CCNP Security FAQ: TrustSec and MACSec
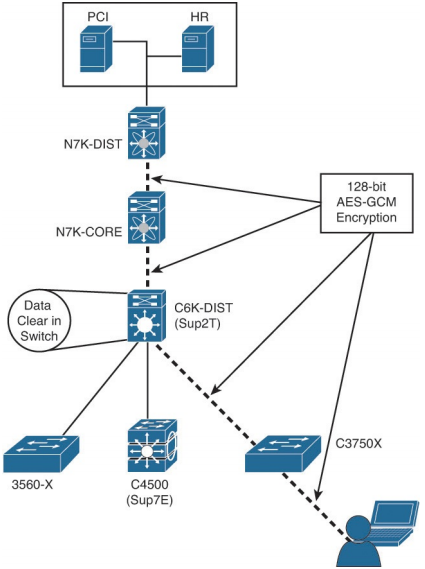
Figure: MACSec Layer-2 hop-by-hop encryption.
Q1. What is a security group tag?
a. A luggage tag applied by TSA workers at airports to flag bags as they enter security checkpoints
b. An internal assignment used in ISE to represent a local copy of an Active Directory group
c. A 16-bit value that represents the context of a user and/or a device
d. An RFID tag used to identify a wireless asset to ISE
Q2. Where are security groups defined in the ISE administrative GUI?
a. Administration > System > Security Group Access > Security Group
b. Policy > Policy Elements > Results > Security Group Access
c. Policy > Policy Elements > Dictionaries > System > Security Group Access
d. Policy > Firewall > Identity by TrustSec
Q3. What are three ways that an SGT can be assigned to network traffic?
a. Manual binding of the IP address to an SGT
b. Manually configured on the switch port
c. Dynamically assigned by the network access device
d. Dynamically assigned by the 802.1X authorization result
e. Manually configured in the NAC agent profile
f. Dynamically assigned by the AnyConnect network access manager
Q4. True or False? An SGT-capable device can automatically map traffic to an SGT based on the VLAN of that traffic.
a. True
b. False
Q5. Which peering protocol can be used to transmit a mapping of IP address to SGTs between SGTcapable devices when traffic is crossing non–SGT-capable network segments?
a. Enhanced Interior Gateway Routing Protocol (EIGRP)
b. Intermediate System—Intermediate System (IS-IS)
c. Border Gateway Protocol (BGP)
d. Security Group Exchange Protocol (SXP)
Q6. What are two modes of SXP peers?
a. Speaker
b. SGT-Reflector
c. Listener
d. SGT-Sender
Q7. How is the SGT transmitted when using native tagging?
a. The SGT is included in the Cisco Metadata (CMD) portion of the Layer-2 Frame.
b. The SGT is included in 802.1Q trunking.
c. The SGT is included in Inter-Switch-Link (ISL) trunking.
d. The SGT is carried in Cisco Discovery Protocol (CDP) messages.
Q8. When using native tagging of SGTs, how can an administrator ensure confidentiality and integrity of the tag?
a. By enabling MD5 authentication between SGT peers
b. By enabling IEEE 802.1AE (MACSec) between the switches
c. By enabling IEEE 802.1AE (MACSec) between the endpoint and the access switch
d. By configuring peer-to-peer GRE tunnels between the switches
Q9. What are two methods of enforcement with SGTs?
a. SG-ACLs on switches.
b. SG-ACLs on routers.
c. SG-Firewalls.
d. SG-Appliances.
e. SGTs are not enforced.
Q10. What is the difference between uplink MACSec and downlink MACSec?
a. Uplink MACSec defines the encrypted traffic entering the switch from the endpoint, whereas downlink MACSec is the encrypted traffic leaving the switch, destined to the endpoint itself.
b. There is no difference between uplink and downlink MACSec.
c. The difference is solely based on the encryption algorithm used.
d. Uplink MACSec defines the encrypted connection between network infrastructure components, whereas downlink MACSec defines the encrypted connection between the access layer device and the endpoint.