Examining Cisco’s Model of the Self-Defending Network
Several trends in network security point out the need for a flexible, resilient, and fast acting defensive strategy. Both evolving threats and the blurring of the network perimeter serve to underline this need. In Cisco’s model of the Self-Defending Network, every network device has a part to play in a cooperative, homogeneous network security strategy. It is still useful to know the answers to questions such as these:
- Where the threats are coming from (both internal and external to an organization)?
- Across what parts of the network are these threats traveling?
- In which direction are these threats flowing?
Although these questions are open-ended and can only be answered in the course of an organization’s risk assessment, one central question needs to be answered, and that is, “where is the network perimeter?” This will be examined (if not totally answered!) in the next subsection.
Where Is the Network Perimeter?
Before examining which devices to deploy in a secure network architecture, it would be useful to determine where the trusted network boundaries or perimeters are. Here is a simple definition of a network perimeter:
Network perimeters are established by firewalls. A network perimeter is a logical boundary between parts of the network with differing levels of trust.
For now, per the (unfair?) stereotype of a politician, we will evade directly answering the question of where the perimeter is. Instead, the next few thoughts and examples aid you in determining where your network perimeters are in your network.
Once you have established a definition of a perimeter that works for your network, stick with it, as your network security philosophy will be built around it. Some network security experts have opined that the network perimeter is extinct. Most would disagree, at least in part, while agreeing that determining where the perimeter is has become somewhat blurred. For example, firewalls have traditionally established the perimeter by establishing security zones of various levels of trust and using technical controls such as ACLs to control traffic across it. This also made it fairly simple to define ingress and egress flows of traffic because ingress (or inbound) would be defined as traffic that flows from a less-trusted to a more-trusted security zone. Egress (or outbound) traffic would be the opposite direction. Although the definition of ingress versus egress has not changed, what has changed is the location of the perimeter itself in some cases. Here are two examples of cases where the location of the perimeter is somewhat blurred:
- Example 1: Perimeter on an application server. If TCP port 80 (HTTP) traffic is allowed in through a firewall, and that firewall is only
analyzing traffic to OSI layer 4 (the transport layer), it can be argued that the firewall is no longer creating perimeter security for that protocol. The perimeter might actually be established on the web server itself, using whatever application layer firewall capabilities that may or may not be deployed on that device. The security of the entire network may hinge on the razor edge of patch management and proper configuration of the web server. Clearly, an application layer firewall will be needed in order to inspect the traffic for protocol compliance, as well as for malicious intent such as Instant Messaging (IM), Peer-to-Peer (P2P), file sharing, embedded code, and so on. A good security policy defines protocols that are absolutely not allowed on a network, but how is this policy enforced? - Example 2: Moving Perimeter. At one of your training facilities, one of the employee-students brings in a wireless access point and connects it to a wired Ethernet jack in the classroom, creating a wireless network without encryption in the classroom. On the face of this, it seems OK—if the individual connects to the data jack, they are inside the perimeter, and this is allowed by your security policy; then you realize that one of your competitors, who has offices in the floor above you, has access to your corporate network. Where is your perimeter now? Has it moved? Are internal systems at risk?
NOTE
Security practitioners are often heard saying things like, “After we establish the perime ter…” or “That attack is trying to breach our perimeter…” or such. The word “perimeter” will always remain a source of disagreement and anxiety unless the network security poli cy defines it in a consistent way. Cisco used to offer a simple definition (simple is good, right?) that went something like this, “A firewall is a device that establishes a trusted net work boundary (perimeter) and then manages traffic across that boundary.” We examine firewalls in detail in Chapter 5.
Building a Cisco Self-Defending Network
The Cisco Self-Defending Network recognizes that all network elements— whether switch, router, security appliance, firewall, or application server—have a role to play in creating a secure networking environment.
The Three Key Principles of the Cisco Self-Defending Network
The Cisco Self-Defending Network is a unified approach to identify, prevent, and adapt to threats. There are three key principles in Cisco’s Self-Defending Network. A network should be the following:
- Integrated. Every network element is part of both defense and policy enforcement.
- Collaborative. Devices and services collaborate to prevent attacks.
- Adaptive. Threats are automatically prevented through proactive security technologies.
Four Collaborative Systems
Cisco specifies four systems that leverage on the three just-defined principles of the Cisco Self-Defending Network ( integration, collaboration, and adaptation) to prevent attacks. The word “system” in this context defines a logical grouping or type of Cisco network device or software. The following are these four systems:
- Policy Management. Cisco Security Management.
- Threat Management. Cisco Security MARS.
- Endpoint Security. Cisco NAC Appliance and Cisco Security Agent.
- Network Infrastructure. Cisco IPS Sensor Software, Cisco IOS Software, and Cisco ASA Adaptive Security Appliances.
There are more details on some of these Cisco Self-Defending Network solutions in the following section.
EXAM ALERT
Be able to list these systems and match them to the appropriate Cisco solution. Remember that Cisco’s use of the word “system” here defines a logical grouping or type of Cisco network device or software.
Components of the Cisco Self-Defending Network
The components of a Cisco Self-Defending Network are three technical controls and one administrative control. This ties in with the terms physical, administrative, and technical controls found in Chapter 1. Here are the terms:
- Secure Network Platform. Use devices where security is an integral, fundamental network feature. This is a technical control.
- Threat Control and Containment. Employ advanced technologies that mitigate the effects of outbreaks and ensure employee productivity in a constantly-evolving threat environment. This is a technical control.
- Secure Communications. Configure devices to ensure the confidentiality and integrity of data, voice, and wireless communication. This is a technical control.
- Operational Control and Policy Management. Deploy a suite of controls that creates a framework for operational control and policy management to ensure end-to-end security. This is an administrative control.
A secure network platform will be the subject of discussion in subsequent chapters including Chapter 3, “Security at the Network Perimeter.” Let’s examine the last three of the four elements in Cisco’s Self-Defending Network separately: threat control and containment, secure communications, and operational control and policy management.
Threat Control and Containment
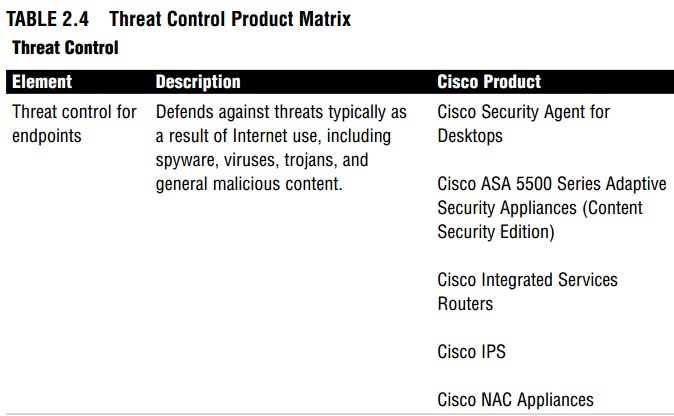
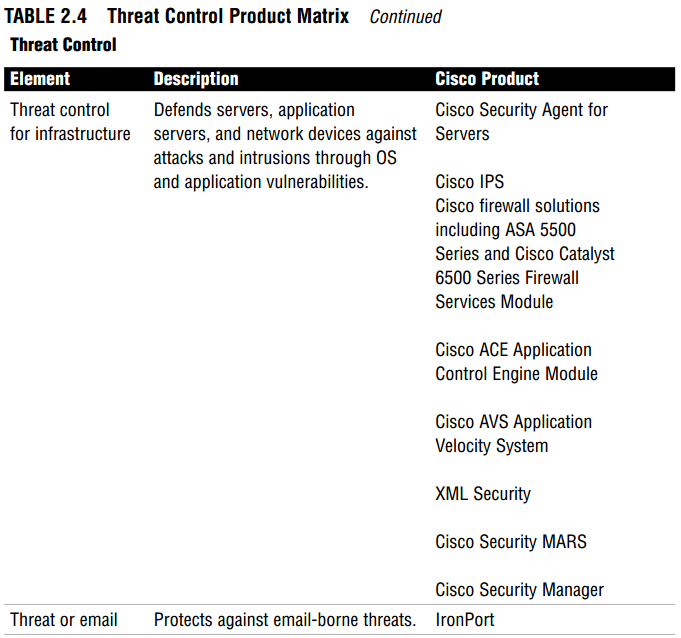
The Cisco solution for threat control and containment contains three elements: threat control for endpoints, infrastructure, and email. Table 2.4 summarizes these threat control and containment elements and lists the Cisco products used.
Secure Communications
Secure communications leverages on advanced technologies such as VPN services (both IPsec and SSL), as well as secure voice and wireless, to maintain confidentiality while increasing flexibility and in a cost-effective manner.
NOTE
Cisco really emphasizes secure communications in not only the traditional “triple play” of data, voice, and video, but also in wireless. This is also a constant thread in this Exam Cram. Cisco’s secure communications solutions use encryption to ensure confidentiality.
For example, Cisco’s IPsec VPN portfolio can be relied on to provide secure communications for both remote access and site-to-site connections. This would be very useful, for example, if an organization wanted to protect the communication path between a sales executive sipping coffee at a local designer coffee shop and the head office, while simultaneously wirelessly connected to the Internet.
Operational Control and Policy Management
Employs network management solutions that aid in the speed and accuracy of policy deployment and provides visibility throughout the network to monitor end-to-end. The controls also help in enforcement of the security policy and manage workflows. Let’s briefly look at two products in the Cisco Self-Defending Network product portfolio: Cisco Security Manager and Cisco Security MARS.
Cisco Security Manager
Cisco Security Manager is a solution that provides for the central provisioning of all aspects of device configuration for the Cisco family of security products. It scales from networks with fewer than 10 devices to truly enormous networks with thousands of devices. Here are some of Cisco Security Manager’s benefits:
- Provisions IOS router platforms, which use the Cisco IOS Security image, as well as ASA 5500 Series Adaptive Security Appliances, Cisco PIX 500 series Security Appliances, Cisco 4200 Series Sensors, and the Advanced and Prevention Security Services Module (AIP-SSM) on the Catalyst 6500 Series and ASA 5500 Series Security Appliances.
- Centrally managed policies with multiple views, including the ability to graphically represent the entire network.
- Graphical user interface.
- Integrates with Cisco Security MARS (see the next section) for event correlation with firewall rules.
- Integrates with Cisco Secure Access Control Server (ACS) to create detailed role-based access control (RBAC) to multiple devices and management functions.
- Integrates into change management and change control by assigning tasks for deploying policies.
Cisco Security MARS
The Cisco Security Monitoring and Reporting System monitors network security devices made not only by Cisco, but also by other companies. It has the following benefits:
- False positives are reduced by an end-to-end network view.
- Its understanding of the network topology and configuration promotes effective attack mitigation.
- NetFlow network behavior analysis helps detect environmental anomalies.
- MARS has over 150 built-in (but customizable) reports, which aid in audit compliance.
- Visual tools, such as detailed topological graphs, aid in identifying threat sources, and making specific recommendations for threat remediation
through layer 2 to 7 of the OSI model.
Cisco Integrated Security Portfolio
Cisco offers a portfolio of products, both hardware and software, to implement the Self-Defending Network. Its modular nature enables you to progressively layer on security features to an existing core IP network. Figure 2.7 illustrates the following:
- An organization starts with an existing core IP network (depicted as a star).
- The core IP network can be enhanced with Cisco’s portfolio of Security Point Services (depicted as a circle wrapping the core IP network’s star).
- The network can further evolve as Advanced Technologies and Services are integrated into the solution.
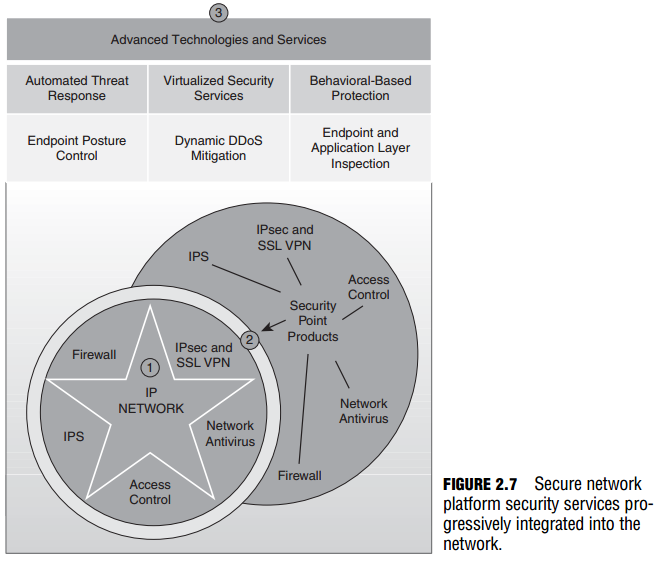
Because no one product can offer all the security services required to secure network infrastructure, Cisco has a broad portfolio of integrated security products. Here is a sampling of some of those products:
- Cisco IOS platforms with integrated IPS, VPN, and stateful firewall technologies.
- Cisco ASA 5500 Series Adaptive Security Appliances with integrated VPN services to enforce perimeter security and access control and IPS (with the AIP-SSM card).
- Cisco PIX 500 Series Security Appliances with integrated VPN services to enforce perimeter security and access control.
- IDS and IPS appliances (blade servers) and integrated IDS and IPS for Cisco IOS routers, Cisco PIX Security Appliances, and Cisco ASA Adaptive Security Appliances.
- Cisco Security Agent endpoint protection software, which protects servers and workstations from known and also unknown threats.
- Security modules (VPN, firewall services) for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers.
- Security Management products for single devices (Cisco Router and Security Device Manager, Cisco Adaptive Security Device Manager) and multiple devices (Cisco Security Manager, Cisco Security MARS).
NOTE
Arguably, the Cisco Integrated Services Routers (ISRs) with a security IOS is the single device that integrates the majority of these features. It integrates secure voice, data, and video services. Some ISRs also offer secure wireless connectivity, either as an integrated feature or with add-on modules. If you have picked up this Exam Cram, you probably already possess the necessary skills, as stated in the course goals for ICND2, “to install, operate, and troubleshoot a medium-sized network, including connecting to a WAN and implementing network security.”
ICND2 is the second of the two courses that comprise the CCNA material. The CCNA cur riculum is based on IOS routers; therefore, it’s no mystery that the IOS router is used to demonstrate these technologies in subsequent chapters.