CCNP Secure FAQ: Introduction to Cisco IOS Site-to-Site Security Solutions
Q1. Which network topology is in use when two sites interconnect using a secure VPN using point-to-point connectivity?
a. Hub-and-spoke network
b. Partially meshed network
c. Individual point-to-point VPN connection
d. Fully meshed network
e. Star topology network
Q2. Which network topology is in use when one central site is considered a hub and all other sites connect directly to the hub site? Most user traffic flows between their respective spoke networks and the hub, but when necessary, two spoke sites can communicate by the hub network acting as a relay between the spoke networks.
a. Partially meshed network
b. Star topology network
c. Hub-and-spoke network
d. Fully meshed network
e. Individual point-to-point VPN connection
Q3. Which network topology is in use when multiple sites interconnect with each other dependent upon their communication needs? Each site can have multiple connections to other sites, but there is no one site that is more important than another. If connectivity is needed between two sites that does not exist, another direct VPN connection is added to the network topology.
a. Hub-and-spoke network
b. Individual point-to-point VPN connection
c. Star topology network
d. Fully meshed network
e. Partially meshed network
Q4. Which network topology is in use when every network has a direct VPN connection to every other network? This topology provides any-to-any communication and provides the most optimal direct path for network traffic.
a. Fully meshed network
b. Star topology network
c. Partially meshed network
d. Individual point-to-point VPN connection
e. Hub-and-spoke network
Q5. Which of the following VPN technologies uses nontunneled IPsec as its encapsulation mode?
a. Individual IPsec tunnels
b. Cisco Easy VPN
c. Dynamic Multipoint VPN (DMVPN)
d. Group Encrypted Transport (GET) VPN
Q6. Which VPN technology can dynamically and automatically build spoke-to-spoke IPsec tunnels?
a. Individual IPsec tunnels
b. Cisco Easy VPN
c. Dynamic Multipoint VPN (DMVPN)
d. Group Encrypted Transport (GET) VPN
e. None of these answers are correct.
Q7. The Internet Key Exchange (IKE) protocol communicates over which port?
a. UDP 500
b. UDP 50
c. TCP 500
d. ESP 500
e. TCP 443
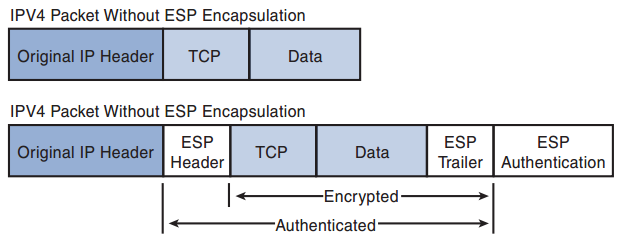
Q8. Which encapsulation mode, when deployed in tunnel mode, provides confidentiality, authenticity, integrity, and antireplay by encapsulating and protecting the entire original IP packet?
a. Authentication Headers (AH)
b. Internet Security Association and Key Management Protocol (ISAKMP)
c. Diffie-Hellman key exchange with Perfect Forward Secrecy (PFS)
d. Encapsulating Security Payload (ESP)
Q9. What should be performed to determine that optimal VPN policies are chosen?
a. Use default settings for everything.
b. Use 802.1X as the encryption algorithm.
c. Perform a formal or informal risk assessment.
d. Install Cisco MARS.
Q10. Most cryptographic systems fail because of what reason?
a. Cryptographic keys are too short
b. Using pre-shared keys over certificate-based authentication
c. Inadequate key management operational processes
d. Weak encryption keys
Q11. Use individual P2P VPN peering only when the number of VPN connections is _____.
Q12. When using any-to-any communications with direct communication paths with low latency and high throughput, a _____ topology is typically the only choice.
Q13. A VPN technology that starts with a hub-and-spoke topology but allows dynamically and automatically built VPNs between spoke sites is _____.
Q14. Cisco GET VPN is considered to be a _____ encapsulation mode and therefore cannot be used on transport networks that cannot route internal VPN addresses.
Q15. _____ provides a framework that provides policy negotiations and key management processes.
Q16. _____ is a set of security protocols that work together to provide security to IP traffic while in transit.
Q17. _____ provides a mixture of security services for IPv4 and IPv6, such as confidentiality, authenticity, and integrity of IP data.
Q18. A VPN technology that supports _____ must be chosen if the transport network does not route internal VPN address spaces.
More Resources