Cisco Network Mgmt Protocol FAQ: Management Communication Patterns
Q1. What are the fundamental interaction patterns between the management agents?
Q2. Assume that you have a network with 1000 devices and 1500 links. Assume that a performance management application is interested in 18 performance parameters per link and 7 performance parameters per device. Assume that with incremental information-retrieval requests, you can retrieve 5 parameters at a time. Someone asks you to build an application that will keep a database of historical information of those parameters, using 15-minute intervals. What rate of management requests and responses must your application support per second? Furthermore, if it takes an average of 5 seconds to receive a response from a device, how many requests must the application be capable of handling in parallel?
Q3. What do you call the capability to apply the same management operation to multiple managed objects simultaneously, using only one management request?
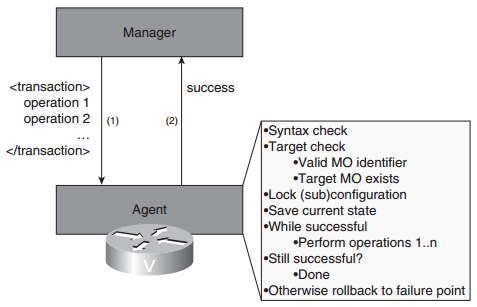
Q4. One important technique that could be supported by devices to facilitate management transactions involves locking the device—that is, allowing a single management session to take management “ownership” of the device and allow no one else to modify the configuration during that time. Such a capability is very powerful, but in what ways does it still fall short of true management transaction support? For bonus points, can you think of new management issues that it introduces?
Q5. One technique that can be used to roll back management transactions involves reverting to an earlier configuration file. Discuss advantages and drawbacks of this technique.
Answer:
Advantages:
- Very effective
- Simple, straightforward application logic and semantics
Drawbacks:
- Performance overhead in persisting configuration file at the beginning of a transaction, as well as reverting to a configuration file in case of rollback, which could make the system too slow to be practical
- Does not provide “locking,” and may result in also rolling back configurations done independently by someone else at the same time during which the transaction took place
Q6. Why can management actions never be subjected to management transactions?
Q7. In network management, what is an alarm?
Q8. Does a TCA have more in common with a configuration-change event or an alarm? Why?
Q9. Is it possible to support polling-based alarm management? If so, why is alarm management generally event based?
Q10. Name three techniques that can be used to make events reliable.
More Resources