Q1. A RADIUS change of authorization enables an authentication server to do which of the following?
a. Escalate an administrative user’s access level within the server’s administration portal
b. Grant context appropriate network access after initial access has previously been granted
c. Gain root-level access of all network devices
d. Take over the world
Q2. Three possible options for change of authorization actions are which of the following?
a. IKEv1, IKEv2, SSL
b. HTTP, FTP, Telnet
c. No COA, Port Bounce, Reauth
d. User mode, privileged mode, configuration mode
Q3. MAC Authentication Bypass is a process by which a device does which of the following?
a. Bypasses all authentication and authorization processes by using a supplicant
b. Authenticates with an X.509 certificate to establish a secure tunnel with the network
c. Authenticates without a 802.1X supplicant on the endpoint by using its MAC address as the RADIUS identity
d. Hides its MAC address from being discovered on the network
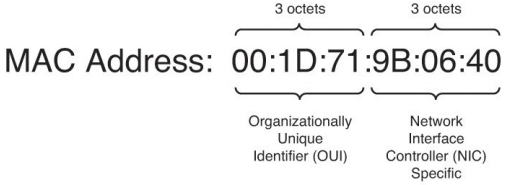
Q4. A MAC address is six octets in length, of which the first three octets are which of the following?
a. A duplicate of the IP address subnet in hexadecimal format
b. Always the same across all network devices
c. Assigned dynamically upon connection to the network
d. An organizationally unique identifier (OUI) that indicates the device’s vendor
e. All F’s—that is, FF:FF:FF
Q5. Which devices often lack an 802.1X supplicant?
a. Printers
b. Laptops
c. Cell phones
d. All of the above
Q6. Prior to MAB, a switchport with a non-802.1x client would be configured without 802.1x. This presented issues because of which of the following?
a. A broadcast storm would be created as the endpoint device was plugged into the interface.
b. A non-802.1x client would still not be able to gain network access.
c. A rogue user could unplug the non-802.1x endpoint and gain unauthorized access to the network.
d. Rebooting the device would cause the switchport to go into error disable.
Q7. Posture assessment can check for which of the following?
a. File conditions including existence, date, and/or version
b. Registry condition, whether a registry entry is or is not present, on Windows-based endpoints
c. Service condition, whether a service is or is not running, on Windows-based endpoints
d. A and B
e. B and C
f. A, B, and C
Q8. When configuring authorization policy based on posture assessment outcome, which of the following values are available for the PostureStatus attribute?
a. Permit, Deny, Drop
b. Compliant, NonCompliant, Unchecked
c. Internet Only, Partial Access, Full Access
d. Compliant, NonCompliant, Unknown
e. AntiVirusNotPresent, AntiVirusNeedsUpdate, AntiVirusCurrent
Q9. To remediate noncompliant endpoints, a redirect ACL must be defined _____ and the web redirection must be destined to ______ portal on the authentication server.
a. as a dACL, remediation
b. on the switch, remediation
c. as a dACL, profiling mitigation
d. on the switch, profiling mitigation
e. as a dACL, authentication DMZ
f. on the switch, authentication DMZ
Q10. A mobile device manager is which of the following?
a. A network administrator responsible for onboarding all mobile devices into the authentication server
b. An application that runs on a mobile device, allowing the user or endpoint to manage the authentication server and other network devices
c. A wireless access point that detects rogue mobile endpoints
d. A software system or service that provides advanced posture assessment for mobile endpoints
More Resources