Starting a Cisco Router
A Cisco router goes through its startup when it is first turned on and there is no configuration saved. When the startup is completed, you can enter the initial software configuration. Recognizing correct router startup is the first step in installing a Cisco router. The router must start successfully and have a valid configuration to operate on the network. This lesson describes how the router starts up and explains how to verify its initial operation.
Initial Startup of a Cisco Router
The startup of a Cisco router requires verifying the physical installation, powering up the router, and viewing the Cisco IOS Software output on the console. To start router operations, the router completes the following tasks:
- Runs the power-on self test (POST) to test the hardware
- Finds and loads the Cisco IOS Software that the router uses for its operating system
- Finds and applies the configuration statements about router-specific attributes, protocol functions, and interface addresses
When a Cisco router powers up, it performs a POST. During the POST, the router executes diagnostics to verify the basic operation of the CPU, memory, and interface circuitry.
After verifying the hardware functions, the router proceeds with software initialization, during which it finds and loads the Cisco IOS image, and then finds and loads the configuration file, if one exists.
The following lists the steps required for the initial startup of a Cisco router:
Step 1 Before starting the router, verify the following:
- All network cable connections are secure.
- Your terminal is connected to the console port.
- Your console terminal application, such as HyperTerminal, is selected.
Step 2 Push the power switch to “On” or plug in the device if there is no On/Off switch.
Step 3 Observe the boot sequence and the Cisco IOS Software output on the console.
Initial Setup of a Cisco Router
When the router starts up, it looks for a device configuration file. If it does not find one, the router executes a question-driven initial configuration routine, called “setup.” Setup is a prompt-driven program that allows a minimal device configuration. After a router completes the POST and loads a Cisco IOS image, it looks for a device configuration file in its NVRAM. The NVRAM of the router is a type of memory that retains its contents even when power is turned off. If the router has a startup configuration file in NVRAM, the usermode prompt appears after entering the console password, if one has been set.
When starting a new Cisco router, there is no configuration file. If no valid configuration file exists in NVRAM, the operating system executes a question-driven initial configuration routine, referred to as the system configuration dialog, or setup mode.
Setup mode is not intended for entering complex protocol features in the router. Use setup mode to bring up a minimal configuration. Rather than using the setup mode, you can use other various configuration modes to configure the router.
The primary purpose of the setup mode is to rapidly bring up a minimal-feature configuration for any router that cannot find its configuration from some other source. Setup mode can be entered when the router boots up without a configuration, or it can be entered at any time after the router is booted and operational, by entering the setup privileged EXEC mode command. Example 4-1 shows how to enter setup from the privileged EXEC mode prompt.
Example 4-1 Entering Setup
Router# setup --- System Configuration Dialog --- Continue with configuration dialog? [yes/no]: yes At any point you may enter a question mark '?' for help. Use ctrl-c to abort configuration dialog at any prompt. Default settings are in square brackets '[]'. Basic management setup configures only enough connectivity for management of the system, extended setup will ask you to configure each interface on the system Would you like to enter basic management setup? [yes/no]: no
For many of the prompts in the dialog of the setup command facility, default answers appear in square brackets ([ ]) following the question. Pressing Enter allows the use of the defaults.
When prompted with “Would you like to enter basic management setup?” the system configuration dialog can be discontinued by entering no at the prompt. To begin the initial configuration process, enter yes. Normally, you enter no at the “basic management setup” prompt so that extended setup can be entered to configure more specific system parameters. Pressing Ctrl-C will terminate the process and start over at any time. When using the command form of setup (Router# setup), Ctrl-C returns to the privileged EXEC prompt (Router#).
If you enter yes at the “Would you like to enter basic management setup?” prompt, you are prompted with “First, would you like to see the current interface summary?” Enter yes to view the router interfaces. Example 4-2 shows the output indicating the current status of each router interface. This information includes the interface IP address and current configuration.
Example 4-2 Current Status of Interfaces
Any interface listed with OK? value “NO” does not have a valid configuration Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned NO unset up up FastEthernet0/1 unassigned NO unset up up Serial0/0/0 unassigned NO unset up up Serial0/0/1 unassigned NO unset down
Continuing through the setup dialog, you are prompted for global parameters. Enter the global parameters at the prompts, using the configuration values that were determined for the router.
The first global parameter sets the router host name. This host name will precede Cisco IOS prompts for all configuration modes. The default router name is shown between the square brackets as [Router].
Use the next global parameters shown to set the various passwords used on the router.
Example 4-3 illustrates the default settings in brackets and shows entering global parameters.
Example 4-3 Default Settings and Global Parameters
Configuring global parameters: Enter host name [Router]: RouterA The enable secret is a password used to protect access to privileged EC and configuration modes. This password, after entered, becomes encrypted in the configuration. Enter enable secret: Cisco1 The enable password is used when you do not specify an enable secret password, with some older software versions, and some boot images. Enter enable password: SanFran3 The virtual terminal password is used to protect access to the router over a network interface. Enter virtual terminal password: Sanj 0se Configure SNMP Network Management? [no]:
Continuing through the setup dialog, you are prompted for additional global parameters. Enter the global parameters at the prompts, using the configuration values that were determined for your router. The example shows the prompts for routing protocols as they appear during setup.
If you enter yes at a prompt to indicate that you want to configure a protocol, additional subordinate prompts appear about that protocol. Example 4-4 illustrates this feature.
Example 4-4 Additional Configuration Prompts
Configure IP? [yes]: Configure RIP routing? [yes]: no Configure CLNS? [no]: Configure bridging? [no]:
Continuing through the setup dialog, you are prompted for parameters for each installed interface. Use the configuration values that were determined for the interface to enter the proper parameters at the prompts. Example 4-5 illustrates the configuration of interface FastEthernet 0/0.
Example 4-5 Configuring Interface FastEthernet 0/0
Configuring interface parameters: Do you want to configure FastEthernet0/0 interface? [yes]: Use the 100 Base-TX (RJ-45) connector? [yes]: Operate in full-duplex mode? [no]: Configure IP on this interface? [yes]: IP address for this interface: 1 0. 2. 2. 1 1 Subnet mask for this interface [255.0.0.0] : 255. 255. 255. 0 Class A network is 10.0.0.0, 24 subnet bits; mask is /24 Do you want to configure FastEthernet0/1 interface? [yes]: no Do you want to configure Serial0/0/0 interface? [yes]: no Do you want to configure Serial0/0/1 interface? [yes]: no
A newer feature in Cisco IOS is Cisco AutoSecure. Cisco AutoSecure is a Cisco IOS security CLI command feature that is used to disable services most often used to attack routers and networks. You can deploy one of these two modes, depending on your needs:
- Interactive mode: Prompts the user with options to enable and disable services and other security features
- Noninteractive mode: Automatically executes a Cisco AutoSecure command with the recommended Cisco default settings
CAUTION Cisco AutoSecure attempts to ensure maximum security by disabling the services most commonly used by hackers to attack a router. However, some of these services might be needed for successful operation in your network. For this reason, you should not use the Cisco AutoSecure feature until you fully understand its operations and the requirements of your network.
Cisco AutoSecure performs the following functions:
- Disables these global services:
- Finger
- Packet assembler/disassembler (PAD)
- Small servers
- BOOTP servers
- HTTP service
- Identification Service
- Cisco Discovery Protocol
- Network Time Protocol (NTP)
- Source routing
- Enables these global services:
- Password encryption service
- Tuning of scheduler interval and allocation
- TCP synwait time
- TCP keepalive messages
- Security policy database (SPD) configuration
- Internet Control Message Protocol (ICMP) unreachable messages
- Disables these services per interface:
- ICMP
- Proxy Address Resolution Protocol (ARP)
- Directed broadcast
- Maintenance Operation Protocol (MOP) service
- ICMP unreachables
- ICMP mask reply messages
- Provides logging for security, including these functions:
- Enables sequence numbers and timestamp
- Provides a console log
- Sets log buffered size
- Provides an interactive dialogue to configure the logging server IP address
- Secures access to the router, including these functions:
- Checks for a banner and provides the ability to add text for automatic configuration
- Login and password
- Transport input and output
- exec-timeout commands
- Local authentication, authorization, and accounting (AAA)
- Secure Shell (SSH) timeouts and ssh authentication-retries commands
- Enables only SSH and Secure Copy Protocol (SCP) for access and file transfers to and from the router
- Disables Simple Network Management Protocol (SNMP) if not being used
- Secures the forwarding plane, including these functions:
- Enables Cisco Express Forwarding or distributed Cisco Express Forwarding on the router, when available
- Antispoofing
- Blocks all Internet Assigned Numbers Authority (IANA) reserved IP address blocks
- Blocks private address blocks, if customer desires
- Installs a default route to Null0, if a default route is not being used
- Configures a TCP intercept for a connection timeout, if the TCP intercept feature is available and the user desires
- Starts an interactive configuration for Context-Based Access Control (CBAC) on interfaces facing the Internet, when using a Cisco IOS Firewall image
- Enables NetFlow on software forwarding platforms
When you complete the configuration process for all installed interfaces on the router, the setup command shows the configuration command script that was created, as shown in Example 4-6.
Example 4-6 Configuration Command Script
The following configuration command script was created:
hostname RouterX enable secret 5 $1 $aNMG$kV3mxj lWDRGXmfwj EBNAf1 enable password cisco line vty 0 4 password sanj ose no snmp- server !i p routing no clns routing no bridge 1 !i nterface FastEthernet0/0 media- type 1 00BaseX half- duplex ip address 1 0. 2. 2. 1 1 255. 255. 255. 0 no mop enabled !i nterface FastEthernet0/1 shutdown no ip address !i nterface Serial0/0/0 shutdown no ip address !i nterface Serial0/0/1 shutdown no ip address dialer- list 1 protocol ip permit !e nd [0] Go to the IOS command prompt without saving this config. [1] Return back to the setup without saving this config. [2] Save this configuration to nvram and exit. Enter your selection [2]: 2
The setup command offers the following three choices:
- [0]: Go to the EXEC prompt without saving the created configuration.
- [1]: Go back to the beginning of setup without saving the created configuration.
- [2]: Accept the created configuration, save it to NVRAM, and exit to the EXEC mode.
If you choose [2], the configuration is executed and saved to NVRAM, and the system is ready to use. To modify the configuration, you must reconfigure it manually. The script file generated by the setup command is additive. You can turn features on with the setup command, but not off. In addition, the setup command does not support many of the advanced features of the router or those features that require a more complex configuration.
Logging In to the Cisco Router
When you configure a Cisco router from the CLI on a console or remote terminal, the Cisco IOS Software provides a command interpreter called the EXEC. The EXEC interprets the commands that are entered and carries out the corresponding operations. You must log in to the router before entering an EXEC command.
After you have configured a Cisco router from the setup utility, you can reconfigure it or add to the configuration from the user interface that runs on the router console or auxiliary port. You can also configure a Cisco router using a remote-access application such as SSH.
For security purposes, the EXEC has the following two levels of access to commands:
- User mode: Typical tasks include those that check the router status.
- Privileged mode: Typical tasks include those that change the router configuration.
When you first log in to the router, a user-mode prompt is displayed. EXEC commands available in user mode are a subset of the EXEC commands available in privileged mode. These commands provide a means to display information without changing router configuration settings.
To access the full set of commands, you must enable the privileged mode with the enable command and supply the enable password, if it is configured.
NOTE The enable password is displayed in clear text using the show run command. The secret password is encrypted, so it is not displayed in clear text. If both the enable and secret passwords are configured, the secret password will override the enable password.
The EXEC prompt then displays as a pound sign (#) while in the privileged mode. From the privileged level, you can access global configuration mode and the other specific configuration modes, such as interface, subinterface, line, router, route-map, and several others.
Use the disable command to return to the user EXEC mode from the privileged EXEC mode. Use the exit or logout command to end the current session. Figure 4-25 illustrates the navigation through these modes.
Figure 4-25 User Mode Navigation
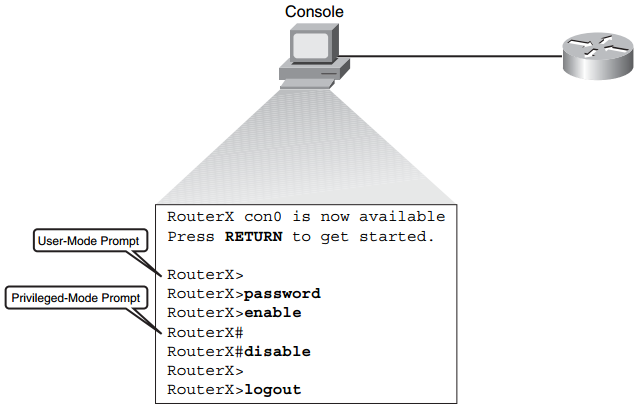
You can enter a question mark (?) at the user-mode prompt or the privileged-mode prompt to display a list of commands available in the current mode. Example 4-7 shows help at the user-mode prompt.
Example 4-7 Getting Help in User Mode
RouterX> ? Exec commands: access-enable Create a temporary Access-List entry access-profile Apply user-profile to interface clear Reset functions connect Open a terminal connection disable Turn off privileged commands disconnect Disconnect an existing network connection enable Turn on privileged commands exit Exit from the EXEC help Description of the interactive help system lat Open a lat connection lock Lock the terminal login Log in as a particular user logout Exit from the EXEC -- More --
NOTE The available commands vary with different Cisco IOS Software versions.
Notice the — More — at the bottom of the sample display. This indicates that multiple screens are available as output. Additional commands follow, and you can perform any of the following tasks:
- Press the Spacebar to display the next available screen.
- Press the Return key (or, on some keyboards, the Enter key) to display the next line.
- Press any other key to return to the prompt.
Enter the enable user-mode command to access privileged EXEC mode. Normally, if an enable password has been configured, you must also enter the enable password before you can access privileged EXEC mode.
Enter the ? command at the privileged-mode prompt to display a list of the available privileged EXEC commands. Example 4-8 shows privileged-mode help.
Example 4-8 Getting Help in Privileged Mode
RouterX# ? Exec commands: access-enable Create a temporary Access-List entry access-profile Apply user-profile to interface access-template Create a temporary Access-List entry bfe For manual emergency modes setting cd Change current directory clear Reset functions clock Manage the system clock configure Enter configuration mode connect Open a terminal connection copy Copy from one file to another debug Debugging functions (see also 'undebug') delete Delete a file dir List files on a filesystem disable Turn off privileged commands disconnect Disconnect an existing network connection enable Turn on privileged commands erase Erase a filesystem exit Exit from the EXEC help Description of the interactive help system -- More --
NOTE The available commands vary with different Cisco IOS Software versions.
Showing the Router Initial Startup Status
After logging in to a Cisco router, the router hardware and software status can be verified by using the following router status commands: show version, show running-config, and show startup-config.
Use the show version EXEC command to display the configuration of the system hardware, the software version, the memory size, and the configuration register setting.
Example 4-9 shows the output from a show version command.
Cisco IOS Software, 2800 Software (C2800NM-ADVIPSERVICESK9-M), Version 12.4(12), RELEASE SOFTWARE (fc1) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2006 by Cisco Systems, Inc. Compiled Fri 17-Nov-06 12:02 by prod_rel_team ROM: System Bootstrap, Version 12.4(13r)T, RELEASE SOFTWARE (fc1) RouterX uptime is 2 days, 21 hours, 15 minutes System returned to ROM by power-on System image file is “flash:c2800nm-advipservicesk9-mz.124-12.bin” This product contains cryptographic features and is subject to United States and local country laws governing import, export, transfer and use. Delivery of Cisco cryptographic products does not imply third-party authority to import, export, distribute or use encryption. Importers, exporters, distributors and users are responsible for compliance with U.S. and local country laws. By using this product you agree to comply with applicable laws and regulations. If you are unable to comply with U.S. and local laws, return this product immediately. A summary of U.S. laws governing Cisco cryptographic products may be found at: http://www.cisco.com/wwl/export/crypto/tool/stqrg.html If you require further assistance please contact us by sending email to [email protected]. Cisco 2811 (revision 53.50) with 249856K/12288K bytes of memory. Processor board ID FTX1107A6BB 2 FastEthernet interfaces 2 Serial(sync/async) interfaces 1 Virtual Private Network (VPN) Module DRAM configuration is 64 bits wide with parity enabled. 239K bytes of non-volatile configuration memory. 62720K bytes of ATA CompactFlash (Read/Write) Configuration register is 0x2102 RouterX#
In the example, the RAM is assigned with 249,856 KB available for main memory and 12,288 KB available for I/O memory (shared by all the interfaces). The I/O memory is used for holding packets while they are in the process of being routed.
The router has two Fast Ethernet interfaces and two serial interfaces. This is useful for confirming that the expected interfaces are recognized at startup and are functioning, from a hardware perspective.
The router has 239 KB used for startup configuration storage in the NVRAM and 62,720 KB of flash storage for the Cisco IOS Software image.