Implementing Endpoint Security
Examining Endpoint Security
To devise a successful strategy to defend your endpoints, you must begin with knowledge of the defenses that are available. This section describes the current endpoint protection methods, such as Host-based Intrusion Prevention System (HIPS), integrity checkers, operating system protection, and the Cisco NAC Appliance.
As part of our discussion, we will cover endpoint security and explore the fundamental principles involved in host security. We will also examine specific threats to endpoints, such as buffer overflows, and help you understand how to defend against these, as well as other common threats such as viruses, worms, and Trojan horses.
Defining Endpoint Security
Before you can take steps to defend your endpoints, you must better understand what endpoint security is and what it consists of. We will begin by exploring the fundamental principles involved in host security, as well as discuss the need to defend endpoints from viruses, worms, Trojan horses, and other security threats.
Cisco bases its strategy for securing hosts, as well as the more overarching network and enterprise security needs, on three broad elements (see Table 7-2).

You might be wondering why, if you are securing your network borders, an endpoint security strategy is necessary. Endpoints in your environment run various pieces of software, as well as potentially various operating systems. Having an endpoint security strategy is central to securing your environment, because the software that these systems run has historically had weaknesses that attackers have often exploited.
One approach to this is to use “secure” (trustworthy) software that is specifically designed to protect data and withstand attack attempts. In practice, however, “secure” software has generally been used only with the military and in critical commercial systems. This type of software typically is custom-written and is not commercially available. This being the case, what are you to do when your endpoints are running less secure commercial software to meet your business needs?
One step you can take is to “harden” the software. Hardening is the process of making sure that all known patches and security fixes have been applied to the software, as well as adjusting recommended settings to lock down known vulnerabilities. To successfully do this, you need extensive documentation of the software’s internals, which often is not provided by vendors.
Secure software has two main areas of focus:
- Security of operating systems
- Security of applications that run on top of the operating system
Examining Operating System Vulnerabilities
The various endpoints that we support on our networks each support some form of endpoint, whether it is a desktop operating system (OS) or Network Operating System (NOS). These operating systems provide a set of basic security services to all applications that run on them. Table 7-3 lists the basic security services. 

Even with these basic security services in place, an attacker could still unleash an attack. Should either the trusted code or a trusted path not present or become compromised, the operating system and all applications could easily fall victim to hostile code. Adding to your challenge in defending these endpoints is the fact that an operating system might be made more vulnerable if there is a need to provide support for legacy protocols. Standardizing on a proven, modern operating system may help decrease the need for such legacy support.
One of the benefits offered by modern operating systems is that they provide each process with an identity and privileges. During program operation, privilege switching is possible, or this may occur during a single login session. The UNIX world has the suid (set-UID) facility to provide this capability, whereas modern Microsoft Windows operating systems have the runas utility.
Whether you are working with a UNIX OS or one of the versions of Windows, several techniques can help protect your endpoints from common operating system vulnerabilities. These are examined in Table 7-4. 

By working with both Cisco NAC and Cisco Security Agent, you can effectively provide protection against operating system vulnerabilities.
Examining Application Vulnerabilities
It is important to take the proper steps to address the vulnerabilities faced by your operating system, such as applying service packs and hot fixes and tuning it for secure operation.
However, the majority of attacks target applications or, perhaps more specifically, the data they are protecting (or both). These attacks against applications can be categorized as either direct or indirect:
- Direct: An attacker “tricks” the application into performing a task using the application’s privileges.
- Indirect: An attacker compromises another subsystem and then, through this compromised subsystem, attacks the application (this is called privilege escalation).
Ultimately, attacks like these seek to use the application’s privileges. Hence, the more privileges an application has, the more damage an attacker can do to the application’s sensitive data and the system as a whole with this form of attack. The Cisco Security Agent is designed to help you prevent both direct and indirect attacks. The next section examines the Cisco Security Agent in greater detail as we look at a variety of Cisco technologies that can be used to help defend endpoints from attack.
The goal of most attackers is to gain access to an application running on a host that processes sensitive data. By gaining access to an application running on such a host, the attacker can penetrate the sensitive data he wants to obtain. If the application hosting sensitive data is running in such a manner that an attacker has the option of communicating directly with the application, you must ensure that the application is suitably protected from this potential threat. If an attacker’s goal is to compromise the confidentiality of the sensitive data, attacks will focus on allowing him to gain read or write access to the data via the application. Another form of attack, a denial-of-service (DoS) attack in a specific application, may seek to make the application and its data unavailable to legitimate users.
An example of this might be an attack launched against a database that supports a large e-commerce application.
A common method used in attacks of this nature involves saturating the target (victim) machine with external communication requests. As these communication requests increase, the system is overwhelmed and cannot respond to legitimate traffic, or its responses are so slow that it is rendered effectively unavailable. These DoS attacks may be implemented by two primary means:
- Forcing the targeted computer(s) to reset, or consume its resources so that it can no longer provide the intended service
- Obstructing the communication media between the intended users and the victim machine so that they can no longer communicate Attacks can occur in a variety of ways. An attacker may attack an application directly by exploiting a known flow or vulnerability in the application itself. He might also attack the application by bypassing its access controls and, in doing so, gain read or write access to sensitive data. As commercial business and personal applications grow more complex, the likelihood of flaws and vulnerabilities has grown. For many organizations, the cost and time involved to develop secure custom applications make it a less-than-feasible option.
Another form of attack at the application level is “elevation of privileges.” In this kind of attack, an attacker gains access to sensitive data by using a series of compromises of other system components. An attacker might initially obtain basic user-level access to the system where the sensitive data is stored. Having gained this basic access, the attacker could exploit a given flaw in any local application, using this to attain system administration privileges. Now, with administrative privileges, the attacker may be able to read or write to most objects on the system, including the sensitive data held by the target application.
Understanding the Threat of Buffer Overflows
To understand the threat that buffer overflows present when defending endpoints, you must first understand what a buffer overflow actually is and how applications operate. When a user or other source interacts with an application, it has to carefully verify all input, because the input might contain improperly formatted data, control sequences, or simply too much
data for the application to work with. When these things occur, a buffer overflow condition can arise. Attackers realize this and try to exploit this vulnerability. In fact, buffer overflows are a very common type of exploitation used by attackers.
An attacker who unleashes a buffer overflow exploit essentially tries to overwrite memory on an application stack by supplying too much data to the input buffer. Because this form of attack uses the application’s very nature against itself, it can be hard to stop. Of course, it is not easy to discover how to initiate a buffer flow and use it to exploit a system. However, as soon as an attacker discovers the vulnerabilities that lead to this condition, he or she can prepackage exploit code for widespread use.
Buffer Overflow Defined
With a buffer overflow, a program writes data beyond the allocated end of a buffer in memory. Often buffer overflows arise from a bug in the application or from improper use of languages such as C or C++ that are not memory-safe. When these overflows occur, valid data may be overwritten as well, making these threats particularly dangerous.
Buffer overflows are one of the most commonly exploited computer security risks because of the structure of how computers handle data. Program control data generally sits in the memory areas next to data buffers. An attacker might initiate a buffer overflow condition to make the computer execute arbitrary, potentially malicious code that is then fed back to the
program as data. A very similar attack is a heap overflow. Applications dynamically allocate a stack known as the heap. This is done at runtime, and it generally contains program data. Attackers can target this as well and exploit it in a similar manner.
The Anatomy of a Buffer Overflow Exploit
Because buffer overflows are one of the most common methods of application subversion in use today on the Internet, it is important that you understand these attacks and how to stop them. Let’s take a look at the anatomy of a buffer overflow attack in detail.
In most buffer overflow attacks, the attacker tries to subvert a program function that reads input and calls a subroutine (see Figure 7-1). What makes this possible is that the exploitable program function does not perform input length checks and allocates a fixed amount of memory for data.

- When an application makes a subroutine call, it places all input parameters on the stack.
- To return from the subroutine, the return address is also placed on the stack by the calling function.
- An attacker-supplied parameter can overwrite the return address, being too long to fit on its place on the stack.
The way applications work is that when an application makes a subroutine call, it places all input parameters on the stack. To return from the subroutine, the return address is also placed on the stack by the calling function. An attacker overwrites the return address by sending data that is longer than the fixed memory space on the stack that the application allocated. After this overwrite occurs, the application returns to an attacker-supplied address, pointing to the attacker’s malicious code. In essence, the attacker has hijacked this application communication and now can insert his own malicious code. This code is supplied by the attacker as part of the excessively large input. The end result of this attack is that arbitrary code may now be executed with the privileges of the legitimate application.
Understanding the Types of Buffer Overflows
Most buffer overflow attacks are used to either root a system or cause a DoS attack. We will look at each of these types of attacks. The phrase “rooting a system” comes from the UNIX world. It means that a system has been hacked so that the attacker has root, or superuser, privileges. Rooting a system is most
easily accomplished with either remote root or local root buffer overflows. Of these two, remote root buffer overflows are the more dangerous. This is because an attacker can “own” your system in a matter of seconds if the system is unprotected and vulnerable. If you think in terms of worms, the most dangerous of these have exploited remote root buffer overflows.
Local root buffer overflows work a bit differently. This form of attack generally requires some kind of assistance in distributing the exploit. This is typically done via a virus that is transported by e-mail, or it could be done using a Trojan horse-infected executable. Regardless of the mechanism, the attacker’s goal remains the same.
The great majority of software vulnerabilities that have been discovered are buffer overflows. That is why this is such an important area to understand and defend against. In fact, some research suggests that two out of every three software vulnerabilities found by CERT are buffer overflows. As discussed in a later section, Cisco offers technologies that can defend against buffer overflows, such as the Cisco Security Agent, which can actually prevent buffer overflows.
Additional Forms of Attack
Buffer overflows are not the only concern. The larger issue is that a buffer overflow may be used to initiate malicious code such as viruses, worms, and Trojan horses so that they may gain access to your system and begin to do their damage. Two of the most destructive worms that have been unleashed on the Internet are SQL Slammer and Code Red. The destruction these worms caused was made possible by remote root buffer overflows. In contrast to worms, viruses are more likely to take advantage of local root buffer overflows to unleash their exploits. Trojan horses, the third major threat we will examine in this section, generally resemble viruses in that they exploit local root buffer overflows. Let’s examine each of these in more detail:
- Worms: Worms are a form of malicious code that can replicate themselves without a host over networks by independently exploiting vulnerabilities. In other words, they can replicate themselves without the need to infect a file, as a virus might. Also, because they live in RAM (and because of their capacity for replication), they are incredibly hard to defeat and quite destructive. Although it might seem that the best way to defeat something that lives in memory is to simply reboot the system, effectively clearing out the RAM, this does not address the underlying vulnerability that made the system vulnerable to attack. In a case such as this, the system would be easily reinfected after the reboot if no additional steps are taken to address the vulnerability. Adding to the issue is that worms typically do not require user participation and can spread extremely fast.
- Viruses: In contrast to worms, which can replicate themselves independently, viruses are pieces of malicious code that must have a host to unleash their attack. In some cases, viruses piggyback on legitimate programs or content to deliver their malicious payload. In other instances, such as with the ILOVEYOU virus (which was ILOVEYOU.txt.vbs), the payload was delivered independent of any useful application.
Replication occurs when the virus attaches itself to other software. For instance, in the case of a macro virus, a word.doc may be used. Unlike worms, viruses typically require some form of end-user activation, such as opening a file or clicking an executable. One thing that makes them particularly sneaky is that they can lie dormant for an extended period and then activate at a specific time or date. Viruses also vary in nature. Some are benign, and others are extremely destructive and can destroy programs, files, or entire systems with their exploits. Another aspect that makes them hard to contain is that they can be programmed to mutate to avoid detection and survive attempts to eradicate them.
It is not uncommon for a malicious virus to be packaged with the code of a freeware or shareware program that purports to be something useful, such as a screensaver or game. The host program is something that has a degree of merit, so it is shared among users. It is in this sharing of the executable file that the virus is passed from system to system on CD, via FTP, or as an e-mail attachment. When the file’s recipient executes the program (the infected executable), the virus becomes loaded into memory on that person’s system and can infect other executables on that computer.
Each virus is unique, as are their behaviors. Some install themselves at the first line of code for the executable so that when the user starts the executable, the code for the virus is immediately run. Other viruses are programmed to first check the local hard disk in search of files that have yet to be infected so that they may infect these files. As soon as the code is run, the behavior may be as harmless as displaying a picture or changing the color of text in a given application, or it may be far more destructive.
- Trojan horses: A Trojan horse is different from viruses and worms in that it appears to be a normal and useful program but actually contains hidden, malicious code. When the program is executed, it exploits the privileges of the user who runs it. This can be particularly dangerous if a program such as this is executed by someone with administrative privileges. Often games are used to disguise this malicious code. While the user plays the game, all seems normal, but behind the scenes, the Trojan horse has been installed on the victim’s system. After it is installed, the Trojan horse program continues to run after the game has been closed, unleashing whatever form of attack the programmer intended.
Because the purpose of a Trojan horse is to load a program on a user’s system without his or her knowledge, the nature of the attacks it unleashes can be quite varied. Some Trojan horses may cause immediate damage, and others might be designed to provide remote access to the system via a “back door.” Or the Trojan horse might sit and wait to perform actions as instructed remotely, such as collecting and sending keystrokes captured by a keylogger program running in the background on the machine.
Trojan horses can be hard to defend against. Custom-written Trojan horses, such as those with a specific target, are extremely hard to automatically detect. In addition to taking the proper steps with regard to technology, end-user education is also quite important. A tool such as the Cisco Security Agent is very effective at defeating viruses, worms, and Trojan horses.
Having discussed these three kinds of attacks, let’s take a closer look at worms. Table 7-5 breaks down a worm attack piece by piece.


Table 7-6 compares worm and virus attacks over the past 20 years. It also highlights some of the differences in how the attacks accomplished the various phases of attack that hackers employ. As you review this table, also note how often worms and viruses use similar methods.

Securing Endpoints with Cisco Technologies
With new and emerging threats to endpoint devices, it is important as a security administrator to put in place the right technologies to defend against these threats. Cisco offers a wide range of technologies that can help you protect your endpoints from these threats. This section explores these technologies and discusses how they complement your overall security strategy.
Understanding IronPort
IronPort is designed to protect an enterprise from various Internet threats that target e-mail and web security. IronPort’s e-mail security capabilities are readily used by 20 percent of the largest enterprise organizations in the world. IronPort has a strong history of providing security and reliability. This same code base that protects eight of the ten largest ISPs is built into all of IronPort’s e-mail security appliances for enterprises of any size.
In addition to enterprise-level e-mail protection, the IronPort S-Series is the industry’s fastest web security appliance. This appliance combines a high-performance security platform with Web Reputation technology and a Dynamic Vectoring and Streaming (DVS) engine. The DVS engine is a new scanning technology that enables signature-based spyware filtering. This solution is complemented by a comprehensive set of management and reporting tools that provide ease of administration and complete visibility into threatrelated activities.
IronPort’s M-Series security management appliance is designed to complement IronPort’s e-mail and web security appliances by providing top performance for all your application security gateways. The IronPort M-Series provides a single location where you can effectively manage, store, and monitor all corporate security policy settings and audit information. This flexible management tool was built to centralize and consolidate policy and runtime data, giving administrators a single interface to manage all their application layer security systems.
The Architecture Behind IronPort
SenderBase represents the first and largest e-mail traffic monitoring service, collecting data from more than 100,000 ISPs, universities, and corporations around the world. More than 120 parameters can be measured and scrutinized with SenderBase. The massive SenderBase database handles more than five billion queries per day. Real-time data is provided from every continent, from both small and large network providers. With this massive amount of data, SenderBase can develop the most accurate view of the sending patterns of any given mail sender. This accuracy has helped SenderBase remain the largest database of its kind in the world. SenderBase is licensed to the open-source community, as well as to other institutions that are working to fight spam.
Examining the Cisco NAC Appliance
Several technologies can defend endpoints from the common threats they face. The Cisco NAC Appliance is one device that can be used to enhance and complement other endpoint security measures. Effectively the Cisco NAC comes in two “flavors.” The first is the Cisco NAC framework, which is a software module embedded within NAC-enabled devices. In this framework a number of both Cisco and other NAC-aware vendor products may be used to provide security. The second flavor is the Cisco NAC Appliance. This is an in-band solution that can be used on any switch or router platform to provide a self-contained turnkey solution. This section explores both of these options in greater depth.
The Cisco NAC device enables you to allow only authorized and compliant systems to access the network and allows you to enforce network security policy. This may be done whether the systems are managed or unmanaged. By enabling this enforcement of network security policy, Cisco NAC helps organizations maintain network stability.
The Cisco NAC device provides four key features to help further secure the enterprise and endpoint systems:
- Authentication and authorization
- Posture assessment (evaluating an incoming device against the network’s policies)
- Quarantining of noncompliant systems
- Remediation of noncompliant systems
Table 7-7 covers the two general categories of the Cisco NAC product.

Figure 7-2 shows the components involved when deploying the Cisco NAC Framework. These various components work together to provide compliance-based access control. In this deployment, various NAC functions, such as authentication, authorization, and accounting (AAA), scanning, and remediation, are performed by other Cisco products. As shown in Figure 7-2, the Cisco Secure Access Control Server (ACS) or other partner products such as TrendMicro may be used to provide various functionality.

Figure 7-3 shows the Cisco NAC Appliance, which is a standalone NAC appliance that may be incorporated in both Cisco and non-Cisco networks. This device can provide all the key NAC functionality, including authentication and posture assessment, as well as quarantining and remediation of noncompliant systems without the need for additional products. The Cisco NAC Appliance also comes with preconfigured checks for Windows updates and most major antivirus software packages.

Working with the Cisco Security Agent
In today’s computing environment, endpoint protection must encompass more than simple desktop systems. The Cisco Security Agent software provides full-featured endpoint protection with threat protection capabilities for server, desktop, and point-of-service (POS) computing systems. This highly scalable solution can support as many as 100,000 agents from a single management console. Figure 7-4 shows the architecture of the Cisco Security Agent, which can grow with an organization’s changing needs.

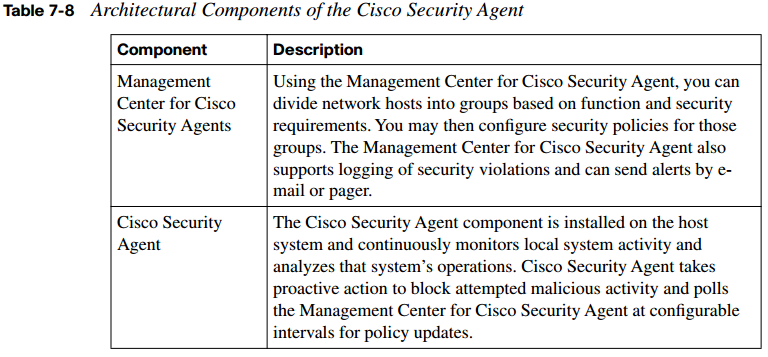
Table 7-8 explores the underlying architectural model for the Cisco Security Agent and the two components that make it up.
Secure administration is another key aspect of this solution. An administration workstation may be configured to securely connect to the Management Center for Cisco Security Agent by using a Secure Socket Layer (SSL)-enabled web interface. This allows for flexibility in administration while providing security.
Understanding Cisco Security Agent Interceptors
To help you understand how Cisco Security Agent interceptors work, we must first explore how applications access system resources. Each time an application needs access to system resources, it has to make an operating system call to the kernel. When this occurs, the Cisco Security Agent intercepts these operating system calls and compares them to the cached security policy. Figure 7-5 shows this process.

As long as the request does not violate the policy, it is passed to the kernel for execution. However, should the request violate the security policy, the Cisco Security Agent blocks the request and takes one of the following actions:
- An appropriate error message is passed back to the application.
- An alert is generated and sent to the Management Center for Cisco Security Agent.
To detect malicious activity, the Cisco Security Agent correlates the particular operating system call with the other calls made by that application or process. By correlating these events, it can see irregularities that denote malicious activity. This “behavior-based” manner of detection adds flexibility and removes the need to rely on signatures and signature updates.
Endpoint protection is provided by the Cisco Security Agent through the deployment of four interceptors, as described in Table 7-9.

The Cisco Security Agent, by intercepting communication between applications and the underlying system, combines the functionality of a number of traditional security approaches:
- Distributed firewall: Through the network interceptor, the CSA performs the functions of a host firewall.
- HIPS: The network interceptor and the execution space interceptor combine to provide the alerting capability of a HIPS with the proactive enforcement of a security policy.
- Application sandbox: The file system, configuration, and execution space interceptors act together to provide an application sandbox. Here you can run suspect programs with less than normal access to system resources for security purposes.
- Network worm prevention: Worm protection is provided by the network and execution space interceptors without a need for updates.
- File integrity monitor: The file system and the configuration interceptors work together to act as a file integrity monitor.
The Cisco Security agent is designed with a series of preconfigured policies that implement all these levels of protection without additional configuration. With the Cisco Security Agent, organizations have the flexibility to create or change policies if they like, to tailor them to their specific needs.
Examining Attack Response with the Cisco Security Agent
It seems that each year a number of new software programs and technologies are released. Coming quickly on their heels are malicious attacks that attempt to discover and exploit their vulnerabilities. Although literally thousands of varieties of attacks exist, with new ones constantly being devised, in general almost all of them have the same ultimate goal.
With each, the goal is to gain control of the core mechanisms of the system being targeted.
However, significant differences exist between the attack mechanisms used in the different phases of an attack. For instance, the mechanisms used in the probe and penetrate phases are much different from the attack mechanisms used in the persist phase.
With the proliferation of new software and new technologies, attackers are constantly uncovering new vulnerabilities and creating custom exploits to take advantage of them. It is because of this ever-changing nature that the first two phases of an attack are constantly evolving. Effectively combating attacks at the probe and penetrate phases requires an administrator to stay current with malicious IPS signatures and firewall defenses.
Unicode encoding of web strings or overlapping packet fragments are just a couple of the ways that attacks during these early phases may evade detection. A significant amount of interpretation is needed because of the mutability of attacks at the penetrate stage. The false alarms that can be generated at this stage require time-consuming review by a security
administrator.
The attack mechanisms generally used in the persist phase and the later phases are much more stable than those employed early on. At these later phases, the malicious activities of an attacker are more limited. Typically, an attack involves making a system call to the kernel to access the system resources. When this occurs, the malicious code may attempt to modify the operating system, modify files, create or alter network connections, or violate the memory space of active processes. These potential attacks on systems resources are much more stable in nature than what we see in earlier phases. Such attacks also use different vectors to access the target systems when compared to attacks launched in earlier phases. In general, local exploits are much more stable and predictable than remote exploits, which are platform-specific because of their use of assembly code.
Because identifying attacks in their early phases is nearly impossible, Cisco Security Agent instead focuses on providing proactive security through controlling access to system resources. Unlike security measures that require almost constant updating of defenses to keep up with the latest attacks, the Cisco Security Agent provides protection that is much more easily managed. The Nimda and Slammer worms caused millions of dollars of damage to enterprises on the first day of their release on the Internet, before updates were readily available. However, the Cisco Security Agent stopped these attacks because it identified their malicious behavior without the need for any updates.
Best Practices for Securing Endpoints
As mentioned earlier, trusted operating systems exist, but they are expensive and can be cumbersome to support. For the most part these are used for military or government purposes, acting as critical servers or workstations. For most modern operating systems, regardless of vendor, the default configuration is still quite untrustworthy. Significant improvements have occurred in the last ten years, but the sophistication of attacks has also greatly improved. As an administrator, you should consider operating system hardening as a mandatory step you must take in sensitive environments. A hardened system can resist an attacker’s attempts at exploitation when alternative paths to sensitive data are attempted.
One way to stay current with vulnerabilities that might plague your systems is to visit your vendor’s website often. Another way to stay up to date on critical issues is to become familiar with industry organizations that track and categorize vulnerabilities. The SANS Institute is one such organization. Each year it compiles its Top 20 list of vulnerabilities. It breaks them into a variety of areas, such as client-side vulnerabilities, server-side vulnerabilities, application abuse, and the like. It is important to familiarize yourself with these vulnerabilities and to stay current as new vulnerabilities emerge. You may view the SANS Institute’s Top 20 list for 2007 at http://www.sans.org/top20.
In addition to performing proper operating system hardening, you should employ network access controls (firewalls) to limit the exposure of hosts to external threats. Only necessary traffic should be allowed to reach internal devices and sensitive machines. A number of security add-ons also should be considered. Tools such as integrity checkers, IPSs, and host firewalls should be put in place for systems that perform important services to help prevent attacks. Additionally, third-party preprocessors may be installed on the host to filter HTTP requests that are received at the web service. Deep packet inspection may also be enabled
on routers and ASAs to filter certain request types and protocol-specific parameters before these requests reach the server.
Application Guidelines
When it comes to application design, security should not be an afterthought. It is best to approach application design with a focus on two key ideas. First, be sure to apply the leastprivilege principle, limiting access where possible. Second, applications should employ modularization and multiple tiers of application functionality, spread over multiple servers.
By following these two steps in your design, you can create a much more secure application.
Even the best single security mechanism cannot stop all threats. That is why it is important to use multiple defenses together to form a multilayered security system to manage host and application risks. Any single security mechanism might be compromised; that is why a multilayered security system does not rely on just one thing. Rather, a multilayered approach employs a number of different security mechanisms to provide a similar protection function while acting as layers so that if one mechanism becomes compromised, another can halt the attack. Although we are discussing this in terms of host and application defense, this principle applies universally to any security system, making it a best practice in any security design.
Apply Application Protection Methods
To conclude our discussion of best practices, it is important that we review four key application protection methods that can help make your environment more secure:
- Using application access controls to enforce least privilege and using secure programming practices are the most significant steps you can take toward application security. The creation of safer, high-level languages, along with the growing awareness of the need for application security among developers, has led to increased security in many current systems. However, most off-the-shelf software used by consumers and businesses is still quite vulnerable to simple attacks that can defeat its security.
- Cryptography is another area of application protection that, when used properly, can provide confidentiality, integrity, and authenticity guarantees for data. These cryptographic methods often are used to protect data when it is no longer under the control of the application. For instance, cryptography might be used to encrypt data on a hard drive so that it can be read only by the application. Another common application of cryptography is to use it to encrypt all data as it flows over the network between the client and the server. This can provide confidentiality in an unsafe network or when communicating using a virtual private network across the Internet.
- Never trust data from outside sources. This code could be malicious and could harm your application. It is also important to perform rigid input validation to be sure that all information entered into that application meets your expectations. Malformed input from a malicious source could damage your system or crash the application.
- Unfortunately, you have to assume that some of the users who work with a given application may be malicious. Users may grow disgruntled and use their access to your corporate network to carry out various malicious acts using your own applications and network access. You need to defend against this, as well as against users who might inadvertently do harm. They can do this by introducing threats into your network and applications either through misuse or through lack of knowledge when faced with such things as infected attachments and malicious programs posing as benign freeware.