CCNP Secure FAQ: Deploying High Availability in Tunnel-Based IPsec VPNs
Q1. What can be used to mitigate device failure?
a. Single ISP transport networks
b. Multiple ISP transport networks
c. Multiple devices at a site
d. Redundant interfaces on a VPN device
Q2. What can be done to provide high availability when the cost of redundant devices cannot be justified?
a. Use single ISP transport networks
b. Use multiple ISP transport networks
c. Use redundant interfaces
d. Use multiple devices at a site
Q3. When a transport network is not under organizational control, it might be necessary to choose which of the following?
a. A different VPN technology
b. Traditional WAN circuits
c. Point-to-multipoint topology
d. Redundant routers
e. Multiple independent transport networks
Q4. Which interface command can be used to choose the best path when deploying the dynamic routing protocol OSPF?
a. ip ospf cost
b. ip ospf tuning
c. ip ospf path
d. ip ospf router
e. None of these answers are correct.
Q5. In a VTI-based IPsec VPN, traffic that should be protected by the VPN tunnel should be routed how?
a. Carefully
b. Redundantly
c. Dynamically
d. Statically
Q6. What should be used to provide a virtual gateway for clients at the spoke site?
a. IPsec
b. DHCP
c. HSRP
d. AAA
e. None of these answers are correct.
Q7. IPsec shared SAs are enabled with what command?
a. tunnel protection ipsec profile shared
b. ipsec dual SA
c. ip split sa
d. crypto ipsec sa redundant
e. None of these answers are correct.
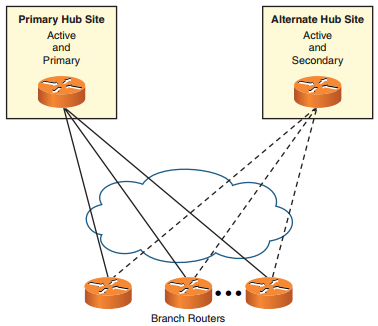
Q8. Which high-availability scenario provides the highest level of redundancy because it mitigates failures of devices, interfaces, access links, and transport networks?
a. Static VTI-based VPN
b. Single DMVPN
c. Dual DMVPN
d. Dual ISPs
Q9. In the case of redundant DMVPNs with multiple GRE tunnels establishing between the same spokes, it is necessary to use _____ for IPsec SAs to establish properly.
Q10. The routing protocol detects both device and path failures using its _____.
Q11. You should design the VPN to meet an organization’s requirements for availability. The design should provide a level of high availability that is commensurate with the _____ of meeting availability needs.
Q12. If _____ are needed, you should either deploy a completely redundant network path that is under the control of local administration or use multiple-transport networks (two ISPs) and connect them to either redundant interfaces or redundant VPN devices.
Q13. _____ will automatically detect peer failures and path failures and then automatically reroute around the failure if redundant paths and devices are in place.
Q14. In a VTI-based IPsec VPN topology, an interior routing protocol will see the VTIbased VPN tunnel as a _____ link.
Q15. An interior routing protocol will view a _____ as either point-to-multipoint (for strict hub-and-spoke DMVPNs) or as a broadcast network (partial or full mesh DMVPNs).
Q16. To provide redundancy for a DMVPN topology, it is recommended to create two separate DMVPN networks by using _____ and one or two spoke routers at remote sites.
Q17. Routing protocols can detect both _____ and _____.
More Resources