such as temperature extremes (too hot or too cold) or humidity extremes (too wet or too dry)
- Electrical threats: Threats such as voltage spikes, insufficient supply voltage (brownouts), unconditioned power (noise), and total power loss
- Maintenance threats: Threats such as poor handling of key electronic components (electrostatic discharge), lack of critical spare parts, poor cabling, and poor labeling
Configuring Password Security
The command-line interface (CLI) is used to configure the password and other console commands. Examples 2-4, 2-5, 2-6, and 2-7 show the various passwords to be configured on a switch.
Example 2-4 Switch Password Configuration: Console Password Configuration
SwitchX(config)# line console 0 SwitchX(config-line)# login SwitchX(config-line)# password cisco
Example 2-5 Switch Password Configuration: Virtual Terminal (Telnet) Password Configuration
SwitchX(config)# line vty 0 4 SwitchX(config-line)# login SwitchX(config-line)# password sanj ose
Example 2-6 Switch Password Configuration: Enable Password Configuration
SwitchX(config)# enable password cisco
Example 2-7 Switch Password Configuration: Secret Password Configuration
SwitchX(config)# enable secret sanfran
CAUTION The passwords used in this text are for instructional purposes only. Passwords used in an actual implementation should meet the requirements of a “strong” and “complex” password.
You can secure a switch by using passwords to restrict various levels of access. Using passwords and assigning privilege levels are simple ways of providing both local and remote terminal access control in a network. Passwords can be established on individual lines, such as the console, and to the privileged EXEC (enable) mode. Passwords are case sensitive.
Each Telnet (VTY) port on the switch is known as a virtual type terminal (vty). By default There are five VTY ports on the switch, allowing five concurrent Telnet sessions, noting that other Cisco devices might have more than five logical VTY ports. The five total VTY ports are numbered from 0 through 4 and are referred to all at once as line vty 0 4 (notice the space between 0 and 4). By syntax, this would include the range from 0 to 4, so it includes all five logical VTY ports, 0–4.
Use the line console 0 command, followed by the password and login subcommands, to require login and establish a login password on the console terminal or on a VTY port. By default, login is not enabled on the console or on VTY ports.
Note that you cannot establish a Telnet connection unless you first set all the vty passwords. If there are no vty passwords set, when you try to telnet in, you get a “password required . . . but none set . . .” error message, and your attempt to telnet is rejected.
The line vty 0 4 command, followed by the password and login subcommands, requires login and establishes a login password on incoming Telnet sessions. Again, for Telnet VTY ports to accept a Telnet EXEC session, you must set the vty passwords.
The login local command can be used to enable password checking on a per-user basis using the username and password specified with the username global configuration command. The username command establishes username authentication with encrypted passwords.
The enable password global command restricts access to the privileged EXEC (enable) mode. You can assign an encrypted form of the enable password, called the enable secret password, by entering the enable secret command with the desired password at the global configuration mode prompt. If the enable secret password is configured, it is used (and required) instead of the enable password, not in addition to it.
You can also add a further layer of security, which is particularly useful for passwords that ross the network or are stored on a TFTP server. Cisco provides a feature that allows the use of encrypted passwords. To set password encryption, enter the service passwordencryption command in global configuration mode. Passwords that are displayed or set after you configure the service password-encryption command will be encrypted in the output. This includes the encrypting of the passwords that might otherwise be displayed in plain text on the screen in the terminal output of a show command, such as show run.
To disable a command, enter no before the command. For example, use the no service password-encryption command to disable the service-password encryption command:
SwitchX(config)# service password- encryption SwitchX(config)# no service password- encryption
Configuring the Login Banner
The CLI is used to configure the “message of the day” and other console commands. This banner can be used to warn others that they have accessed a secure device and that they might be monitored.
You can define a customized banner to be displayed before the username and password login prompts by using the banner login command in global configuration mode. To disable the login banner, use the no form of this command.
When the banner login command is entered, follow the command with one or more blank spaces and a delimiting character of any choice. In the example, the delimiting character is a double quotation mark (“). After the banner text has been added, terminate the message with the same delimiting character.
SwitchX# banner login “ Access for authorized users only. Please enter your username and password.
WARNING Use caution when selecting the words that are used in the login banner. Words like welcome can imply that access is not restricted and can allow a hacker to defend his actions
Telnet Versus SSH Access
Telnet is the most common method of accessing a remote network device. However, Telnet is an insecure way of accessing a network device because it passes all command keystrokes, and all output back to the terminal, in unencrypted clear text. Secure Shell (SSH) Protocol is a secure replacement for Telnet that gives the same type of access. Communication between the client and server is encrypted in both SSHv1 and SSHv2. Implement SSHv2 when possible because it uses a more enhanced security encryption algorithm.
First, test the authentication without SSH to make sure that authentication works with the switch. Authentication can be with a local username and password or with an authentication, authorization, and accounting (AAA) server that runs Terminal Access Controller Access Control System Plus (TACACS+) or Remote Authentication Dial-In User Service (RADIUS). (Authentication through the line password is not possible with SSH.) The following example shows local authentication, which lets you use Telnet to get access to the switch with username cisco and password cisco.
!--- The username command create the username and password for the SSH session username cisco password 0 cisco ip domain-name mydomain.com crypto key generate rsa ip ssh version 2 line vty 0 4 login local transport input ssh
To test authentication with SSH, you have to add to the previous configuration statements to enable SSH. Then you can test SSH from the PC and UNIX stations. If you want to prevent non-SSH connections, add the transport input ssh command under the lines to limit the switch to SSH connections only. Straight (non-SSH) Telnets are refused.
line vty 0 4
!--- Prevent non-SSH Telnets. transport input ssh Test to make sure that non-SSH users cannot telnet to the switch. Port Security Configuration
You can use the port security feature to restrict input to an interface by limiting and identifying MAC addresses of the stations allowed to access the port. When you assign secure MAC addresses to a secure port, the port does not forward packets with source addresses outside the group of defined addresses.
NOTE Before port security can be activated, the port mode must be set to access using the switchport mode access command.
With the Cisco Catalyst 2960 series, use the switchport port-security interface command without keywords to enable port security on an interface. Use the switchport port-security interface command with keywords to configure a secure MAC address, a maximum number of secure MAC addresses, or the violation mode. Use the no form of this command to disable port security or to set the parameters to their default state. Example 2-8 shows the commands used to configure port security.
Example 2-8 Configuring Port Security
SwitchX(config)# interface fa0/5 SwitchX(config-if)# switchport mode access SwitchX(config-if)# switchport port- security SwitchX(config-if)# switchport port- security maximum 1 SwitchX(config-if)# switchport port- security mac- address sticky SwitchX(config-if)# switchport port- security violation shutdown
A port must be in access mode (not trunk mode) to enable port security.
You can add secure (specific) MAC addresses to the MAC address table after you set the maximum number of secure MAC addresses allowed on a port in these ways:
- Manually configure all the addresses (switchport port-security mac-address 0008.eeee.eeee)
- Allow the port to dynamically configure all the addresses (switchport port-security mac-address sticky)
- Configure a number of MAC addresses and allow the rest of the addresses to be dynamically configured
You can configure an interface to convert the dynamic MAC addresses to sticky secure MAC addresses and to add them to the running configuration by enabling sticky learning. To enable sticky learning, enter the switchport port-security mac-address sticky interface configuration command. When you enter this command, the interface converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky secure MAC addresses.
The sticky secure MAC addresses do not automatically become part of the configuration file, which is the startup configuration that is used each time the switch restarts. If you save the sticky secure MAC addresses in the configuration file, when the switch restarts, the interface does not need to relearn these addresses. If you do not save the configuration, the MAC addresses are lost. If sticky learning is disabled, the sticky secure MAC addresses are converted to dynamic secure addresses and are removed from the running configuration. A secure port can have from 1 to 132 associated secure addresses. The total number of available secure addresses on the switch is 1024. Security violation situations are as follows:
- The maximum number of secure MAC addresses has been added to the address table, and a station whose MAC address is not in the address table attempts to access the interface.
- An address learned or configured on one secure interface is seen on another secure interface in the same VLAN.
NOTE Port security is disabled by default.
On the Catalyst 2960 series, use the show port-security interface privileged EXEC command, as shown in Example 2-9, to display the port security settings defined for an interface.
Example 2-9 Displaying Port Security Settings
SwitchX# show port- security interface fastethernet 0/5 Port Security : Enabled Port Status : Secure-up Violation Mode : Shutdown Aging Time : 20 mins Aging Type : Absolute SecureStatic Address Aging : Disabled Maximum MAC Addresses : 1 Total MAC Addresses : 1 Configured MAC Addresses : 0 Sticky MAC Addresses : 0 Last Source Address : 0000.0000.0000 Security Violation Count : 0
An address violation occurs when a secured port receives a source address that has been assigned to another secured port or when a port tries to learn an address that exceeds its address table size limit, which is set with the switchport port-security maximum command.
Table 2-8 lists the parameters that can be used with the show port-security command.
Table 2-8 show port-security Command Parameters
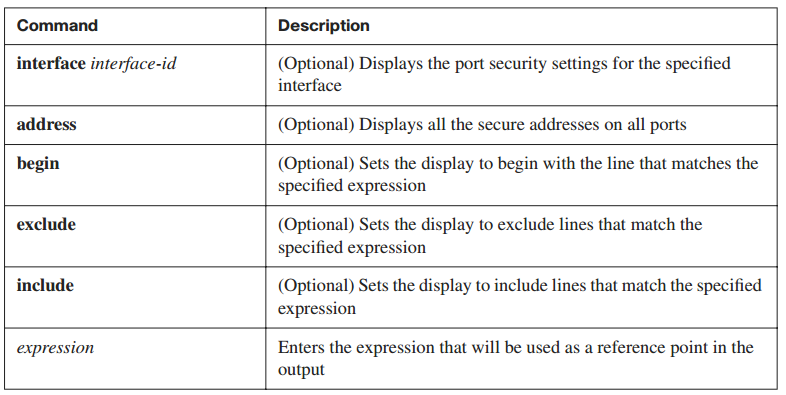
Use the show port-security address command, as shown in Example 2-10, to display the secure MAC addresses for all ports. Use the show port-security command without keywords to display the port security settings for the switch
Example 2-10 show port-security Commands
SwitchX# sh port- security address Secure Mac Address Table ------------------------------------------------------------------- Vlan Mac Address Type Ports Remaining Age (mins) ---- ----------- ---- ----- ------------- 1 0008.dddd.eeee SecureConfigured Fa0/5 - ------------------------------------------------------------------- Total Addresses in System (excluding one mac per port) : 0 SwitchX# sh port- security Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action (Count) (Count) (Count) -------------------------------------------------------------------------- Fa0/5 1 1 0 Shutdown --------------------------------------------------------------------------- Total Addresses in System (excluding one mac per port) : 0 Max Addresses limit in System (excluding one mac per port) : 1024
Securing Unused Ports
In a home, an unlocked door can be a security risk. The same is true of an unused port on a switch. A hacker can plug a switch into an unused port and become part of the network. Therefore, unsecured ports can create a security hole. To prevent the issue, you should secure unused ports by disabling unused interfaces (ports).
To disable an interface, use the shutdown command in interface configuration mode. To restart, or bring up, a disabled interface, use the no form of this command: no shutdown.