CCNA FAQ: Standard Internetworking Models
Q1. What information can DHCP provide to clients? (Choose the 3 best answers.)
A. Clock information
B. IP information
C. DNS information
D. Gateway information
Q2. Which of the protocols are used by email? (Choose the 2 best answers.)
A. POP3
B. SMTP
C. SNMP
D. DHCP
Q3. What takes place when a collision occurs on an ethernet network? (Choose the 3 best answers.)
A. Every device stops transmitting for a short time.
B. A jam signal is sent to notify devices of a collision.
C. A collision signal is sent to notify devices of a collision.
D. A random back-off algorithm starts.
Q4. What is the OUI of the MAC address 01:AB:4D:F2:89:10?
A. 01
B. F2:89:10
C. 01:AB
D. 01:AB:4D
Q5. A MAC address is… (Choose the 2 best answers.)
A. A unique hardware address in a broadcast domain
B. A unique IP address in a broadcast domain
C. Provided by the manufacturer of the NIC
D. Configured manually by the network administrator
Q6. At what layer of the OSI model do you find MAC addresses?
A. Transport
B. Network
C. Data Link
D. Physical
Q7. At what layer of the OSI model do you find sequence numbers?
A. Application
B. Presentation
C. Session
D. Transport
Q8. At what layer of the OSI model do you find IP addresses?
A. Transport
B. Network
C. Data Link
D. Physical
Q9. What kind of PDU is used at the Data Link layer of the OSI model?
A. Bit
B. Segment
C. Packet/Datagram
D. Frame
Q10. What kind of PDU is used at the Network layer of the OSI model?
A. Segment
B. Packet/Datagram
C. Bit
D. Frame
Q11. What kind of PDU is used at the Transport layer of the OSI model?
A. Segment
B. Data
C. Frame
D. Bit
Q12. What is the correct order for data encapsulation?
A. Segment, packet, frame, data, bit
B. Data, segment, packet, frame, bit
C. Bit, frame, packet, segment, data
D. Data, packet, segment, frame, bit
Q13. Routers look at the ________________ when making a routing decision.
A. Destination IP address
B. Source IP address
C. Destination MAC address
D. Source MAC address
Q14. What protocol is assigned to port numbers 20 and 21?
A. DNS
B. Telnet
C. FTP
D. SMTP
Q15. What protocol is assigned to port number 80?
A. SNMP
B. HTTP
C. POP3
D. DHCP
Q16. Which of the following are TCP? (Choose the 2 best answers.)
A. Telnet
B. HTTP
C. TFTP
D. NTP
Q17. Which of the following are UDP? (Choose the 2 best answers.)
A. DHCP
B. SMTP
C. SNMP
D. POP3
Q18. What commands use ICMP? (Choose the 2 best answers.)
A. Show cdp neighbor
B. traceroute
C. Telnet
D. ping
Q19. What protocol maps a known MAC address to an IP address?
A. RARP
B. ARP
C. ICMP
D. Proxy ARP
Q20. What TCP/IP protocol provides terminal emulation to a remote host?
A. HTTP
B. VPN
C. Telnet
D. SNMP
Q21. Briefly list the communication application protocols that are used at the Application layer of the OSI model and what service they provide.
Answer: The following is a list of the protocols utilized at the Application layer of the OSI model and the functionality of each protocol.
- Telnet—Terminal emulation to a remote host
- HTTP—Web-browsing service
- HTTPS—Secure web browsing
- FTP—File transfer
- TFTP—Bare-bones file transfer
- DNS—Name management
- SMTP—Send emails
- POP3—Receive emails
- NFS—File sharing
- NNTP—Usenet newsgroups
- SNMP—Network management
- NTP—Time management
- DHCP—Dynamic host configuration
Q22. Describe how information is passed through the layers of the OSI model.
Q23. Define Positive Acknowledgments and Retransmission (PAR).
Q24. Describe the steps involved in a three-way handshake.
Q25. List the differences between TCP and UDP.
Answer: The following table lists comparisons of the key characteristics of the TCP and UDP protocols.
| TCP | UDP |
| Uses sequenced data transmissions | Does not use sequenced data transmissions |
| Reliable protocol | Unreliable protocol |
| Connection-oriented | Connectionless |
| Expensive to implement | Inexpensive to implement |
| Sends acknowledgments | Does not send acknowledgments |
| Uses windowing flow control | Does not use windowing or flow control |
Q26. List the key functionalities of the Access layer of the Cisco hierarchical model.
Answer: The following list includes the key functionalities of the Access layer of the Cisco hierarchical model:
- Desktop layer
- End-user connectivity
- Virtual LAN (VLAN) workgroup definition
- Continuation of the policies implemented at the distribution layer by using virtual access lists or filter lists
- User access to locally available resources
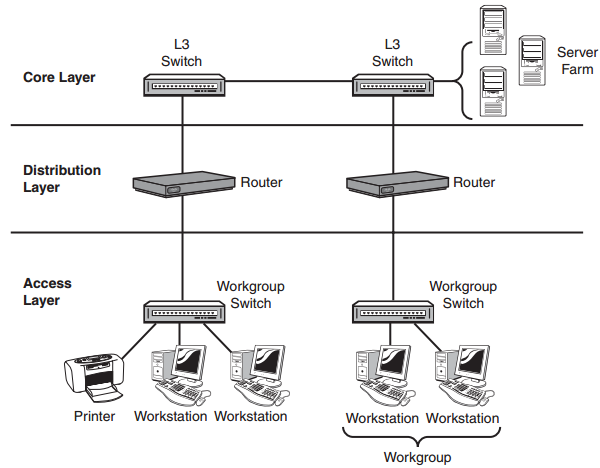
FIGURE: Cisco hierarchical model
Q27. List the key functionalities of the Distribution layer of the Cisco hierarchical model.
Answer: The following list includes the key functionalities of the Distribution layer of the Cisco hierarchical model:
- Control layer
- Middleman between the access and core layers
- Acts as an aggregation point for access layer devices
- Determines how and when to traverse packets to the core layer
- Policy implementation
- Network security
- Routing (best path determination)
- Routing between VLANs
- Filtering
- Access lists
- Packet filtering
- Quality of Service (QoS)
- Network address translation (NAT)
- Route filtering
- WAN access
- Defines broadcast and multicast domains
- Translates between different types of media (i.e. ethernet and token ring)
Q28. List the key functionalities of the Core layer of the Cisco hierarchical model.
Answer: The following list includes the key functionalities of the Core layer of the Cisco hierarchical model:
- Backbone layer
- The Distribution layer manages access to the core.
- High-speed switching
- Reliability
- Redundancy
- Fault tolerance
- Low latency
- Enterprise servers (server farms)
Q29. Which of the following statements is/are true with regard to the device shown below? (Choose all that apply.)

A. It includes one collision domain and one broadcast domain
B. It includes one collision domain and 10 broadcast domains
C. It includes 10 collision domains and one broadcast domain
D. It includes one collision domain and 10 broadcast domains
E. It includes 10 collision domains and 10 broadcast domains
Q30. With respect to the OSI model, which of the following are correct statements about PDUs?
A. A segment contains IP addresses.
B. A packet contains IP addresses.
C. A segment contains MAC addresses.
D. A packet contains MAC addresses.
Q31. You are the Cisco administrator for your company. A new branch office is opening and you are selecting the necessary hardware to support the network. There will be two groups of computers, each organized by department. The Sales group computers will be assigned IP addresses ranging from 192.168.1.2 to 192.168.1.50. The Accounting group will be assigned IP addresses ranging from 10.0.0.2 to 10.0.0.50. What type of device should you select to connect the two groups of computers so that data communication can occur?
A. Hub
B. Switch
C. Router
D. Bridge
Q32. The most effective way to mitigate congestion on a LAN would be to__________________?
A. Upgrade the network cards
B. Change the cabling to CAT 6
C. Replace the hubs with switches
D. Upgrade the CPUs in the routers
Q33. In the work area below draw a line from the OSI model layer to its PDU.


Q34. In the diagram below what procedure is shown?

A. flow control
B. windowing
C. TCP handshake
D. reliable delivery
Review Questions 37
Q36. You need to provide network connectivity to 150 client computers that will reside in the same sub network, and each client computer must be allocated dedicated bandwidth. Which device should you use to accomplish the task?
A. Hub
B. Switch
C. Router
D. Bridge
Q37. In the work area below, drag the OSI model layer on the left to its description on the right.
left list: right list:
Layer Description
Transport Framing
Physical End-to-end connection
Data Link Routing
Network Conversion to bits
Transport End-to-end connection
Physical Conversion to bits
Data Link Framing
Network Routing
The listed layers of the OSI model have the functions shown in the diagram above.
Q38. What feature of TCP is illustrated below?

A. flow control
B. UDP handshake
C. TCP handshake
D. reliable delivery
Q39. Which of the following is an example of a routed protocol?
A. EIGRP
B. IP
C. OSPF
D. BGP
Q40. Which of the following is NOT a function carried out on the Application layer of the OSI model?
A. email
B. data translation and code formatting
C. file transfers
D. client/server processes
Q41. Which of the following layers of the OSI model was later subdivided into two layers?
A. Presentation
B. Transport
C. Data Link
D. Physical
Q13. What feature of TCP is illustrated below?

A. flow control
B. windowing
C. TCP handshake
D. reliable delivery
Q42. An example of a device that operates on the physical layer is a ____________.
A. Hub
B. Switch
C. Router
D. Bridge
Q43. Which of the following is NOT a benefit of using a reference model?
A. divides the network communication process into smaller and simpler components
B. encourages industry standardization
C. enforces consistency across vendors
D. allows various types of network hardware and software to communicate
Q44. Which of the following statements is not true with regard to routers?
A. They forward broadcasts by default
B. They can filter the network based on Network layer information
C. They perform path selection
D. They perform packet switching
Q45. Switches break up _______________ domains and routers break up _____________ domains.
A. broadcast, broadcast
B. collision, collision
C. collision, broadcast
D. broadcast, collision
Q46. How many collision domains are present in the diagram below?

A. eight
B. nine
C. ten
D. eleven
Q47. Which of the following layers of the OSI model is not involved in defining how the applications within the end stations will communicate with each other as well as with users?
A. Transport
B. Application
C. Presentation
D. Session
Q48. Which if the following is the ONLY device that operates at all layers of the OSI model?
A. Network host
B. Switch
C. Router
D. Bridge
[mks_button size=”medium” title=”CCNA Frequently Asked Questions” style=”squared” url=”https://www.configrouter.com/cisco-certified-network-associate-faq/” target=”_blank” bg_color=”#000000″ txt_color=”#FFFFFF” icon=”” icon_type=”” nofollow=”0″] [mks_button size=”medium” title=”CCNA Exam Questions with Explanation” style=”squared” url=”https://www.configrouter.com/ccna-online-training/” target=”_blank” bg_color=”#000000″ txt_color=”#FFFFFF” icon=”” icon_type=”” nofollow=”0″]