Cisco Network Mgmt Protocol FAQ: Common Management Protocols
Q1. Why is SNMPv1 not considered secure? How could a hacker exploit its security holes?
Q2. One of the advantages of SNMPv1 lies in the simplicity of its agent implementations. Does this simplicity also have drawbacks?
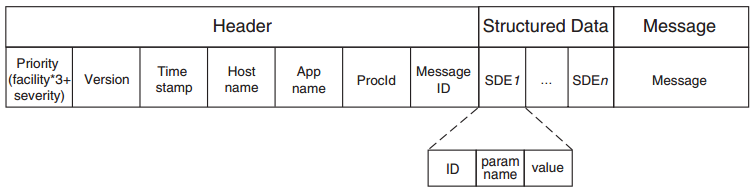
Q3. Explain the difference between an SNMP trap and a syslog message.
Q4. What is the most important reason CLI is hard to use for management applications?
Q5. In what way do CLI and syslog complement each other?
Q6. SNMP has a specific concept of MIBs. Where is the MIB in Netconf?
Q7. One criticism in conjunction with SNMP concerns reliability because SNMP in general uses UDP as a transport, in which packets (and, hence, SNMP management requests or responses) can be dropped. Describe an obvious way of handling reliability in Netconf.
Q8. File transfer protocols allow the transfer of files between two locations. Netconf operations have some resemblance to file transfer protocols, in that they allow the copying, transfer, and deletion of config files. Name three ways in which Netconf differs from a simple file transfer protocol for configuration files.
3) Subtree filtering, allowing to process only subconfigurations within a configuration file.
Q9. What is a flow in Netflow?
Q10. We stated that Netflow can help you identify the top talkers in your network. How? (You may assume that each talker connects to your network using a static IP address—that is, an IP address that does not change.)
More Resources