CCIE SP MPLS FAQ: Virtual Private Network (VPN) Implementation Options
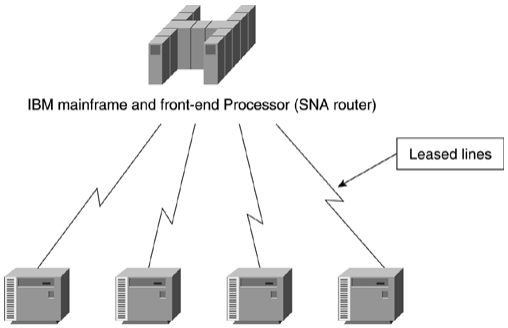
Figure: Typical Computer Network from 15 Years Ago
Q1. Name the two major implementation models that describe Virtual Private
Network (VPN) connectivity.
Q2. Name two possible business problems that can be solved by using a VPN.
Q3. In the peer-to-peer model, describe the difference between a C network and P network.
Q4. Describe two advantages that the peer-to-peer model provides that the Overlay model does not.
Q5. Using the Overlay model, what is the formula to calculate the number of VCs required between a set of client sites if a full-mesh topology is deployed?
Q6. List three technologies that provide IP-based Overlay VPN connectivity.
Q7. Why is the hub-and-spoke topology most often used when the Overlay model is deployed?
More Resources