CCNP Secure FAQ: Deploying Scalable Authentication in Site-to-Site IPsec VPNs
Q1. What is the one central trusted introducer called?
a. Identity certificate
b. RSA algorithm
c. Certificate authority
d. X.500 distinguished name
e. None of these answers are correct.
Q2. A list of all certificates that are no longer valid is called which of the following?
a. Old certificate list
b. Revoked Certificate List
c. Certificate Revocation List (CRL)
d. Invalid Certificate Authority List
e. Expired Certificate List
Q3. Which of the following is something that can cause issues in a PKI system?
a. Synchronized time
b. Variable time
c. Unsynchronized time
d. Manually configured time
e. None of these answers are correct.
Q4. The SCEP interface on a Cisco IOS Software Certificate Server is enabled with what command?
a. ip scep server
b. set scep server enable
c. ip http server
d. crypto server scep
e. None of these answers are correct.
Q5. To integrate PKI-based authentication with site-to-site VPNs, which protocol must be configured to use PKI-based authentication?
a. IKE
b. GRE
c. AAA
d. RSA
e. VPN
Q6. PKI clients can enroll to the Cisco IOS Software Certificate Server using which two types of enrollment?
a. SCEP
b. IKE
c. TACACS
d. Manual
Q7. Which storage method is considered the most secure for storing a Cisco IOS Software PKI client’s private key?
a. USB Smart Token
b. NVRAM in clear text
c. Encrypted on an external USB storage
d. Encrypted on NVRAM
e. Private section in NVRAM
Q8. What information does the client send to the CA during the enrollment process?
a. IP address
b. Client’s private key
c. Client’s public key
d. Name of device
Q9. By default, what will the IKE process on Cisco IOS Software routers accept if signed by its locally defined trustpoint CA?
a. A client IP address
b. Client’s private key
c. Any valid certificate
d. A new CRL
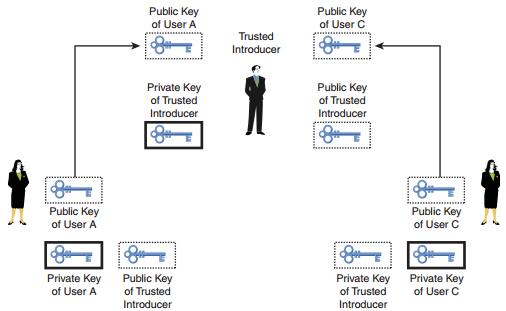
Q10. _____ is where existing point-to-point key exchanges can be tied together to soften the public key distribution problem.
Q11. When enrolling to a PKI, clients submit their _____ and _____ to the CA.
Q12. When deploying PKI-enabled VPNs, one of the major choices is whether to use a _____ PKI or an _____ PKI.
Q13. _____ provides data integrity, data origin authentication, protection against replay, and confidentiality to user traffic.
Q14. Digital signatures are commonly used by many authentication protocols for traffic running over _____ networks.
Q15. To participate in the PKI system, all end users must _____ with the CA, which involves a process in which they submit their public key and their name to the CA.
Q16. An _____ is a piece of information that binds a PKI member’s name to its public key and puts it into a standard format.
Q17. The Cisco IOS Software Certificate Server stores its database on the local _____ of the router.
More Resources